One of the features of Right Click Tools that comes up often when we work with customers is the fact that out of the box, Right Click Tools requires Local Admin access on the target computer you are running actions against in order to be successful. When you install without any additional configuration, your Right Click Tools actions are being run as the user who initiates the tool from the console, so that is the user who would need to have Local Administrator on the target computer.
This article is going to talk about three different ways of setting up Right Click Tools Enterprise with the Recast Management Server, and what the Local Admin Requirements are for each.
Default Install
With the default install of Right Click Tools and the Recast Management Server, it is required that the person running the originating ConfigMgr console have Local Admin access to the target computer in order for the actions to complete successfully.
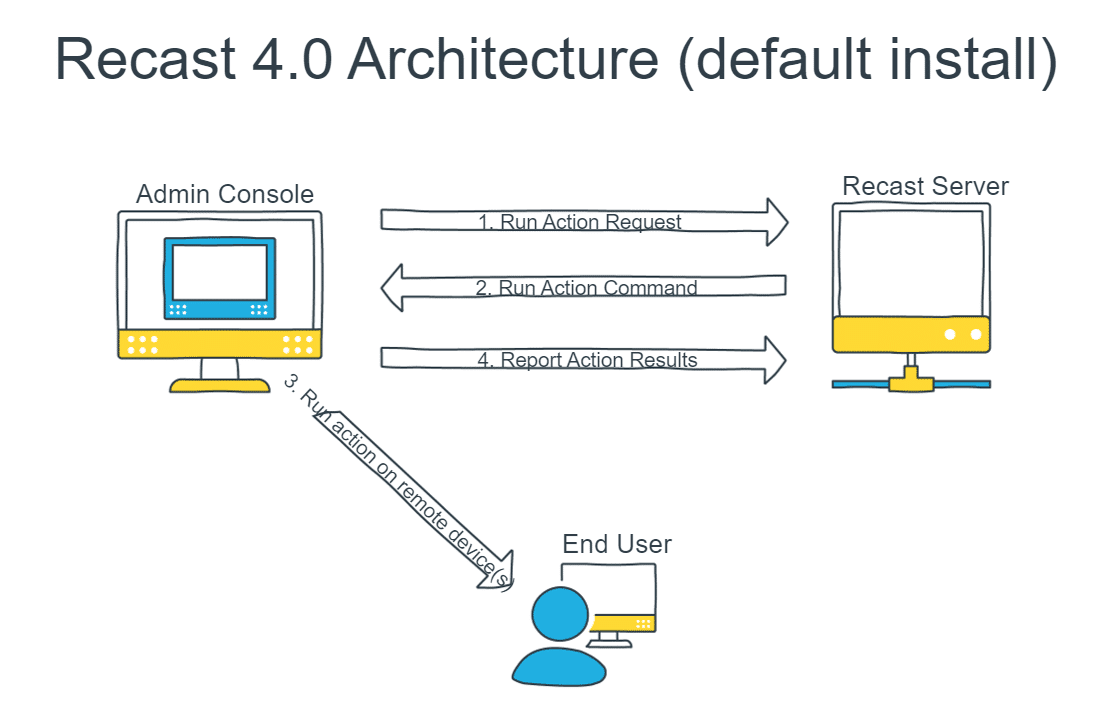
Here’s how the actions are run in a default installation of Recast Management Server (and there’s a diagram of this setup below):
- Actions are initiated from the ConfigMgr Admin console
- The console checks with the Recast Management Server to make sure the user has permission to run the action, and then the action command is given the go ahead on the computer with the ConfigMgr console.
- The action is run from the ConfigMgr console computer to the target computer. Because it is being run in the context of the logged in user, that user must be local admin on the target computer.
- Results are then reported back to the Recast Management Server to be added to the Audit Log.
Limiting the number of Local Administrators with Recast Proxy
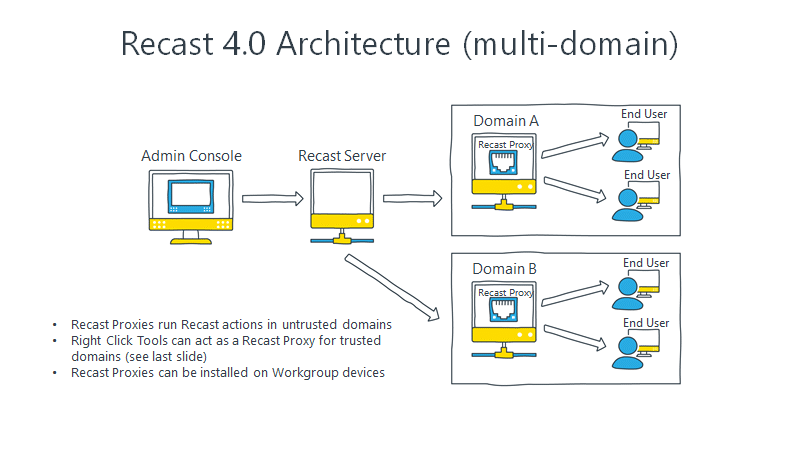
Using a Recast Proxy, you can limit the number of Admin Users in your environment by having all actions run as a single Service Account. A Recast Proxy is a service that runs under a service account and it can be used to run Right Click Tools actions under that Service Account. When running with a Recast Proxy, the steps to running a Right Click Tools action look like this (And another diagram is below):
- Actions are initiated from the ConfigMgr Console
- The Recast Management Server determines if the user has permission to run the action and if the user is allowed it sends theaction on to the Recast Proxy.
- The Recast Proxy runs the action against the target computer with a Service Account. Because it is running in the context ofthe Service Account, the Service Account must be Local Admin on the target computer.
- The proxy reports results back to the Recast Management Server to be added to the audit log
- Results from the action are also returned to the originating ConfigMgr admin console.
Minimize Local Administrators with Recast Agent
If your organization has removed all named Local Administrator accounts or is using LAPS to rotate the password after a predetermined time, you can use the Recast Agent to run many actions without Local Admin access.
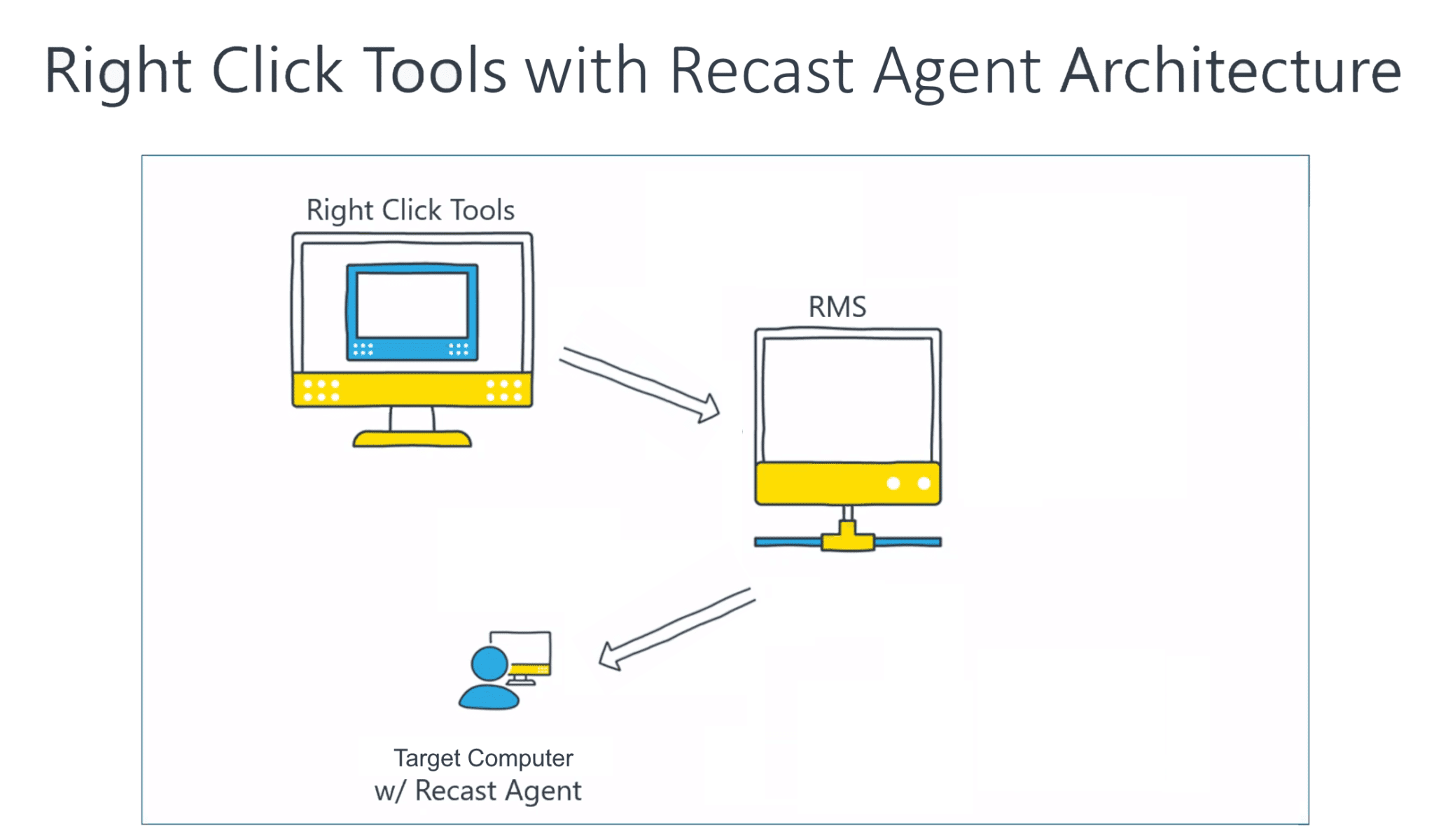
With the Recast Agent running on a target computer, there is no need for users to have Local Administrator access on the target computer for certain actions. The Recast Agent is a service running on a computer that acts as a Right Click Tools client. When the Agent service is running, Right Click Tools actions can execute under the system context, which means that Local Admin rights are not required for those actions.
Note: Not all actions can be performed without Local Admin rights. Actions that require elevated permissions to open something directly on the remote computer, such as remotely accessing File Explorer, CMD, PowerShell, and the Registry, still require administrator permissions on the remote device.
When running actions with the Recast Agent, the steps look like this:
- Actions are initiated from the ConfigMgr Console.
- The Recast Management Server determines if the user has permissions to run the action. If the user is allowed, the action is sent to the Recast Agent running on the target device.
- The Recast Agent runs the action against the device. Because the Agent is running as System, no Local Admin credentials are required for actions that do not inherently require elevated permissions.
- The agent reports results back to the Recast Management Server to be added to the audit log.
- Results from the action are returned back to the originating ConfigMgr admin console.
Final Notes
- Actions requiring interactive sessions that open something directly on a remote device (e.g., Interactive PowerShell Prompt, remote Registry edits and opening C$) still require Local Administrator rights on the target device.
- Other actions, which don’t open something directly on the remote computer, such as Client Actions, Remote Software Center, System Information, and Remote Windows Security will work as normal using the Recast Agent.
- By understanding these capabilities and limitations, you can effectively use the Recast Agent to perform many administrative tasks without needing Local Admin access, while planning accordingly for actions that still require elevated permissions.
Hopefully this helps clarify some of the ways we can changeup the Local Administrator requirements for Right Click Tools.



