Microsoft LAPS (Local Administrator Password Solution) has been around for several years, and we know many organizations haven’t implemented it yet. The good news is that many have. Thankfully, it’s simple to set up and greatly reduces a commonly exploited attack vector.
LAPS mitigates the risk of lateral escalation that results when customers use the same administrative local account and password combination on their computers. – Microsoft
If you’re among those who haven’t set up LAPS yet, see our Overview of Microsoft LAPS post. The post guides you through the setup process. For the rest, day-to-day operational duties take over and urgent issues pile up. Why is that? Who seriously checked LAPS client health once it was set up? Who confirmed it was working on all endpoints? As with any implementation, you need to check up on it from time to time. This shouldn’t be a surprise—you already do this with the ConfigMgr (SCCM) client, monitor client health, and have perhaps even implemented auto-remediation scripts. You probably monitor AV/anti-malware, IDS, and disk encryption—so why not LAPS?
LAPS Dashboard Monitors Health
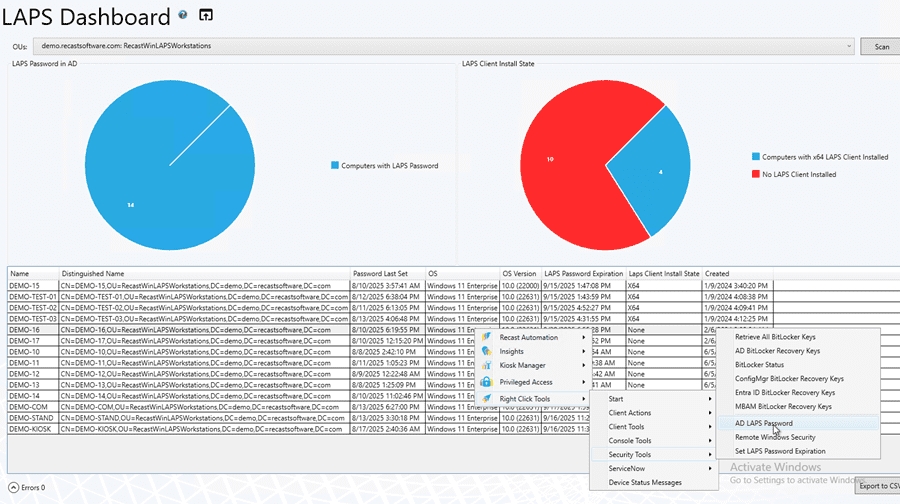
The team at Recast Software created a useful dashboard for monitoring LAPS health. This is included in Right Click Tools Enterprise. Here is an image from our Documentation, showcasing the additional data this feature surfaces:
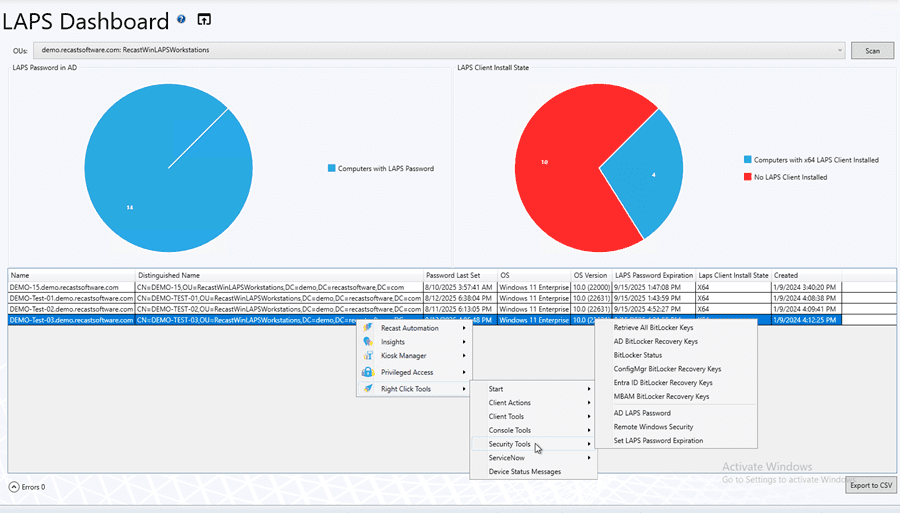
Most of us are in the ConfigMgr Console every day. Having this LAPS dashboard keeps it visible and at the front of our minds, which is highly useful. It only takes a few seconds to pull it up, check the stats, and move on. If an anomaly exists, the team can start looking into it.
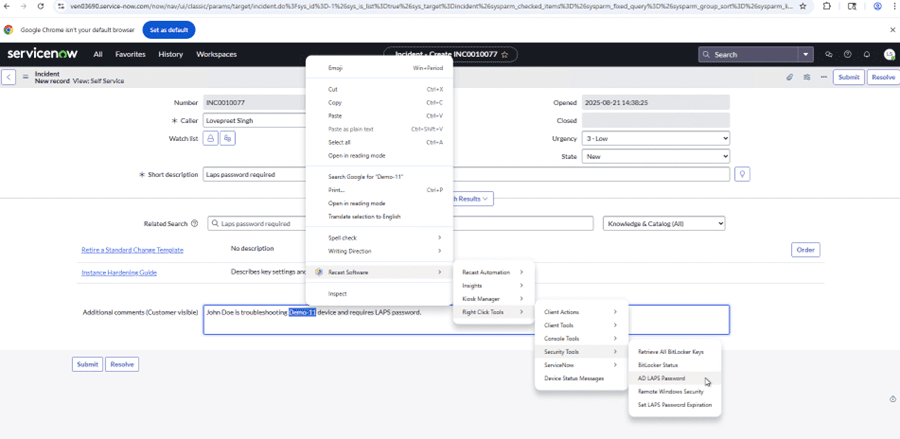
Teams can also look up passwords here. There’s no need to create a special package for Service Desk techs to look up passwords. Most Service Desk techs already have the ConfigMgr console, so we can grant permission for this feature, giving them a powerful way to look up passwords when supporting users. The great news is that even if Service Desk techs don’t have permissions in ConfigMgr, we can use the RCT Browser Extension, which brings Right Click Tools into the systems where they already work. For example, a ticketing system like ServiceNow or Jira. See the screenshot below.
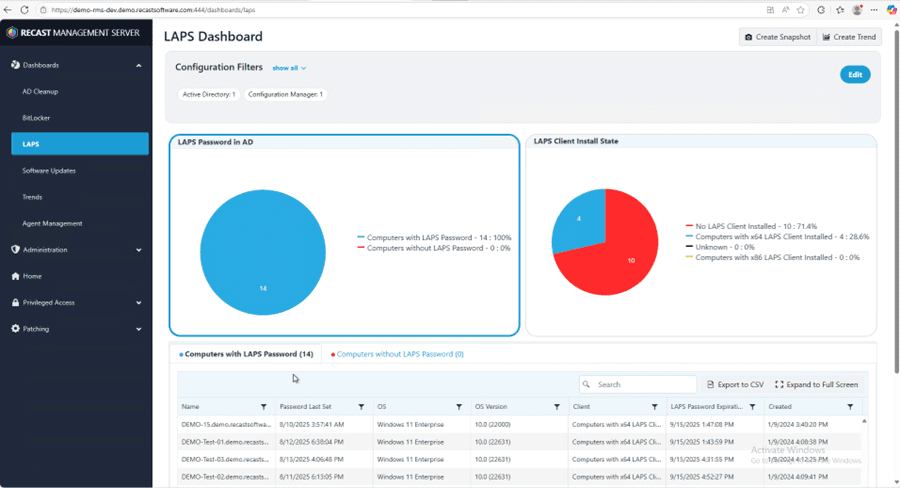
Additionally, we can export LAPS dashboard results to a CSV file. This makes it easy to provide the data that Security and Audit teams need to confirm compliance. For auditors, provide a read-only, intuitive web dashboard that shows LAPS compliance without exposing passwords. That’s exactly what the Recast Management Server LAPS web dashboard offers.
So how do we set this up? First, get a Right Click Tools Enterprise license and set up the Recast Management Server.
What permissions are required to allow my Service Desk to view passwords?
We’ll cover that, building on the last post where we set up LAPS and created AD Groups with different permissions. Assumptions before continuing: Have AD groups created for granting permissions to.
First, in the lab, we have Service Desk Tier 1–3 support roles with different access to the ConfigMgr console. We want all of them to be able to see the dashboards and pull up passwords. In ConfigMgr:
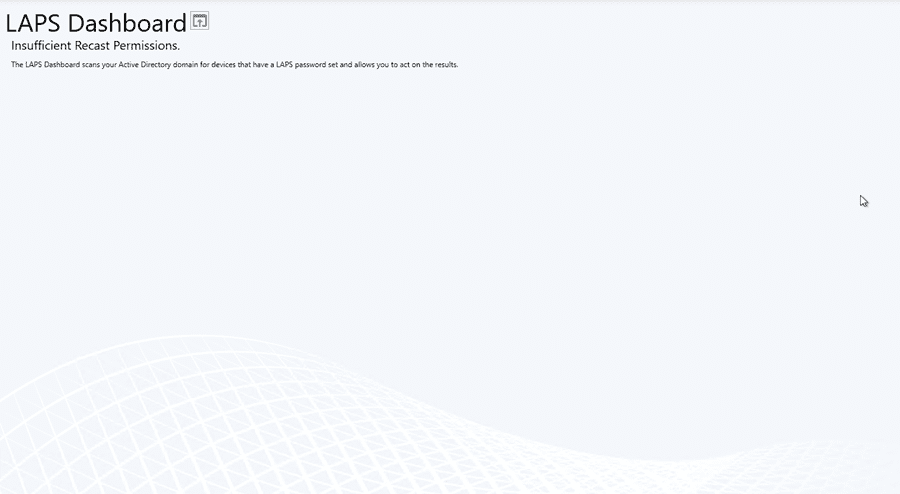
Before adding any permissions, this is what the dashboard looks like for a Tier 1 Service Desk user without the required rights:
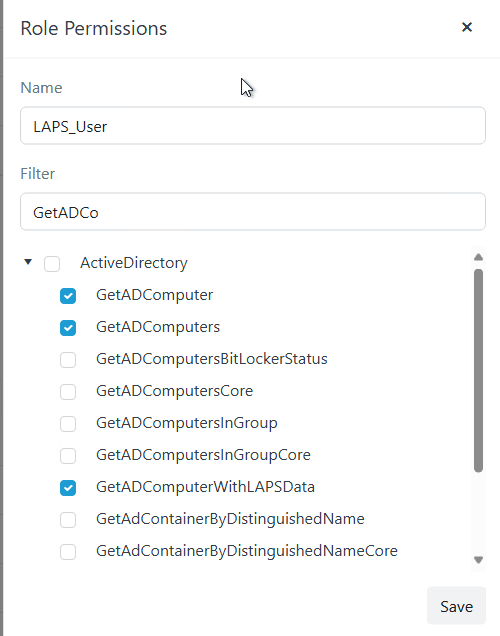
Let’s add some permissions. In Recast Management Server, we created a LAPS role with permissions limited to the LAPS console.
Okay, this looks better.
So what does this look like in the Recast Management Server console? What permissions does our ‘LAPS_User’ role have? See below:
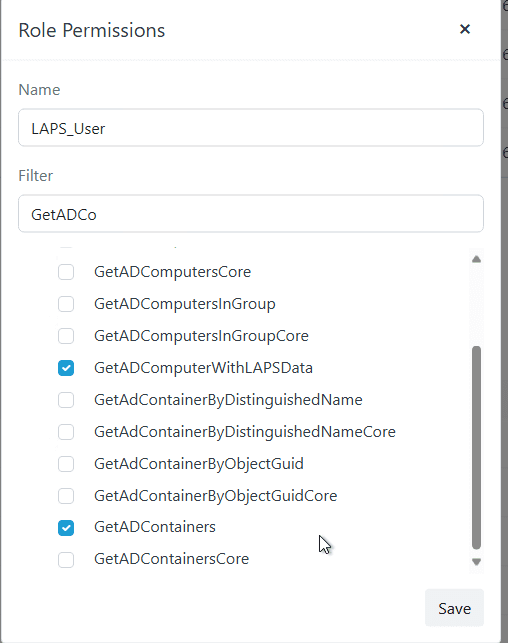
Then we added the ‘LAPS Admins’ AD group and assigned it to the ‘LAPS_User’ role.
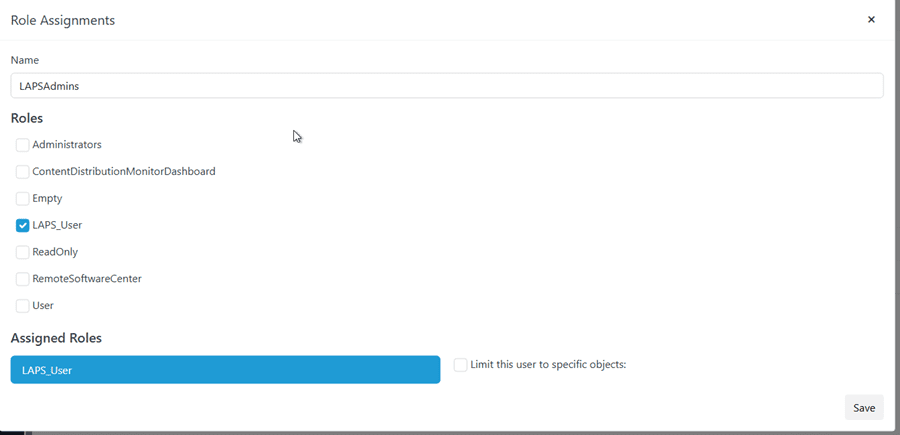
Okay, now we can rest easy knowing our Service Desk has only the permissions they need—no more.
Keep LAPS Healthy with Ongoing Visibility
LAPS closes a critical gap, but it’s only as strong as your visibility. With the LAPS dashboard in Right Click Tools Enterprise and the read-only web view in Recast Management Server, you can confirm compliance, catch issues early, and let Service Desk teams retrieve passwords securely when needed. Set up roles and permissions once, export reports for auditors as required, and make quick health checks part of your routine—so LAPS protection stays consistent across every endpoint.


