Intune
How to Set Up Windows LAPS with Microsoft Intune
Topics: Intune
Have you ever made a mistake on a device and needed to get into the local administrator account to recover it? Or have you encountered an environment where all the local administrator accounts shared the same credentials? Well, look no further: Windows Local Administrator Password Solution (LAPS) has arrived to help improve those scenarios to better secure and manage those local administrator accounts. Let us dive in and learn more about Windows LAPS and how to manage it with Microsoft Intune.
What is Windows Local Administrator Password Solution?
Windows Local Administrator Password Solution (LAPS) is a feature in Windows that helps manage and back up the password of a local administrator account on your Microsoft Entra ID joined devices or Windows Server Active Directory-joined devices.
Read our introduction to Windows LAPS here. You can also find our Microsoft LAPS overview here, the original LAPS solution.
Note: We also have a video walk through of this setup process at the bottom of this blog post.
Benefits of Windows Local Administrator Password Solution?
- Helps protect against pass-the-hash, as well as lateral traversal strikes.
- Helps keep your local administrator credentials unique.
- Allows you to sign in and recover devices that might not be accessible (network issue, etc.)
Prerequisites
Okay, so what do I have to buy for this to work? In this scenario, we are going to use Intune as our MDM solution to push the policy to the devices, so we will at least need to have a basic Intune subscription.
Licenses Required
- Intune subscription – Microsoft Intune Plan 1 at a minimum (You will need this license to deploy a policy to the machine)
- Active Directory subscription – Azure Active Directory is free, and you can use all the features of LAPS with Microsoft Entra ID free.
Tip: To see if your current plan includes the basic Intune subscription, take a look at https://m365maps.com/ created by Aaron Dinnage to help with any of your licensing questions.
Where is Windows LAPS available?
Windows LAPS is available on the following OS platforms:
- Windows 11 22H2 – April 11, 2023, Update and later (Pro, EDU and Enterprise)
- Windows 11 21H2 – April 11, 2023, Update and later (Pro, EDU and Enterprise)
- Windows 10 – April 11, 2023, Update and later (Pro, EDU and Enterprise)
- Windows Server 2022 and Windows Server Core 2022 – April 11, 2023, Update and later
- Windows Server 2019 – April 11, 2023, Update and later
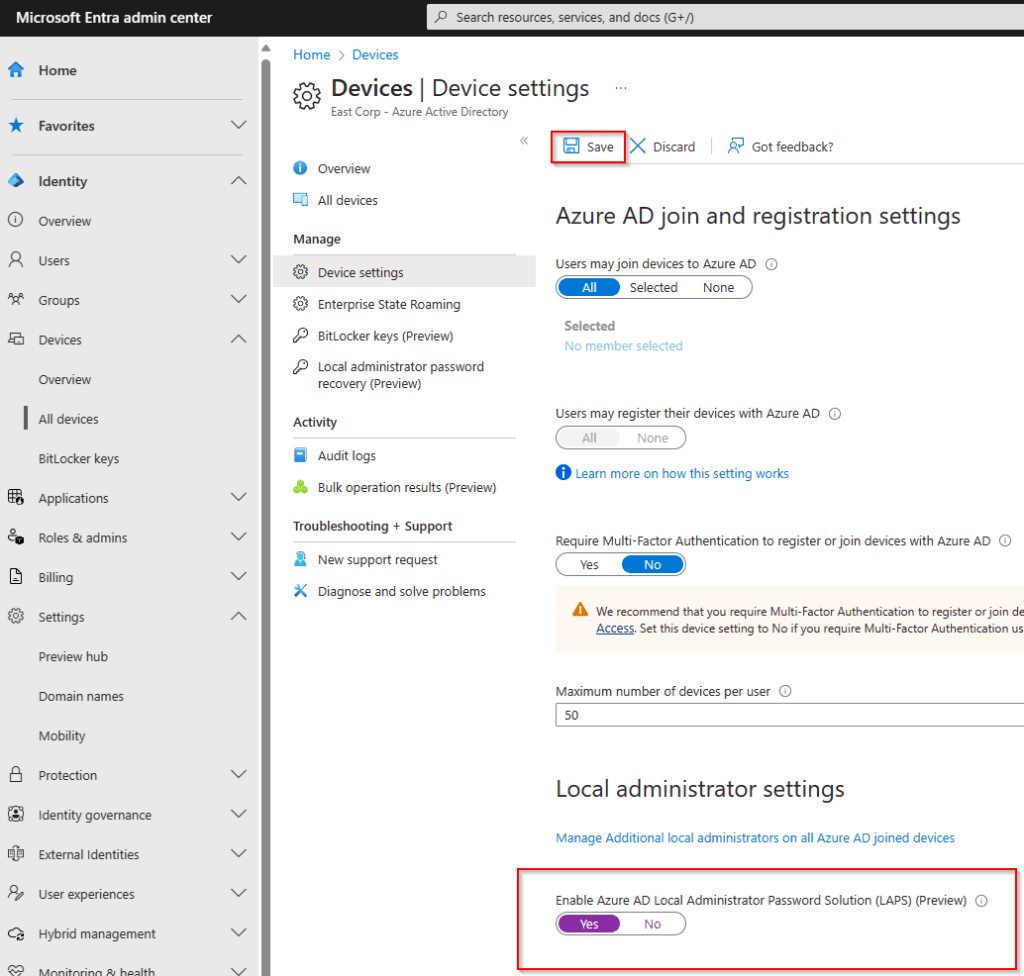
Enable LAPS in Microsoft Entra ID Device Settings
First, you want to make sure you enable Microsoft Entra ID Local Administrator Password Solution (LAPS) (Preview) inside of Microsoft Entra admin center with at least the Cloud Device Administrator role.
- Go to Microsoft Entra admin center.
- In the left-hand menu, click Identity.
- Select the Devices tab > choose All devices.
- Open Device settings.
- Under Local administrator settings, toggle Yes to enable Microsoft Entra ID Local Administrator Password Solution (LAPS) (Preview).
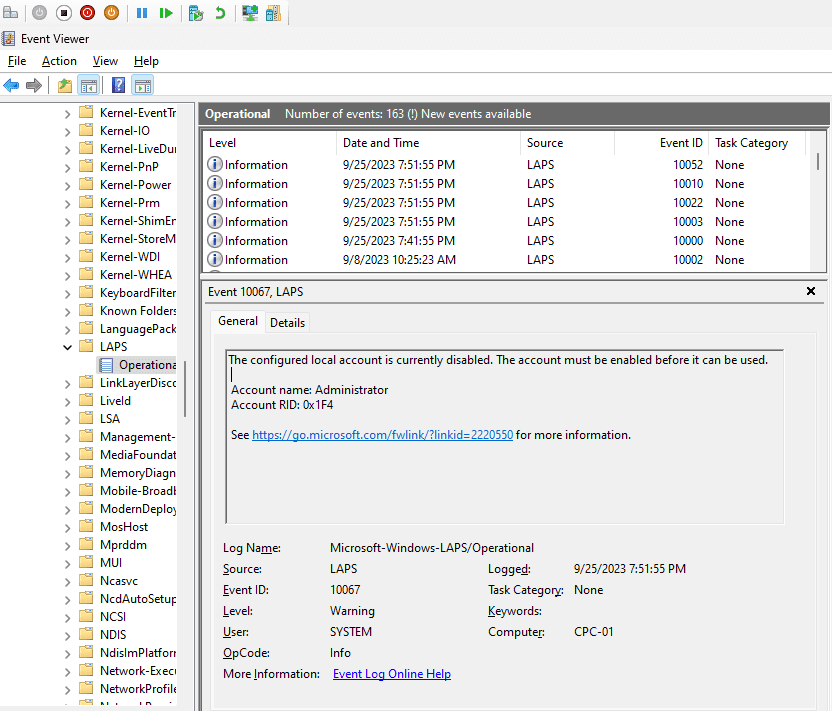
Enable the Local Administrator Account
I was running into trouble when I first tried this, I noticed my local administrator account was disabled as you can see on the event viewer. Which I learned that the local administrator account is disabled by default. So, let’s go enable it, using a Configuration Profile policy in the Intune portal.
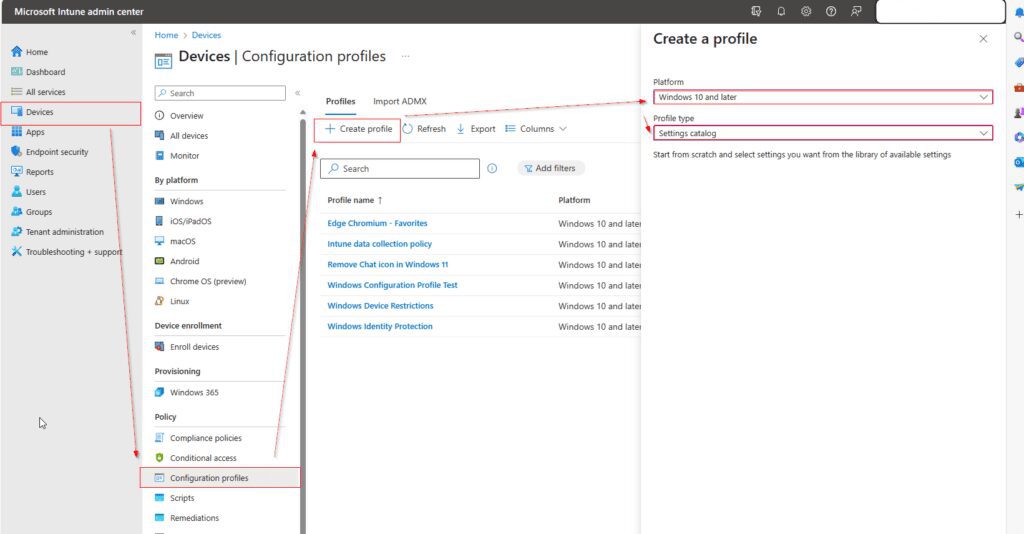
- Enable Local Administrator account using Configuration profiles.
- Go to Microsoft Intune admin center.
- Click Devices.
- Click Configuration profiles.
- Click +Create Profiles.
- Select Windows 10 and later for Platform and Settings catalog for Profile type.
- Click Create.
Add a Name and Description to your Configuration Profile policy > click Next.
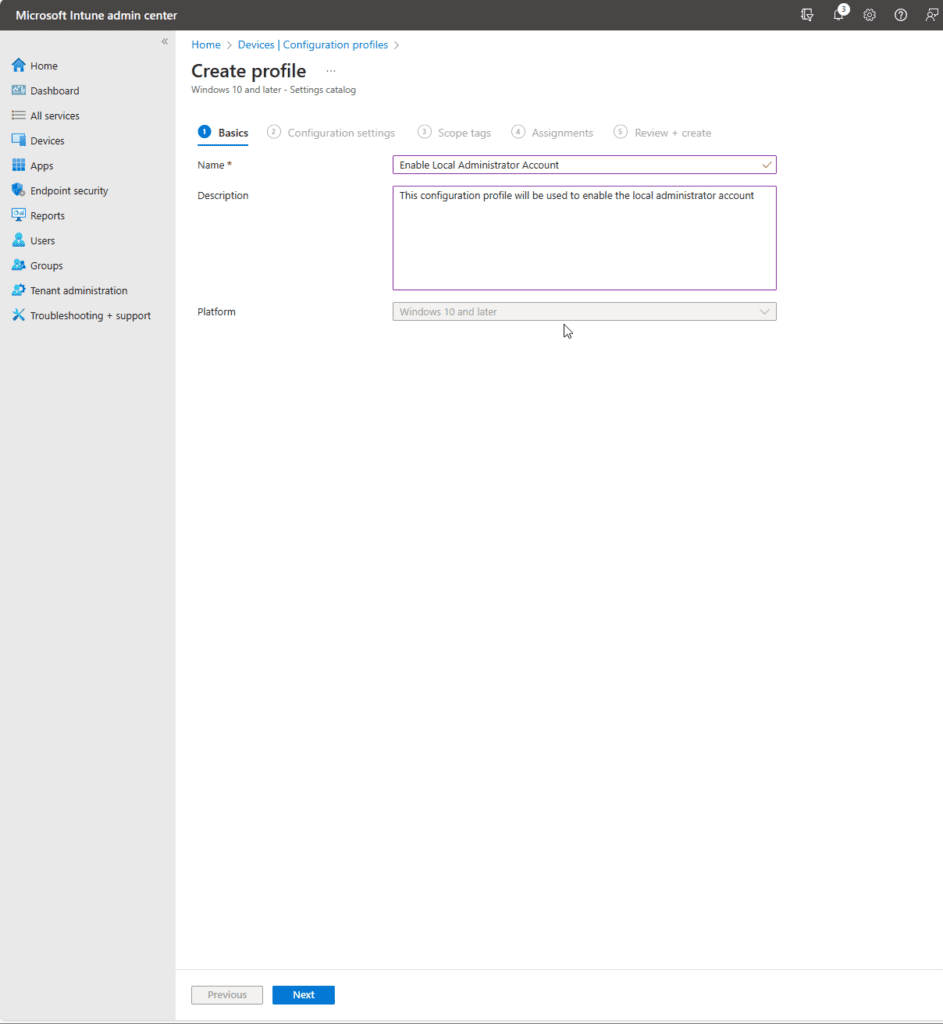
Click on +Add settings.
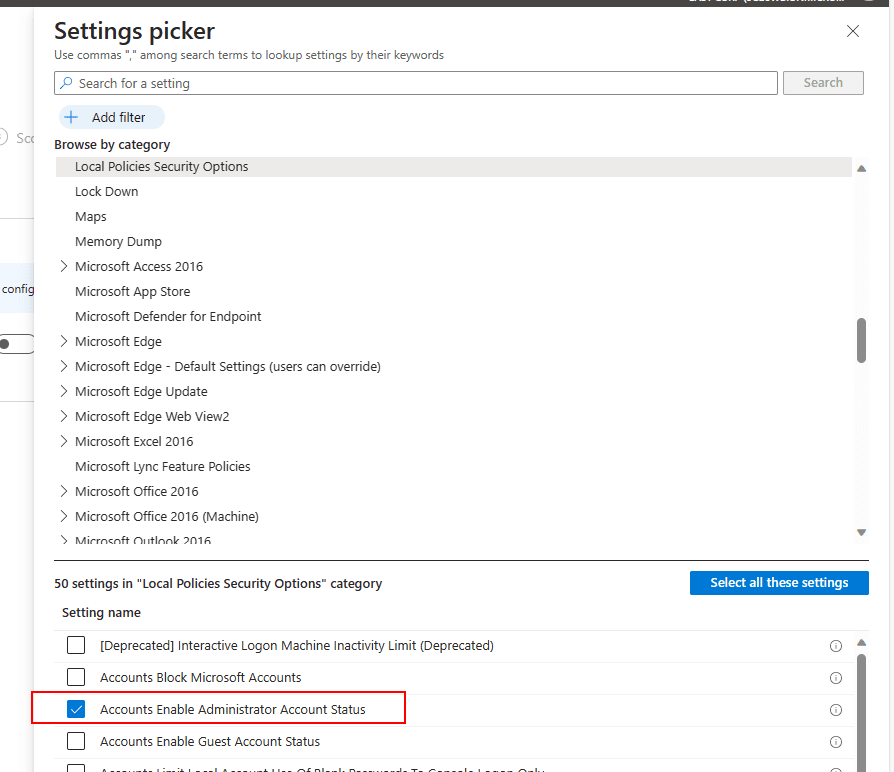
Search for the Local Policies Security Options category > Select Accounts Enabled Administrator Account Status > then Enable it.
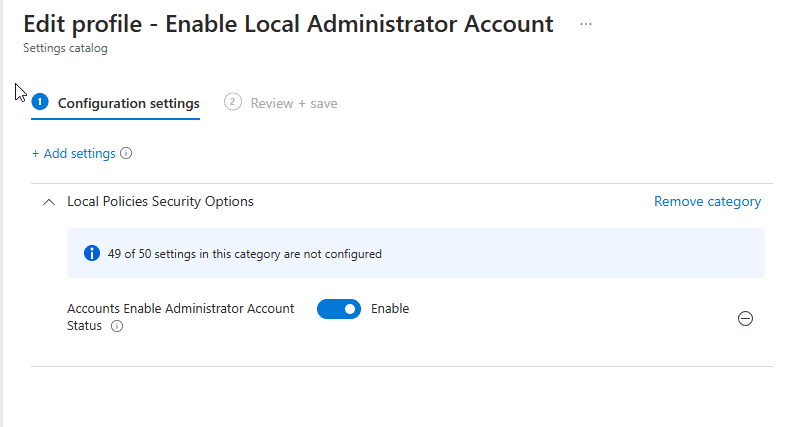
Assign to the Included groups you want. In my case I will + Add all devices > Click Next and Create to deploy policy.
As a wise man once told me, trust but verify. Confirmed the Administrator account is Enabled.
How to Manage Windows LAPS with Intune
Cool! I have all the boxes check-marked. Now how do I manage Windows LAPS with Intune?
First, you want to make sure you at least have the Intune Administrator role to apply these changes inside of your Intune environment. Once you have that set up, let’s get this show on the road.
Let’s create a LAPS Policy inside of Intune
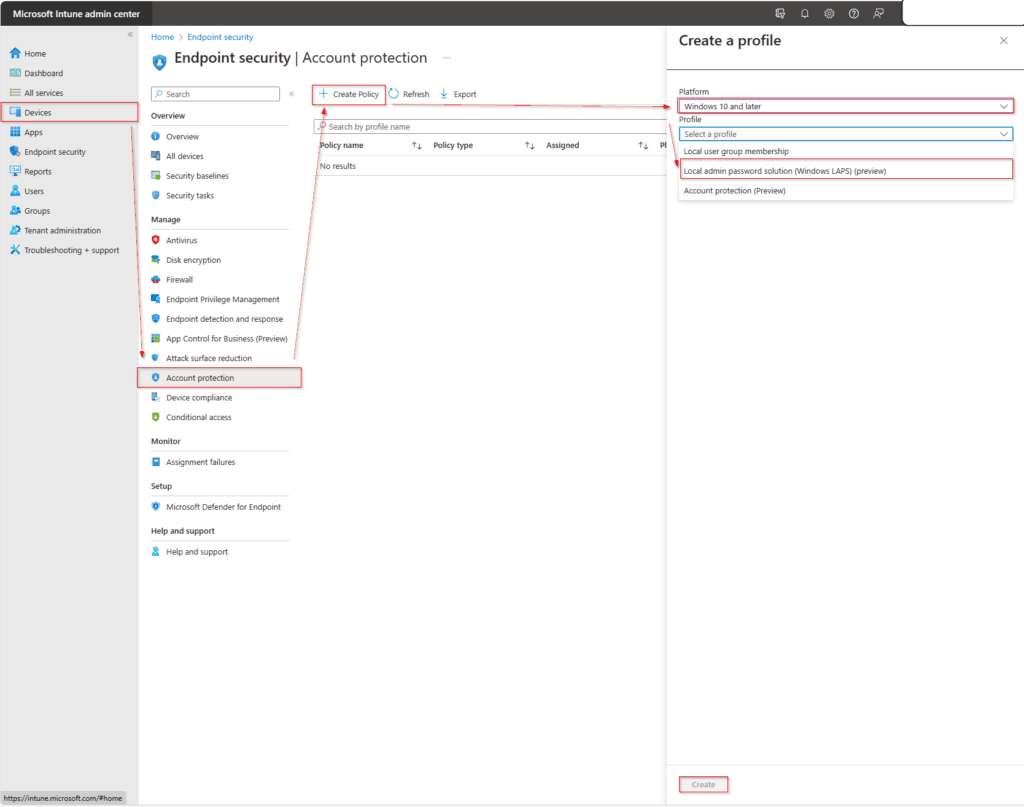
- Go to Microsoft Intune admin center.
- Navigate to Endpoint Security.
- Then Account Protection.
- Click + Create Policy.
- In the Policy, set Windows 10 and later for the platform.
- Select Local admin password solution (Windows LAPS) (preview) for the Profile.
- Click Create.
On the Create Profile page on Basics, you can add a name for the profile. You can also add a description to the profile to give a brief summary and purpose for the policy.
On Configuration settings, we will configure the settings we will apply to our Intune managed devices.
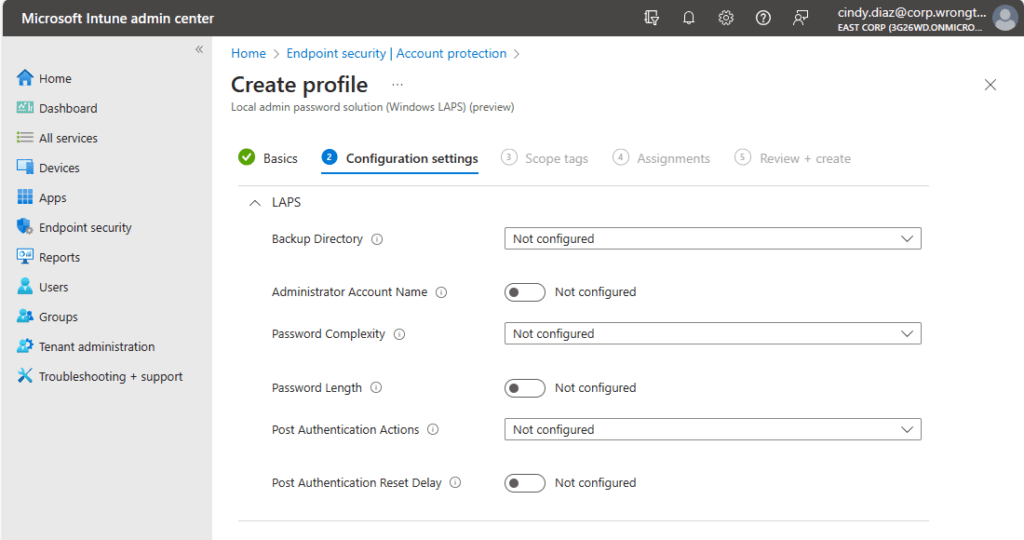
Before we start pushing buttons and configuring our settings, let’s learn a little bit about what this all means on this page.
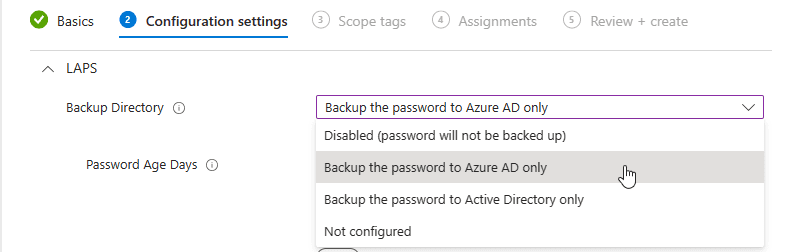
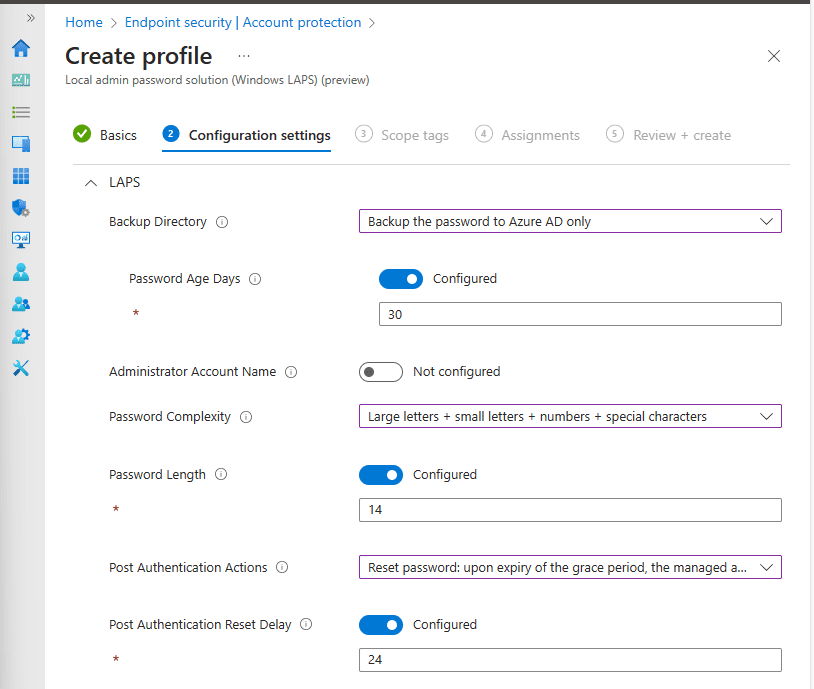
Backup Directory – Here, we are going to tell the machine where to store the password. In my case, I want to back up the password to Microsoft Entra ID only.
💡 You can only pick one choice where to store the password.
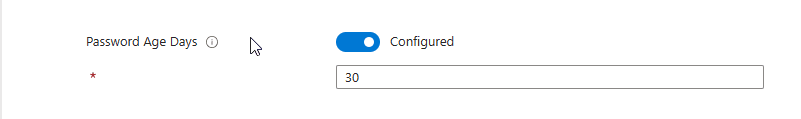
Password Age Days – In this section, we will set the password age of the local administrator before we rotate the password and store the new one in Microsoft Entra ID. In this case, the local administrator password will rotate after 30 days.
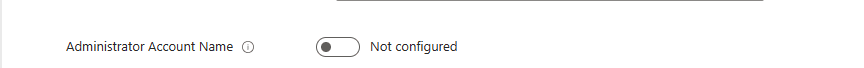
Administrator Account Name – This setting allows you to specify the name of the managed local administrator account. If no name is specified it will use the built-in local administrator account located well-known SID.
Password Complexity – This setting will allow us to control the complexity of the managed local administrator account. In my scenario we want to make it harder for our attackers, so we will set our complexity to use Large letters + small letters + numbers + special characters.
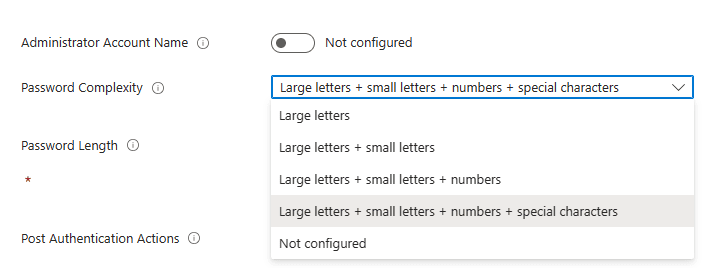
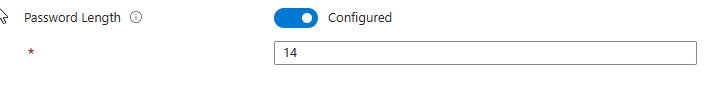
Password Length – This setting will allow us to set the length for the managed local administrator account. Here by default when configured the password length is 14.
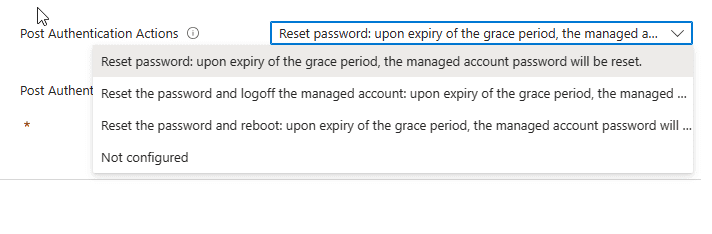
Post Authentications Actions – This setting will be used to configure what happens to the password after someone has authenticated using the local administrator account. This means after the managed local administrator password is used, run the post actions. Here I told the Post Authentication Actions to Reset the password and logoff the managed account; upon expiry of the grace period (24 hours later), the managed account password will be reset.
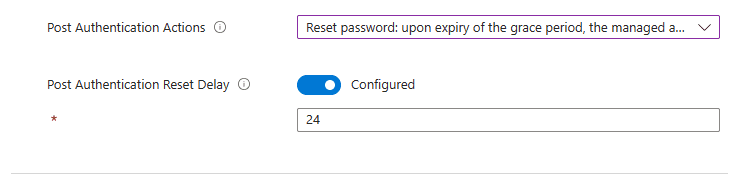
Post Authentication Reset Delay – This setting is used to specify how long to wait after running the Post authentications actions. In my case I gave it a 24-hour grace period, after 24 hours it’s going to run the post authentication action.
Final Configuration Setting for Windows LAPS Policy
We won’t make any changes on the Scope tags page > Click Next.
In the Assignments sections, you can assign this policy to a group, All users or All devices. I will select to apply this policy to All devices.
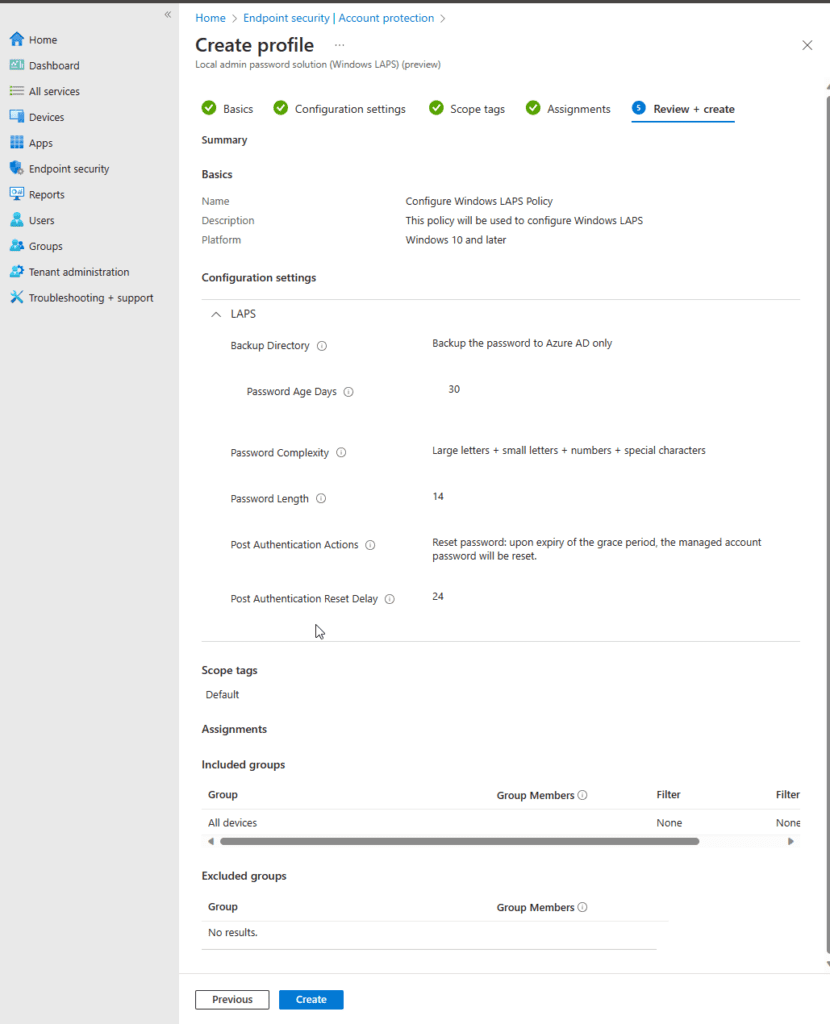
In the Review + create section, double check your policy to make sure it fulfills your need before creating. If it looks good, go ahead and click on Create.
Let’s again trust but verify that our device has received these configurations. Let’s go into our Account Protection policy and check the report. I have an Intune managed device that is called CPC-01 and it looks like it has succeeded.
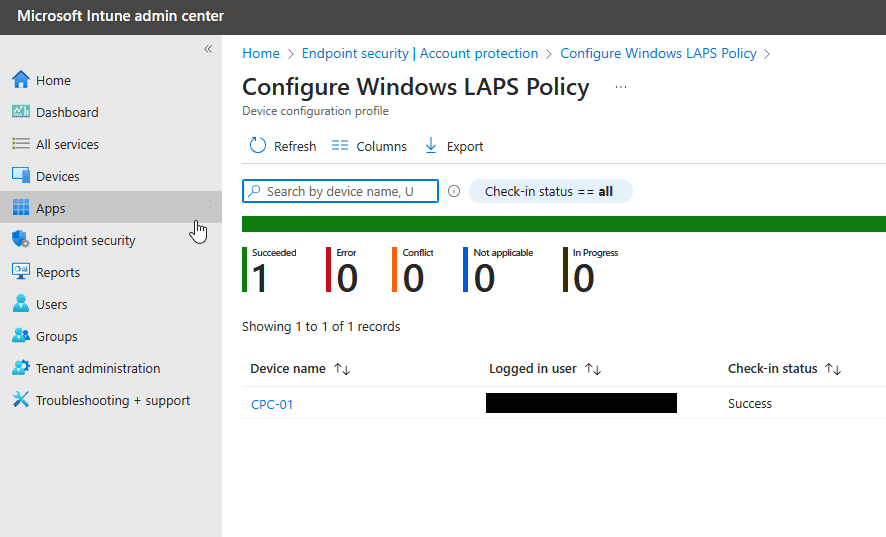
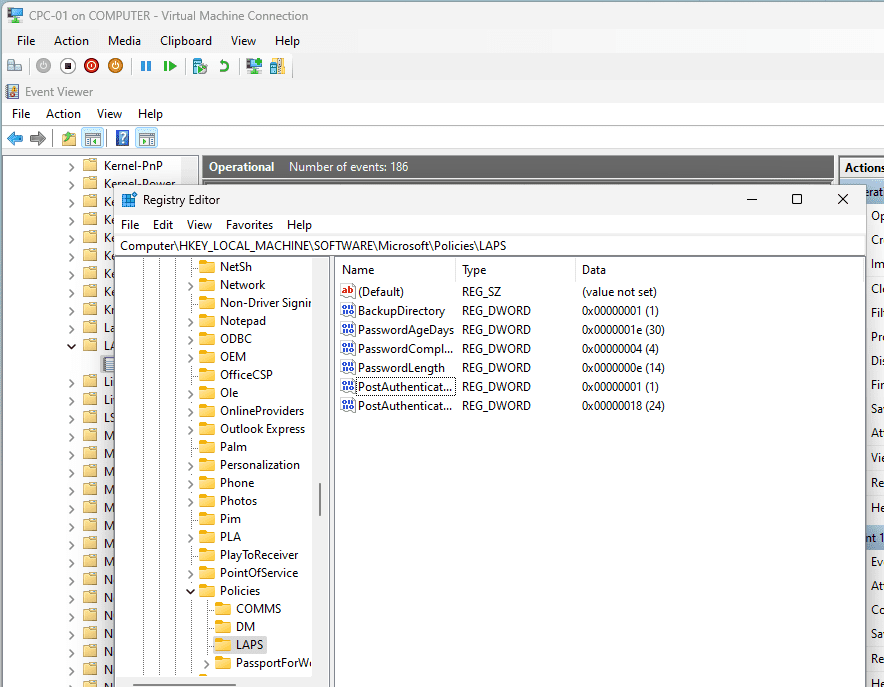
Let’s go a little deeper and go to that device to verify locally that it has received those configurations. We can go to the registry editor and add this path to view what’s been written in the registry.
HKLM\Software\Microsoft\Policies\LAPS
Here we can see information such as our Password Age Days where we set it to 30, Password length where we set it to 14 and our BackupDirectory value of 1 which is Microsoft Entra ID etc.
How to View a Device’s Local Administrator Password
We will try to access the managed Local Administrator password two ways with Microsoft Entra ID and the Microsoft Intune Portal. Make sure to at least have one of the following built-in roles (Global Administrator, Cloud Administrator or Intune Administrator) to access that information.
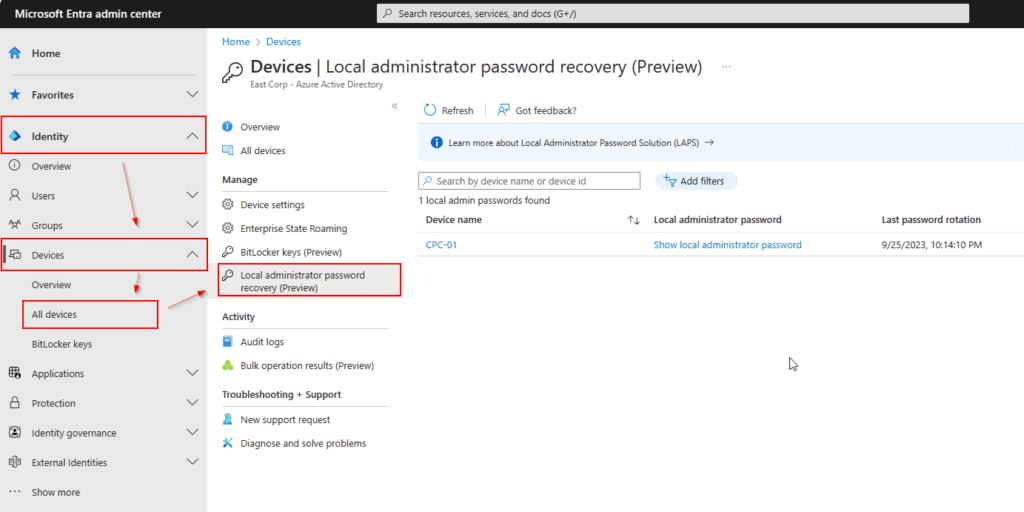
- Go to Microsoft Entra admin center.
- Click Identity.
- Then Devices.
- Then All devices.
- Click on Local Administrator password recovery (Preview).
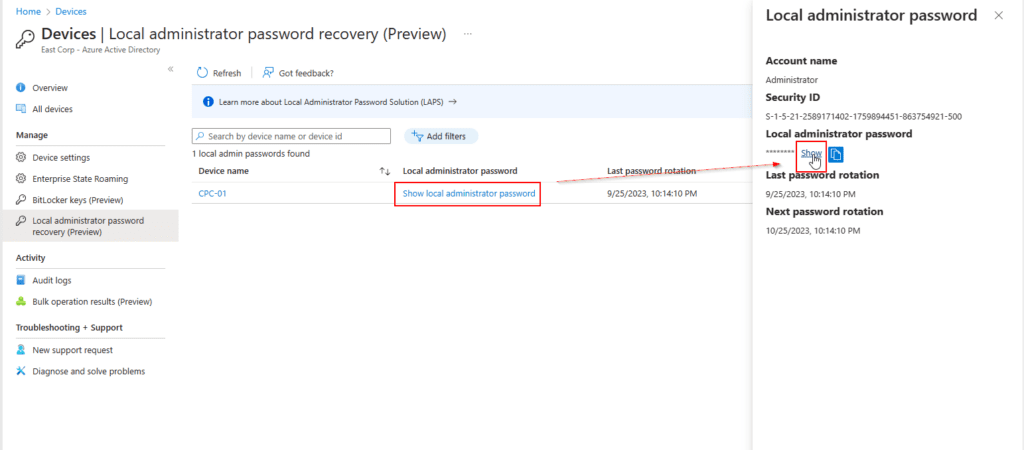
Click Show local administrator password on the device you want to retrieve the local administrator password for > Click on Show to view Local administrator password.
Microsoft Intune admin center
Go to Microsoft Intune admin center > Devices > Windows.
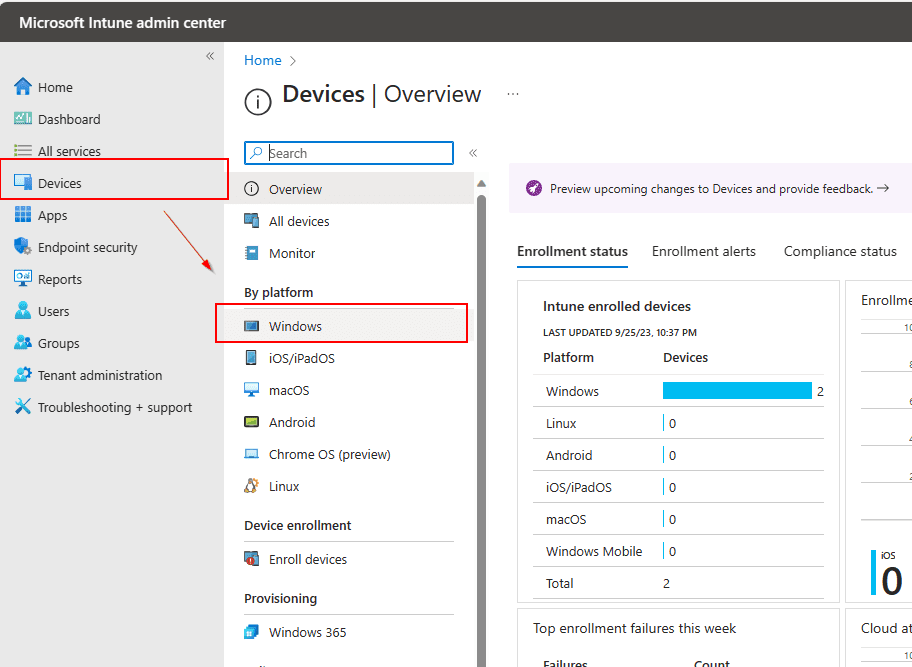
Click on your Windows device you want to retrieve the local administrator password for > select Local admin password.
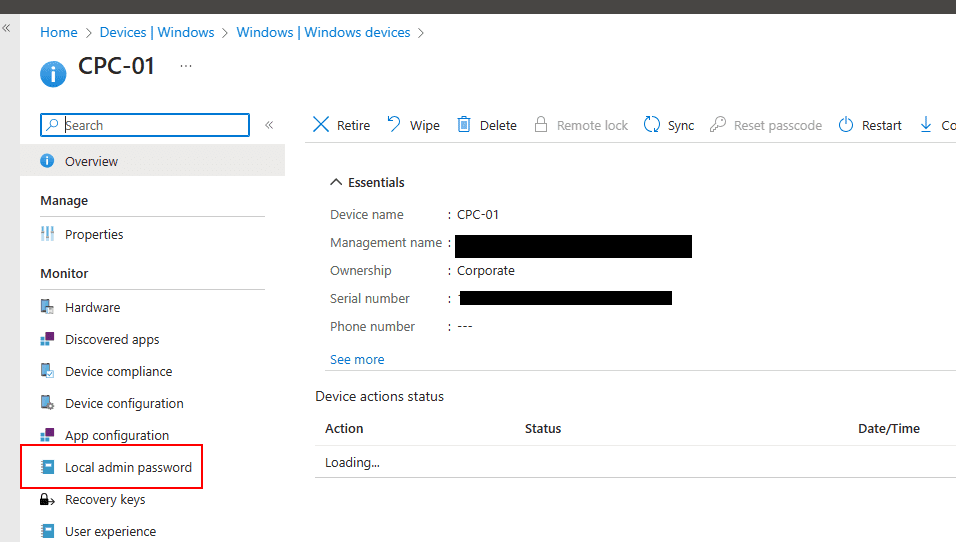
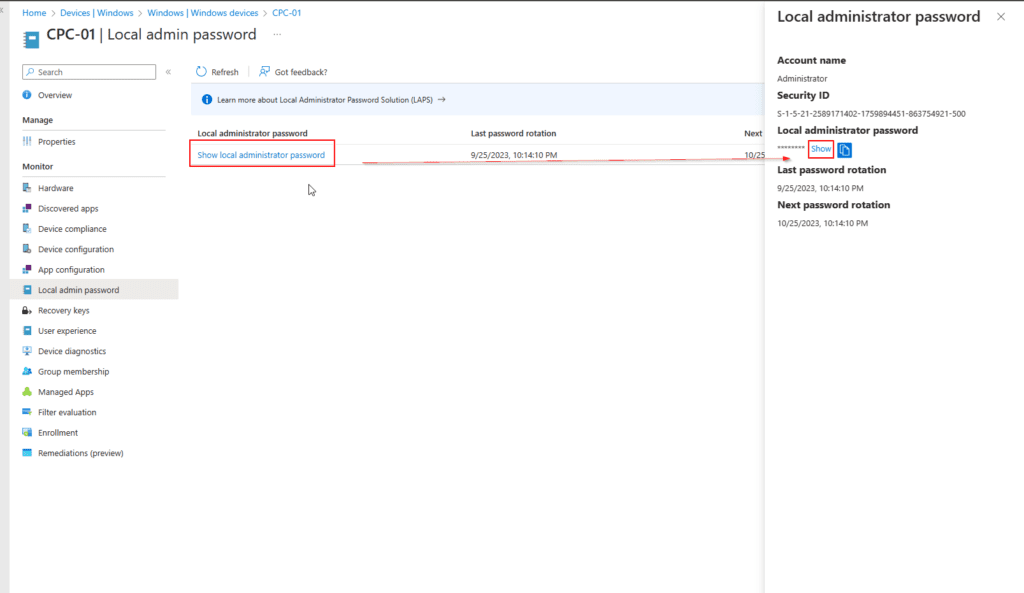
Click on Show local administrator password > click on Show to view Local administrator password.
Let’s put this Local Administrator Password to work on an actual device!
Let’s run PowerShell as an administrator.
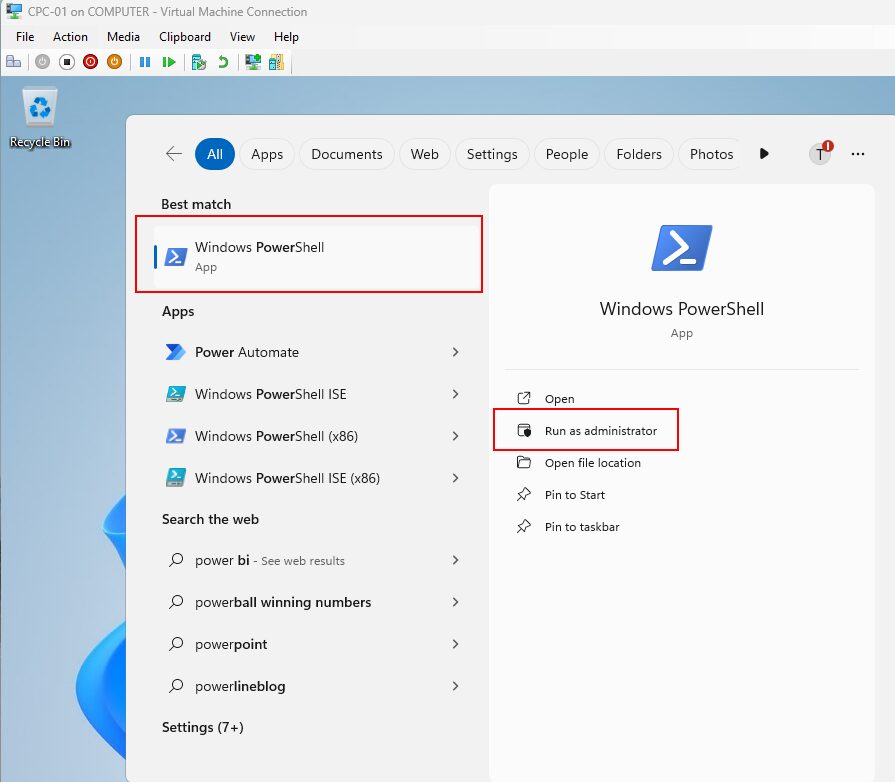
You’ll then view the UAC Prompt asking for administrator credentials > add .Administrator to run with the local administrator account and add the local administrator password retrieved from either Intune or Entra.
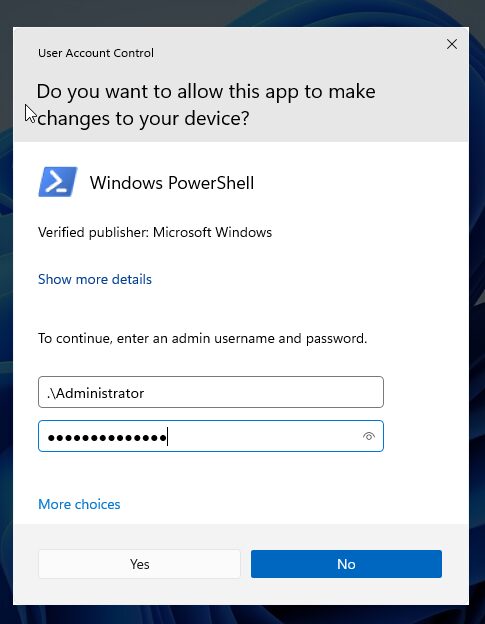
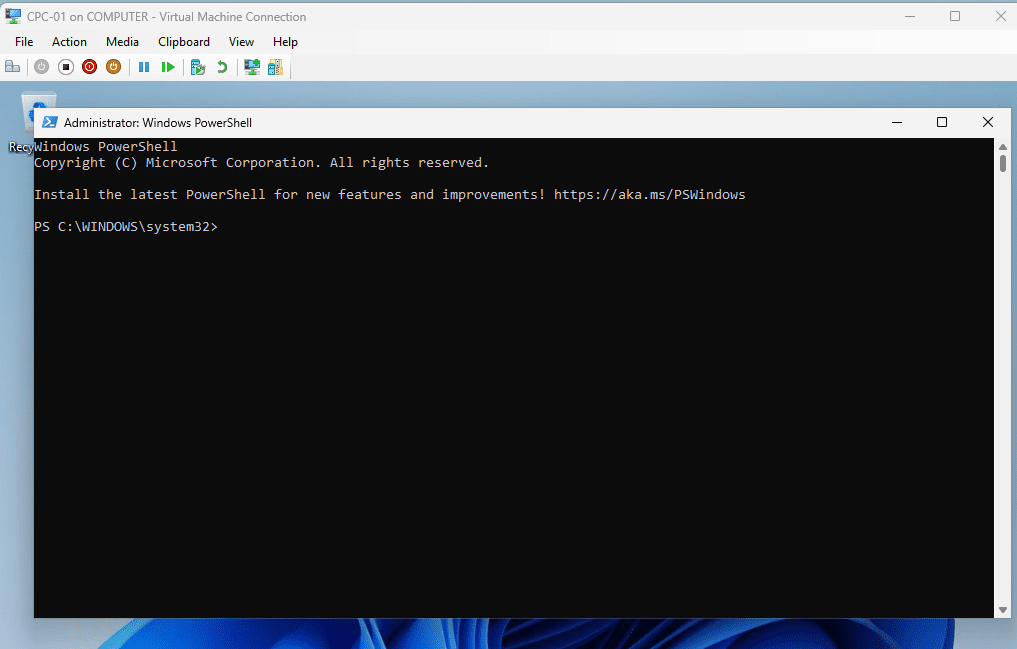
Completed: How to Set Up Windows LAPS with Microsoft Intune
Boom! There we go! The king of the jungle, the administrator!
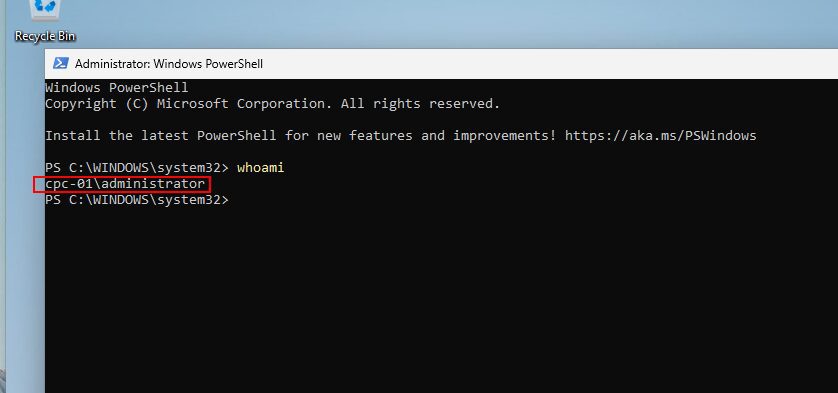
Bonus Tip: Change Windows LAPS password on demand.
- Go to Microsoft Intune admin center.
- Click Devices.
- Then All devices.
- Then click on the device you want to change the LAPS password on.
- Navigate to the 3 dots.
- Select Rotate local admin password.
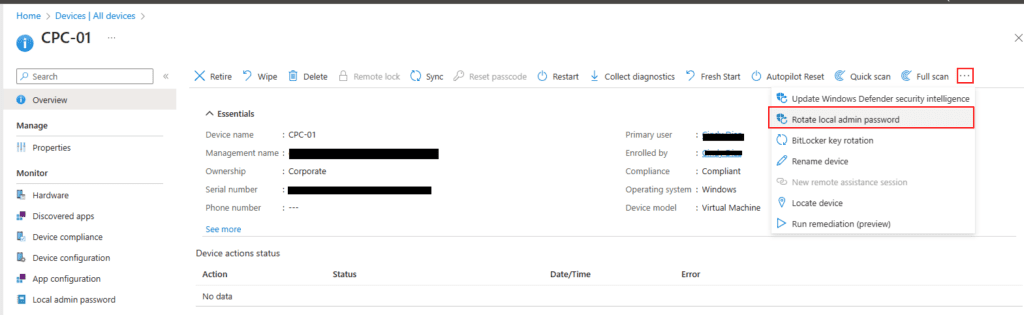
Read the prompt and select Yes (At your own risk).
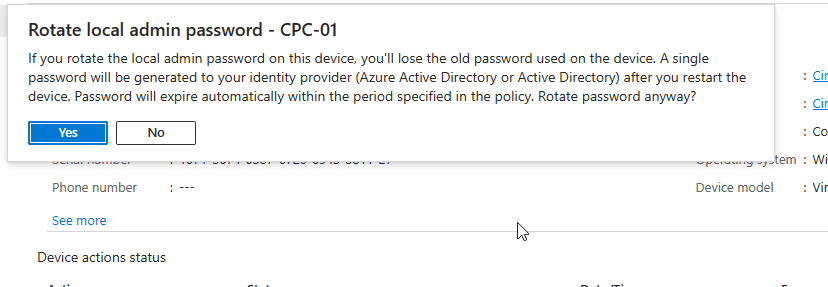
Success!
Conclusion: Windows LAPS with Microsoft Intune
Windows LAPS with Microsoft Intune simplifies the process of securing local administrator accounts while protecting against common attacks. By ensuring each device has its own unique password that rotates automatically, this solution helps reduce the risk of unauthorized access. It also streamlines recovery efforts when mistakes are made. Adopting this approach delivers a practical, cost-effective way to maintain control and safeguard your environment.