In a world where Zero Trust is becoming the industry standard, the last thing you want to do is give out unnecessary permissions. Striking a balance between empowering your employees and reigning in admin access can be challenging. While we often think of these issues in terms of our end users, IT employee accounts should be treated with the same level of scrutiny, providing just enough access to get the job done.
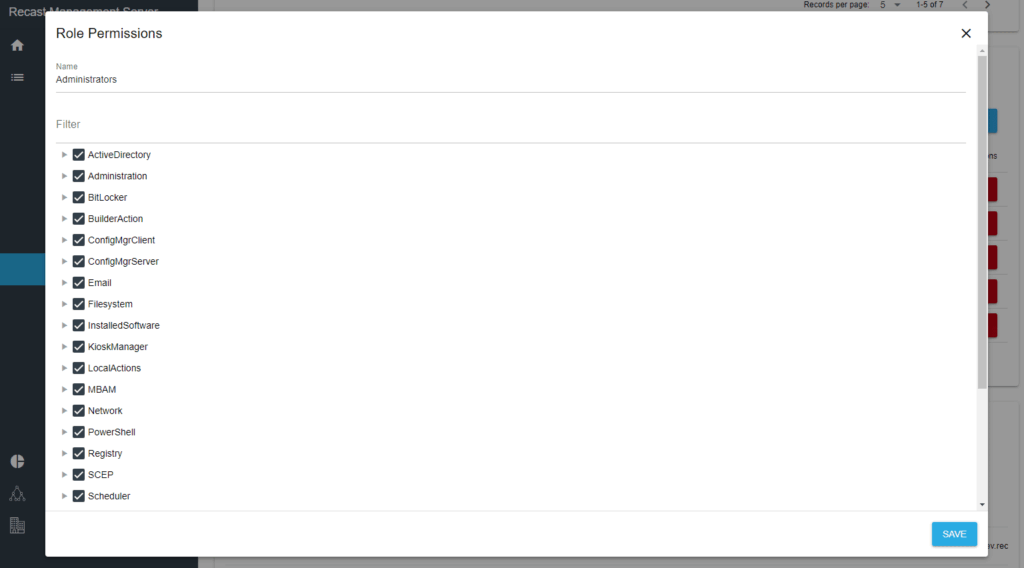
That is why we offer Role-Based Permissions for our Right Click Tools actions. Role-Based Permissions give you the power to control who can take the actions you want, while restricting the actions specific users don’t need. Importantly, you don’t need to set these permissions for each individual. You can set up a role, give only the access you want, and assign that role to the appropriate users or groups.
Why Role-Based Permissions?
Giving out permissions is easy. Reeling them back in can be much more difficult. Using Role-Based Permissions, you empower your IT team to service your environment more effectively. Give your help desk a taste of ConfigMgr to help them grow, while having the peace of mind that they will not overstep their bounds.
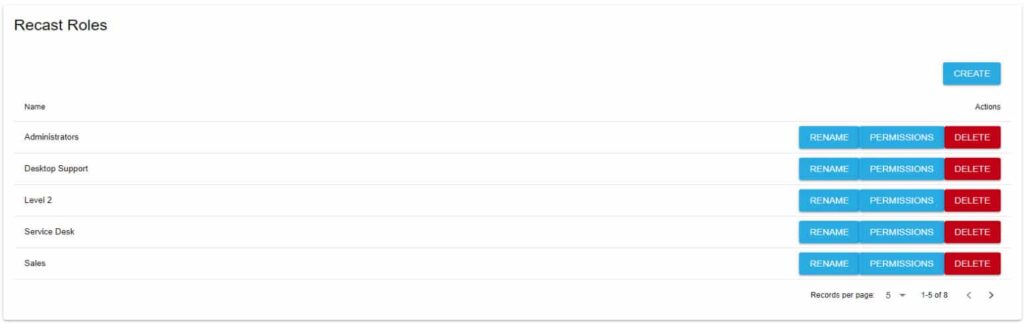
Do you have permissions set in ConfigMgr for certain users to only be able to access specific resources? No problem! The permissions set in the Recast Management Server will respect and adhere to whatever you have set on the ConfigMgr side. If your users are scoped for certain workstations or resources, they will only be able to act on those resources in Right Click Tools as well. You can also set up your own scopes in the RMS to gain further granular control over who can run what actions against what endpoints.
How?
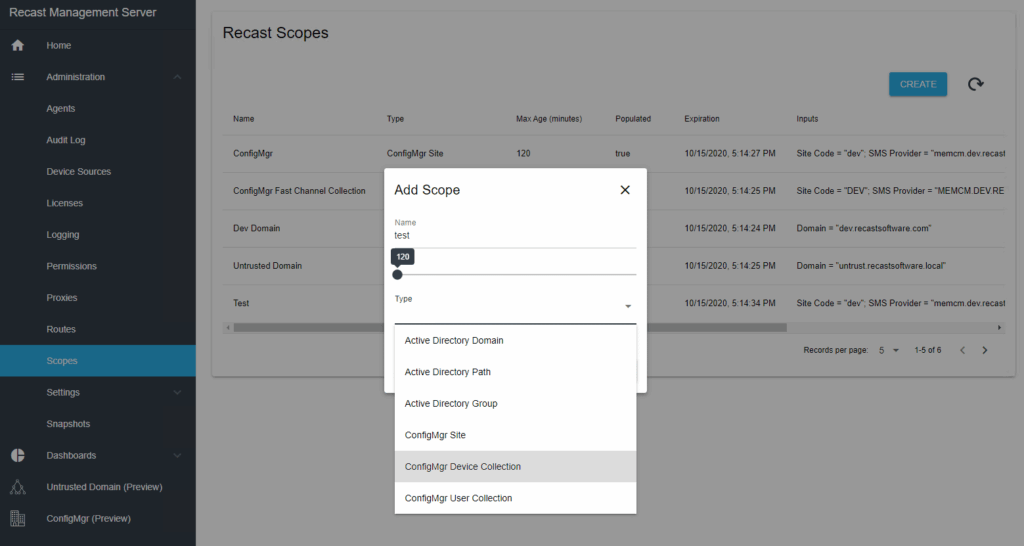
Setting up Role-Based Permissions for Right Click Tools requires an Enterprise license as well as the use of a Recast Management Server (RMS). The RMS can be set up on the same server hosting ConfigMgr. Or, if you prefer, throw it on a brand-new remote server.
Setting up the roles can be as broad or granular as you desire. We even have some role templates to download and import if you want to fast track getting role-based access control up and running. For more information on how to get your RMS with Proxy set up, check out this post. Our support team is always willing to help you out as well, so don’t hesitate to reach out.



