Endpoint Insights
How to Test System Center Endpoint Protection (SCEP)
Topics: Endpoint Insights
While reviewing my inbox, I noticed a phishing attempt to download malware. The timing couldn’t be more perfect because I was starting to create some new System Center Endpoint Protection (SCEP) SQL Server Reporting Services (SSRS) reports working with System Center 2012 Configuration Manager (CM12) and CM12 R2 for Enhanced Web Reporting (EWR).
I needed a way to trigger SCEP into thinking my PC was infected in order to check the report layouts, so I allowed the malware to be downloaded and then immediately cleaned by the SCEP client. It worked and I was able to see the report layouts.
A few days later I needed to test my new report layouts again. Instead of looking for another phishing attempt in my inbox, I thought that there must be an easier way to fool SCEP into thinking that there was a threat. It suddenly hit me, the EICAR test virus! I remembered back to my AV Administrator days that this was a test virus that triggers SCEP. The EICAR test virus was developed by the European Institute for Computer Anti-Virus Research (EICAR).
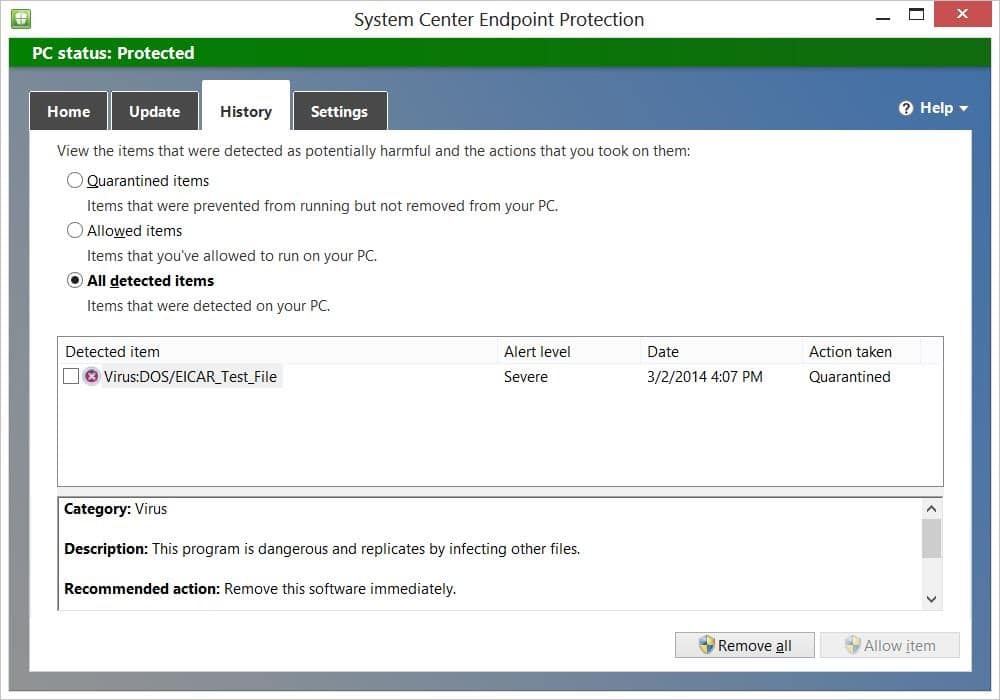
I found everything that I needed on EICAR’s website to create the EICAR test virus on my hard drive. As soon as I tried to save the file, SCEP fired an alert to notify me that malware was detected. Additionally, it provided a notice that said, “No action is needed,” and then the threat was cleaned. Finally, you can see from the SCEP interface that the EICAR test virus was quarantined.
Obviously, this was a far safer way to trigger SCEP alerts in order to test my new report layouts.
For more details about the EICAR test virus and how to get a copy of it, please see the EICAR website.
http://www.eicar.org/86-0-Intended-use.html