Right Click Tools
Recast Proxy Overview
Topics: Right Click Tools
Recast Proxy Overview
Recast Proxy is a feature that enables you to extend your reach of the Right Click Tools into previously untapped areas, such as: Untrusted Domains, WorkGroup Machines, and machines the user [ConfigMgr Console User] doesn’t have rights on directly. This post is an overview, the next post covers deployment in more detail.
Proxy Types
- Device Proxy: Basically an “Agent” that runs as System on the local machine, that allows the Recast Server to directly query / control the Proxy machine.
- Service Account Proxy: Runs the service as the “Service Account” that you specify.
- Right Click Tool Actions that Require a Proxy
- Scheduling Options (Kiosk & Builder). Since the Recast Server is no longer able to run actions directly, these need to be sent to a proxy. If you want to schedule a time for your Kiosk Template or Builder Actions to be scheduled, it has a dependency on a Service Account Proxy being installed in the domain. The Service account requires permissions on both the device you install the Recast Proxy software on and the machines you wish to run the actions on.
- Scoping permissions for Recast users. If you want to limit a user to only run Recast actions on specific devices or AD users, you need to have a Recast Proxy to evaluate the scope. This use case only requires that the proxy have read access to the domain / OU / AD Group, or read access to the ConfigMgr device / user collection that the scope is applicable to. If all user permissions are configured to use the built-in All scope, then a proxy is not required.
Test Scenarios in this Post
- Untrusted Domain
- Work Group Computers (No Domain)
- Any Machine / Any Domain – ConfigMgr Console User doesn’t have permissions on endpoints. [Service Account Mode]
PreReqs: You already have a Recast Management Server Setup and working in your environment. For assistance with that, learn more here. You’ll need to Export the Self-Signed Certificate from the Recast Server**
** If you’re using PKI, and have your PKI infracture already setup and pushed your certs to the Untrusted domain machienes or imported them on the workgroup machines, that will save you a bunch of time, and you can skip importing the self-signed cert that is about to be covered:
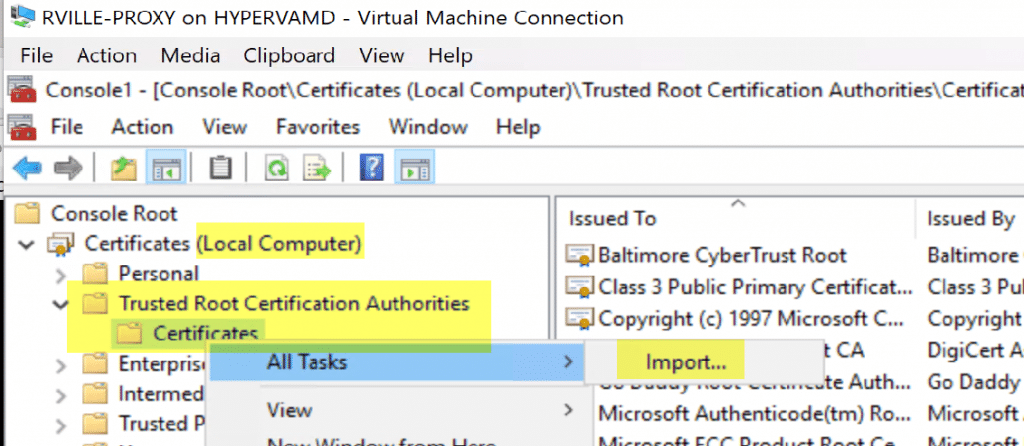
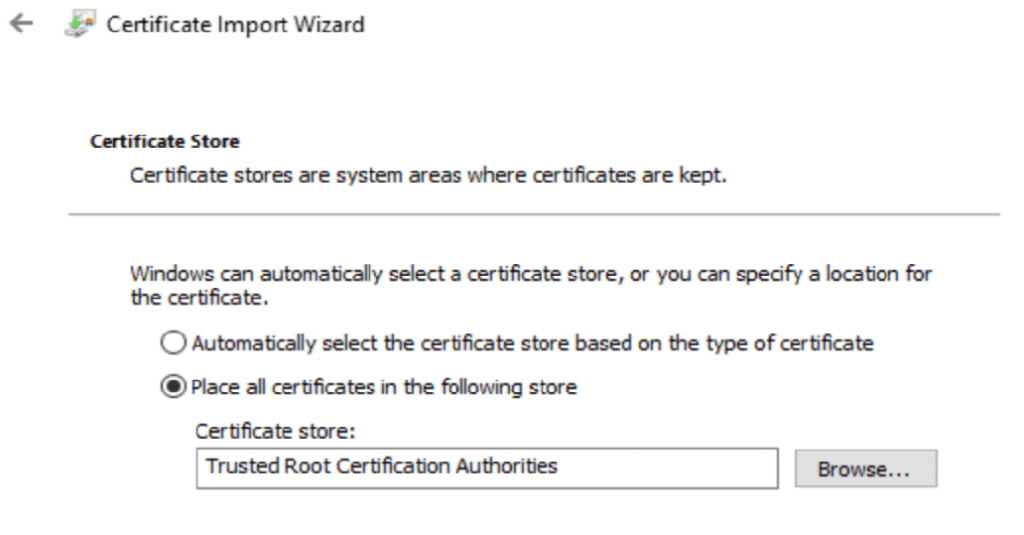
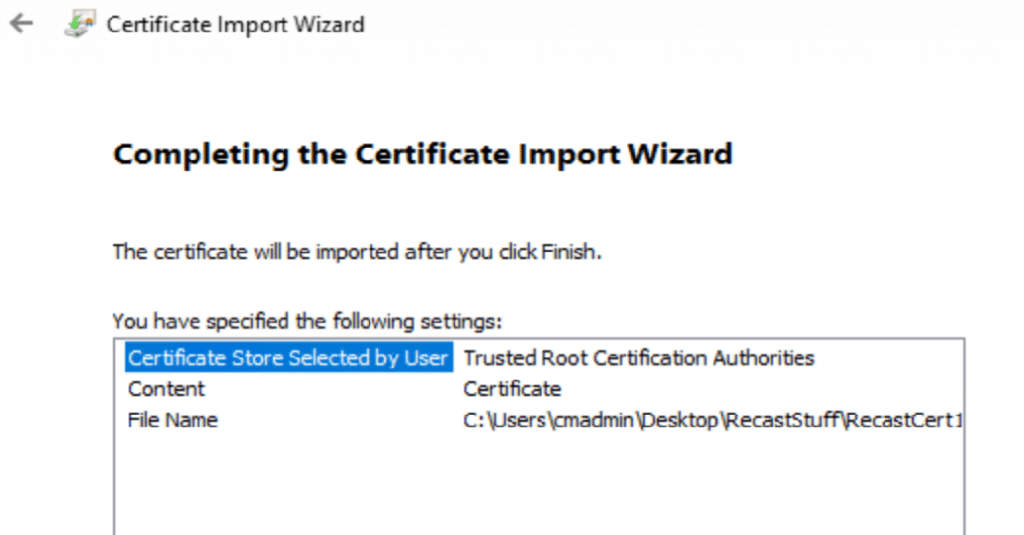
To Export the Self-Signed Cert, open MMC with the Certificate Snap-in, then export the Cert:
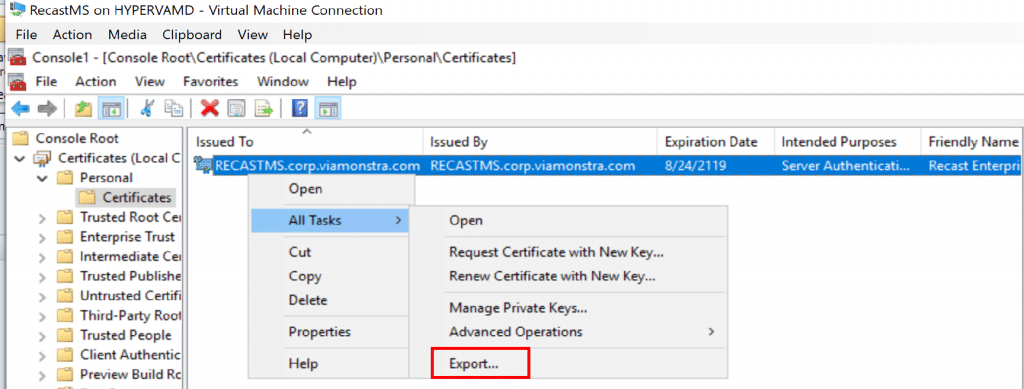
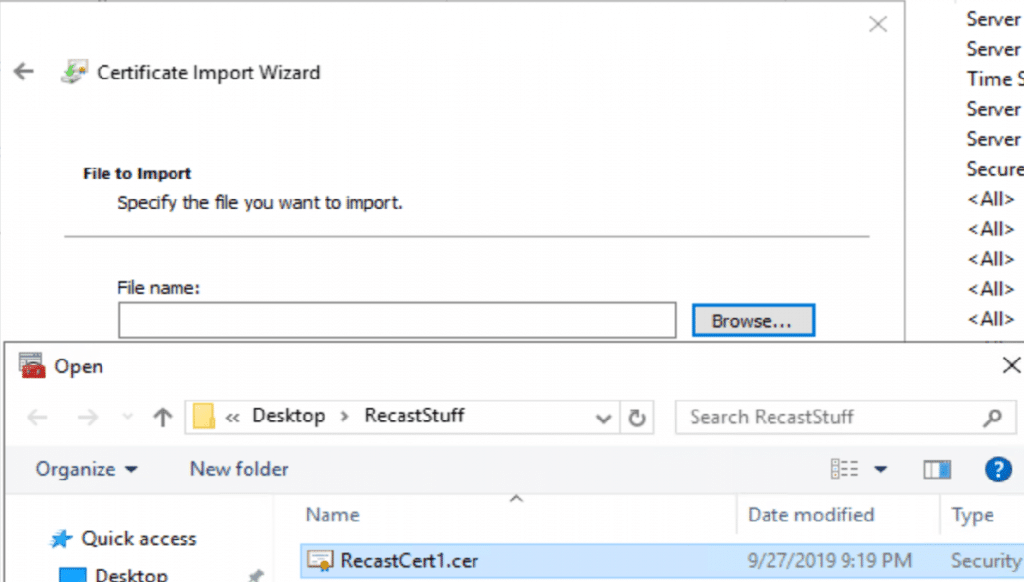
When exporting in this example, we chose all the defaults then saved it to our Source Share where we could access it easily when we install the Proxy Software.
Before we Start, Lab Setup:
- Main Domain: CORP.VIAMONSTRA.COM
- DC (AD / DNS) = DC01
- ConfigMgr Primary Site (MP/DP) = CM
- SiteCode = PS2
- Recast Server = RecastMS
- UnTrusted Domain: CORP.RECASTVILLE.COM
- DC (AD / DNS) = RECASTVILLEDC
- Recast Proxy Host = RVILLE-PROXY
- Service Account “RecastService” is Local Admin on all Workstations.
- Network = 192.168.1.X / 255.255.255.0
- Router (DHCP) = ASUS Home Router
- 2 Host “Servers” running Server 2019 with Hyper-V
- Several Hyper-V VMs
- A few physical machines
1: Untrusted Domain: (Service Account Proxy)
Did you find yourself in a merger, you now have more than one Active Directory Domain, you already took time to setup your CM Infrastructure so in that other domain, but now you would like to leverage the Right Click Tools as well? No problem. First off, we’re not going to cover how to extend your CM environment in this post, but here is a useful blog write up that we used to help when setting this up in a lab.
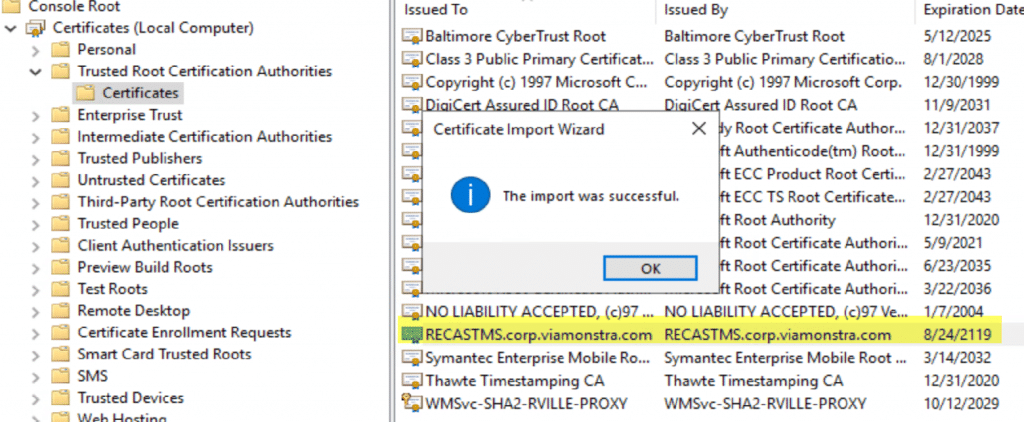
In the Unstrusted domain RECASTVILLE, we want it to be managed by the ConfigMgr Server & Recast Management Servers in the VIAMONSTRA domain. We created a dedicated box for the Proxy Host (RVILLE-PROXY), you can use a server / workstation you already have, no additional hardware / servers required. We’d recommend NOT using a domain controller as your proxy host. Before you begin your Proxy Install, if you’re using a self-signed cert, you’ll need to import it into the Trusted Root Certificates Authorities.
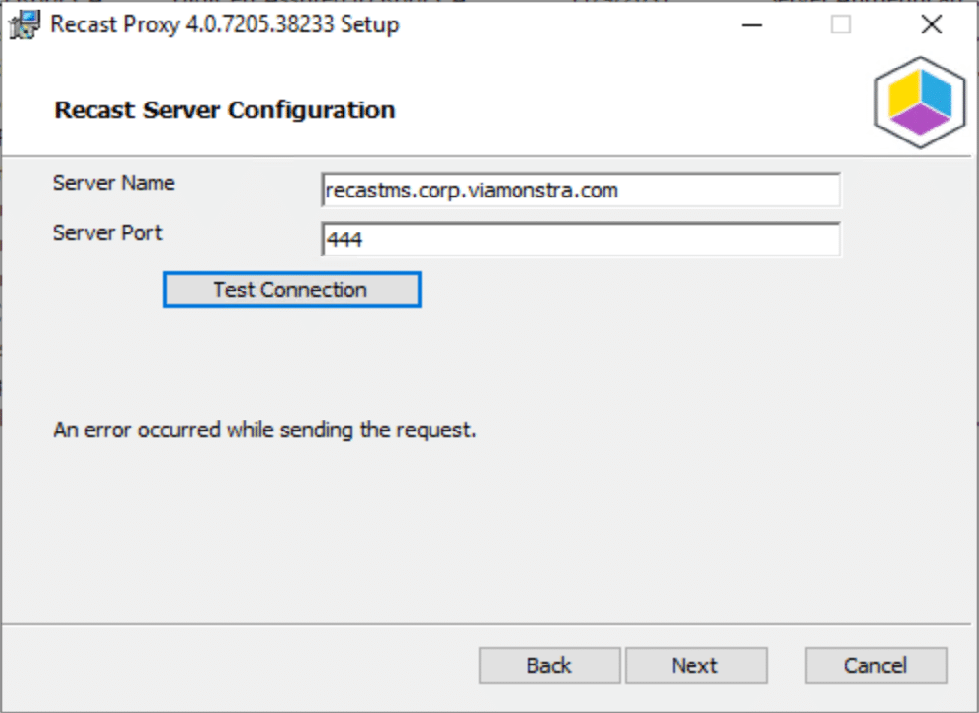
When you start the Proxy Install, if you run into this, it is probably due to the certificate. You’ll need to import the Self-Signed Certificate (if you’re not using a PKI setup or a Certificate issued by one of the main certificate authorities).
Proxy Install Instructions are already documented on the Recast Site, but I’ll walk through it here too.
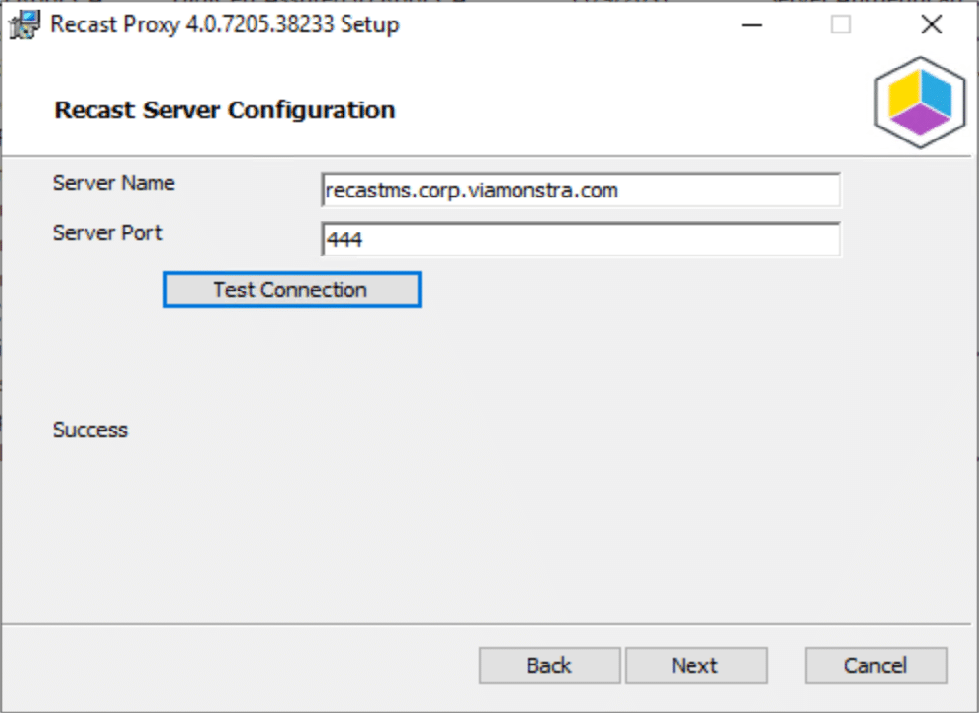
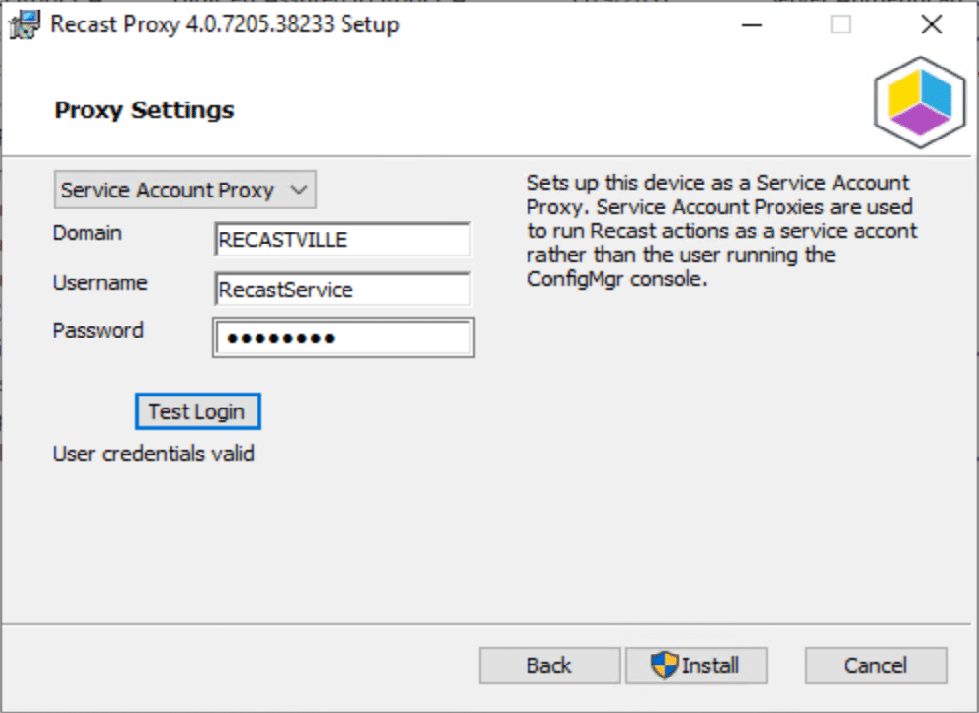
The Service Account needs to have rights on the devices you plan to trigger Right Click Actions on. This example, the RecastService is in an AD Group, which is setup in Group Policy to be a local admin on all workstations.
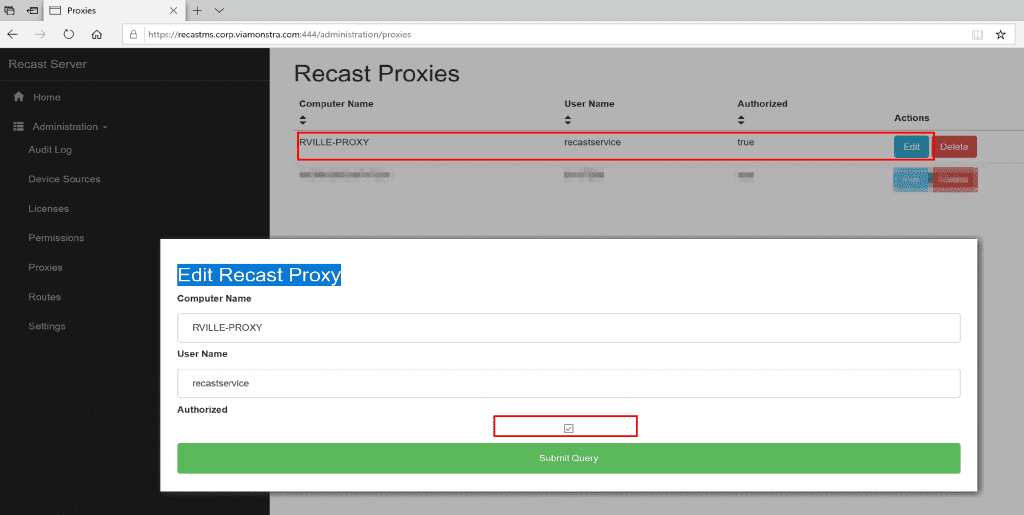
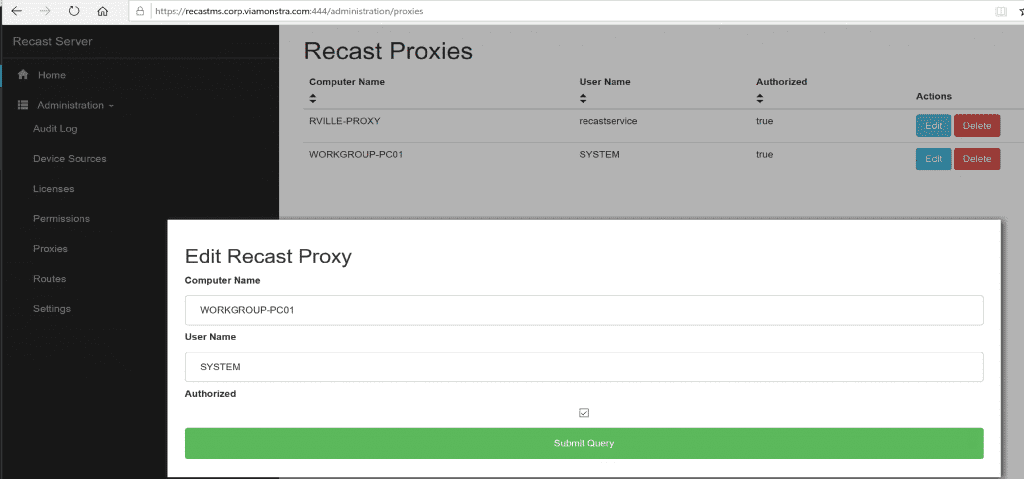
After the install, you’ll go into the Recast Server’s Web Portal, confirm the Proxy Install shows up under Proxies, then “edit” it to check the box “Authorized”.
Then Setup your Route… details on the Deployment Post
Once you have your Route Configured, and have it authorized, you can start using the tools.
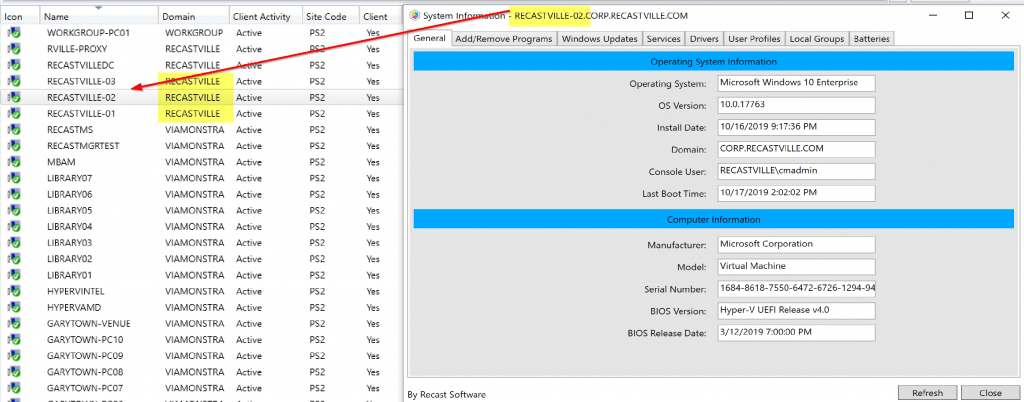
2: Work Group Computer (Device Proxy)
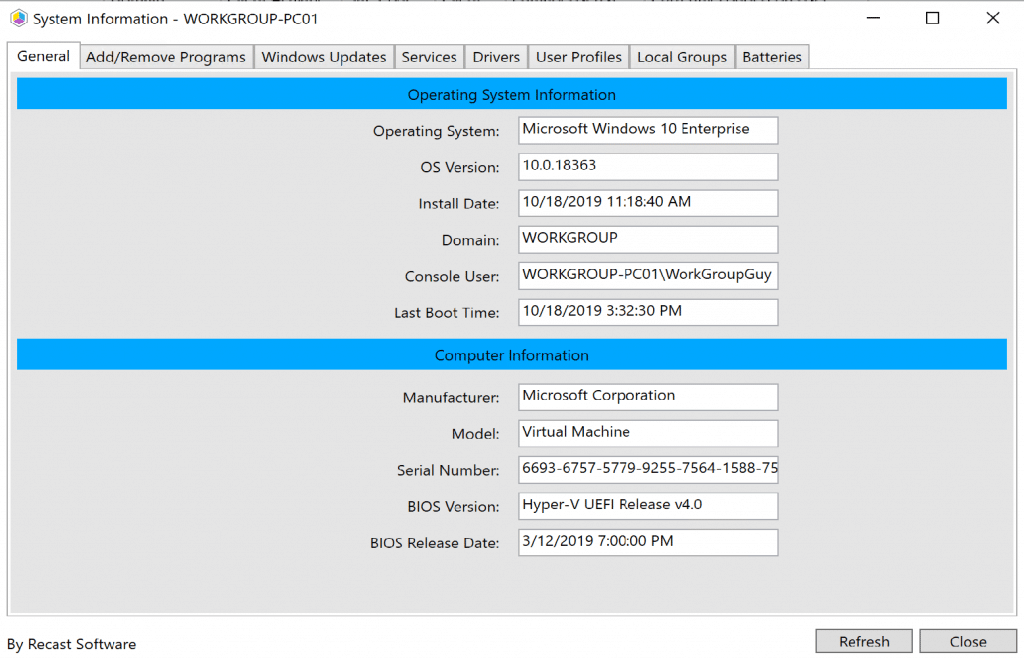
In this example, we’ve setup a Windows 10 machine, it’s not joined to any domain. We installed the CM Client manually and it populated into the Console. See more on how to install SCCM Client on Workgroup Computers from our friends at SystemCenterDudes. On the workstation Computer, we added the Recast Server’s Self-Signed Certificate, then installed the Recast Proxy, but this time in Device Mode.
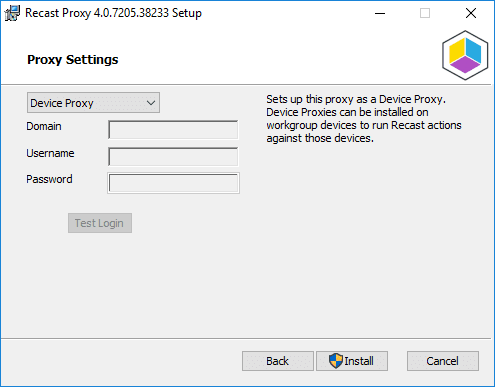
After the install, go back to the Recast Management Server’s Web Portal and authorize the Proxy.
3: Service Account / User Permissions
Scenario: Service Desk launch the Console with an account that has rights in the ConfigMgr Console, but no rights on the workstations. If you want the actions to be ran by a service account you can install a service account proxy using the same instructions as Scenario 1. In this scenario most customers chose to install the proxy on their Recast Management Server.
With the Recast Server, you can setup roles, and scopes and assign accordingly. Having Recast Proxies installed, it will allow the Techs run the tools on the machines without needing rights on those workstations. Expect a future blog post going into this scenario and going into deeper controlling rights of Console Users.
Deployment: [Deployment Blog Post]
Troubleshooting:
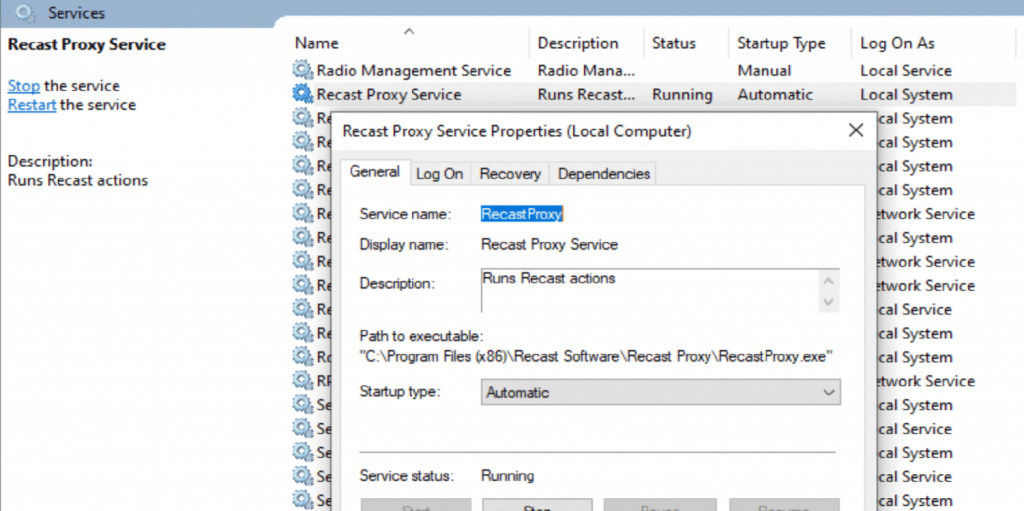
- Service, Recast Proxy, should be automatic and running
- Device Proxy. Service Uses System:
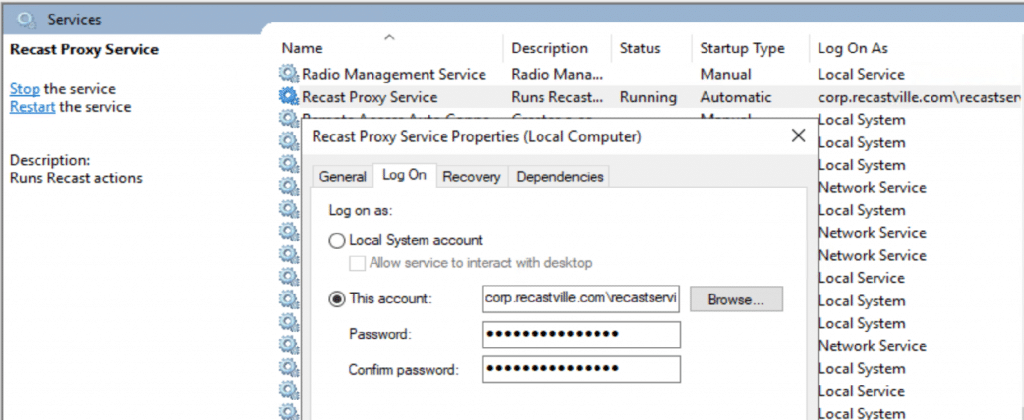
- Service Account. Service uses the Account you specify, which means it too needs to be a local admin account on the machine you run the Proxy software on.
- Certificate. As noted earlier, make sure you install the certificate if it is a self-signed Certificate. If you are using a cert from your CA or issues by a trusted authority, then you don’t need to worry about this.
- DNS, make sure you can ping the Recast Management Server and vise versa.
Recast Proxy Empowers Your Team
In summary, the Recast Proxy Software enables you to leverage your Recast investment on any device in your environment.
Check out this video to learn more about the Recast Management Server with proxy setup process.