From our 2021 cybersecurity survey, we learned that Finnish organizations are overall well equipped when it comes to cybersecurity. However, there’s still significant work to be done, particularly in the areas of mobile device and IT environment management.
The Cybersecurity Survey
In 2021, we conducted a web survey on cybersecurity and centralized device management. We got answers from more than 200 individuals from Finnish companies and organizations of all shapes and sizes.
The data we received was both insightful and, at times, painful. Securing e-mail from cybersecurity threats proved a point of strength with an excellent 94% of respondents stating it is managed well. And 90% of the respondents said their organization’s device management is centralized. In all the questions around this theme, the “yes” answers, indicating positive development, far outweighed the “no” and “I don’t know” responses.
However, the survey reveals the work is not over. Finnish companies should still pay far more attention to mobile devices security, environment development, and the managed use of workstations, applications, and SaaS services.
Cybersecurity Survey – Admin Rights
About 20% of organizations let their users go wild on their workstations without any restrictions or access right management. That’s a clear reason to worry. Unlimited admin rights are a serious cybersecurity risk, and one we recommend you tackle.

Cybersecurity Survey – File Management
Relying solely on a local server for file management, coupled with potential data dispersed across external hard drives and USB flash drives, presents a multitude of risks. Most organizations use cloud services to save data, but considering how widely available and easy to use cloud services are, 13% of respondents answering “No” is simply too much.

Cybersecurity Survey – Centralizing Device Management
About 80% of the organizations participating in the survey have transitioned to centralized device management, and that is great news!

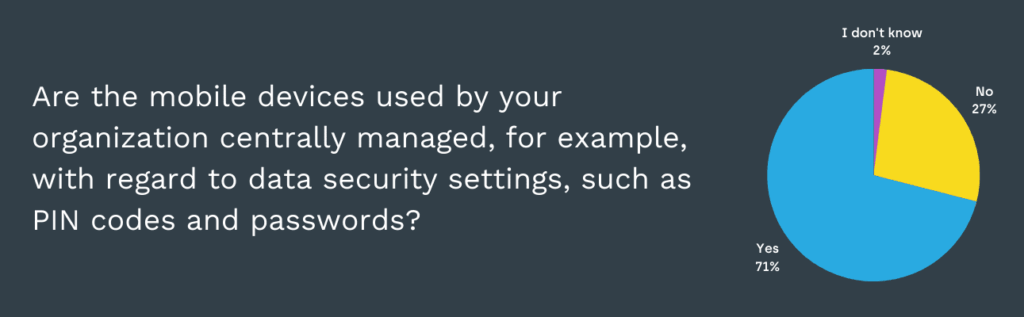
Cybersecurity Survey – Mobile Device Management
Nowadays mobile devices are just as essential to an organization’s cybersecurity as workstations and laptops. Without centralized management and best-practice security in place, the risks are significant. When asked whether mobile devices were centrally managed, almost 30% of respondents answered “No” or “I don’t know.”
A cell phone is often seen as a personal device, even though the user can use it to access important and valuable organizational data. Securing mobile devices without complicating the users’ life is feasible and less complicated than many think, and it should be prioritized.
Cybersecurity Survey – Email Systems
A mere 1% of the respondents work in an environment with e-mail systems unprotected from cyber threats, and that is something to celebrate! The 1% and 5% that checked “No” and “I don’t know” should take steps to bolster their digital communication security. Implementing an email scanning tool to catch emails containing malicious links and attachments is a great first step that has become easier than ever. For instance, Microsoft Defender for Office365 provides email filtering and protection for Teams and is broadly used and manageable to implement.

Cybersecurity Survey – SaaS Management
24% of the respondents said that their organization does not oversee or manage the installation of applications or SaaS service use. That’s quite concerning!
Centralized application management should be on every modern organization’s agenda. Not only is it essential for cybersecurity, but managed and systematic use of applications and services makes everyone’s work easier and improves the organization’s effectiveness and productivity.
Learn more about centralized application management here.

Cybersecurity Survey – Environment Development
At first glance, these numbers don’t look too bad. Almost 90% of organizations have this covered. However, an IT environment is an essential requisite for operations, so seeing that 11% of companies either do not develop their environments or are not sure of it raises concern.
I doubt any company would say their business doesn’t need constant development. Too often, the attitude towards IT environments can be viewed differently. An evolving IT environment that is actively developed is a huge asset for an organization, whereas an environment that does not evolve increases cybersecurity threats, slows down operations, and can create all kinds of other problems and risks.
Recast Software’s product suite is designed to develop a company’s IT environment together with the customer, adapting to both the company’s operations and the requirements of the ever-changing world.

Conclusion: Cybersecurity Survey Revealed Successes and Underlying Issues within Finnish Companies
Recast Software wants to thank everyone who participated in this survey!
We also recommend The State of System Administration white paper. Based upon survey data collected from 500 SysAdmins globally late in 2022, the white paper contains insights into topics including:
- How satisfied are system administrators with their jobs and what factors decrease or increase that rating?
- What are the trends in endpoint management such as the future state of co-managed and pure cloud environments?
- Which software titles do IT teams find most valuable?
- How are admin rights managed today across organizational endpoint tiers?
- What is the current state of zero trust implementation and what plans are in motion to improve security within environments?
- And much more!



