Intune
How to Migrate Group Policy Objects to Microsoft Intune
Topics: Intune
Are you looking to transition your Group Policy Objects (GPOs) to Microsoft Intune, but wonder how to begin this migration effectively? This article guides you through the process of importing your GPOs into Intune. We’ll delve into using Group Policy Analytics to determine the compatibility of your current settings with Intune, and how to leverage this analysis to create robust setting catalog policies.
What is Group Policy Analytics?
Group Policy Analytics is a tool in Microsoft Intune that allows you to import your Group Policy Objects from a Domain Controller to migrate to Intune. It helps you find which settings are supported for migration to cloud-native endpoints. This will help you decide which of your GPO (Group Policy Object) policies can be migrated to Intune or give you the opportunity to evaluate non-supported policies to see if they are still needed. It’s always fun to dig into those GPOs your IT admins set up for testing years ago!
Before we go further, let’s first go over some prerequisites:
Which Operating Systems Apply
- Windows 11
- Windows 10
What Will I Need
- Intune administrator
- or a role that has Security baseline permission and the Device configurations/Create permission
- Save GPO (Group Policy Objects) Policies as an .XML File
Getting Started
Go to your Domain Controller > Search for Group Policy Management.
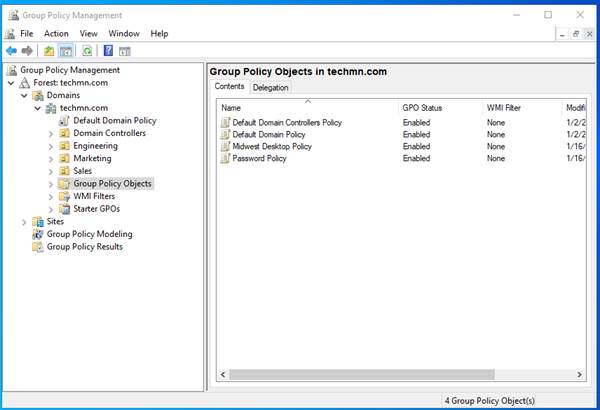
Go to the Group Policy Object OU. There you will see the Group Policy Objects you have in place.
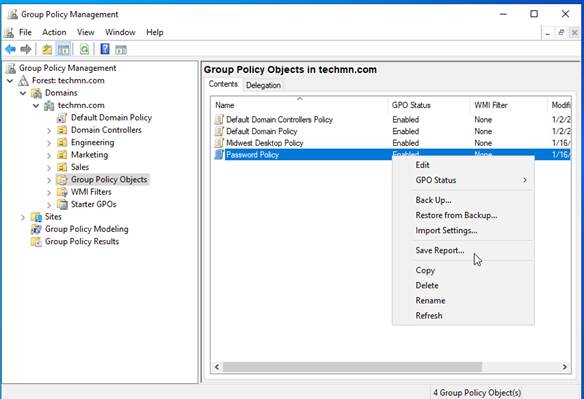
After clicking on Group Policy Objects, you will see all the Group Policy Objects in place in your domain. I’m going to select the GPOs I want to back up by right clicking on the selected items and choosing Save Report. I will then save the file as an .XML.
Go ahead and select a location you would like to backup the Group Policy Objects. Set a description to help distinguish your backups in case you’re dealing with multiple. Also make sure the format is set to XML Document.
Now that you have your .XML files, let’s head over to Intune to import these GPOs. Go to https://intune.microsoft.com > Devices > Group Policy Analytics.
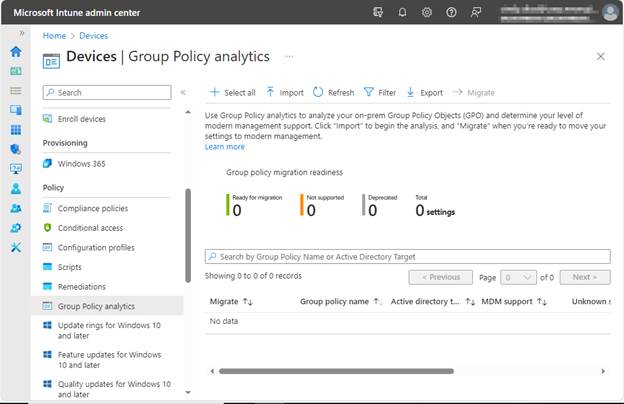
Click on Import > You’ll be brought to the following screen, which gives you information on Group Policy Analytics and directions on exporting and importing your GPOs. Find the .XML files we saved earlier, select them for import, and click Next when done.
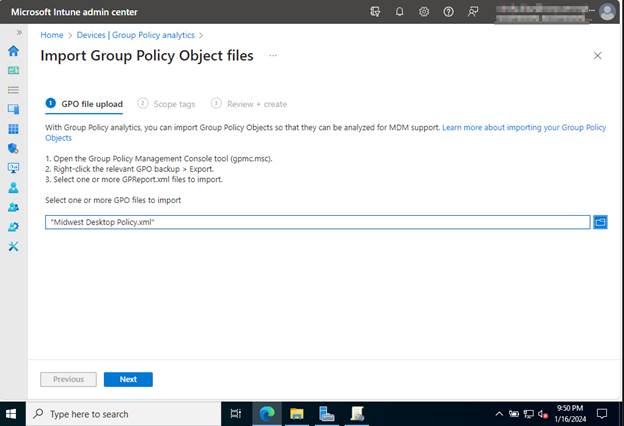
After clicking Next, you’ll be prompted to add any scope tags. In my case, I don’t have any set. However, if you do, go ahead and make the best choice for your situation.
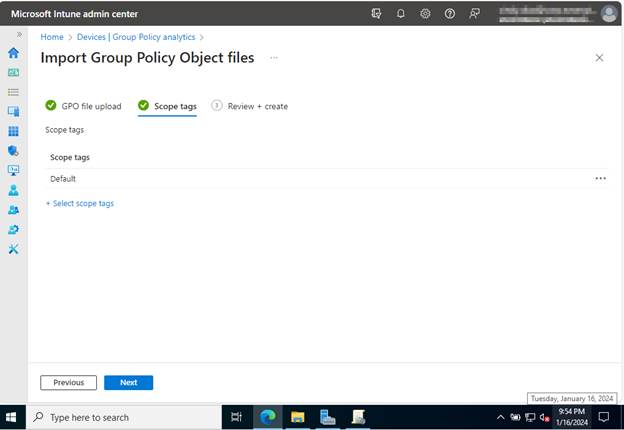
Verify you’ve added all the imports and scope tags, and assigned them to the correct place. Click Create when finished to view the results.
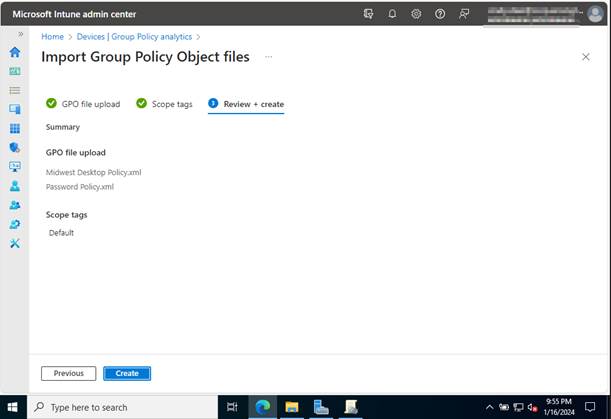
Once we have imported those, you will see your Group Policies displayed on the screen. In this case, I added both Midwest Desktop Policy and Password Policy. We can see that Midwest Desktop Policy is 100% MDM Supported, which means all the settings in the GPO can be migrated to CSP.
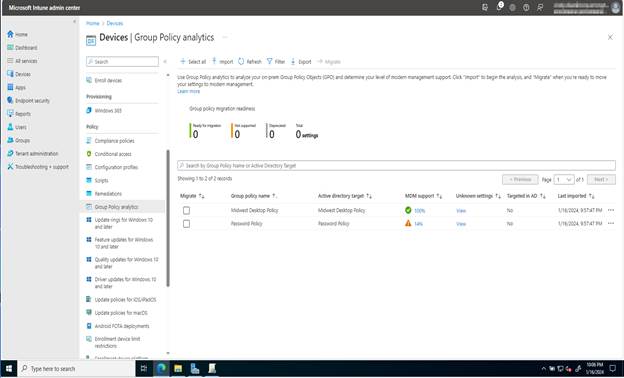
Click on the 100% under MDM Support to learn more about the policies that can be migrated. You can see details including the Min OS (Operating Systems) version required, the CSP Mapping (which shows the OMA-URI path for the on prem policy), and other information associated with the settings.
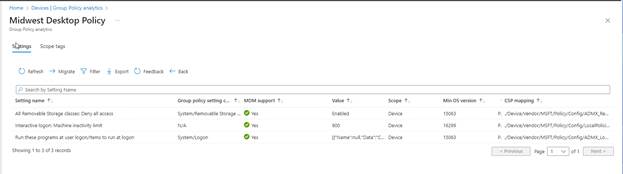
Note the Password Policy which has 14% of MDM support. This indicates that most of those GPO policies cannot be migrated. Let’s go ahead and click on the 14% to learn more.
After clicking on 14% under MDM Support, I’m brought to the GPO Analytics, which doesn’t show us great results. The reason we are seeing the No under MDM support is because these GPOs do not have settings that can be translated to MDM settings.
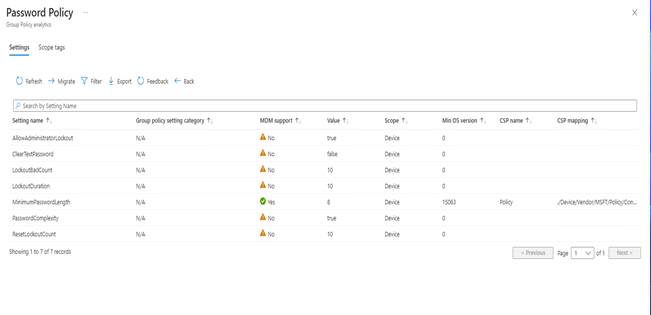
For now, I will go back to Group Policy Analytics and select the GPO that has 100% MDM support and select Migrate.
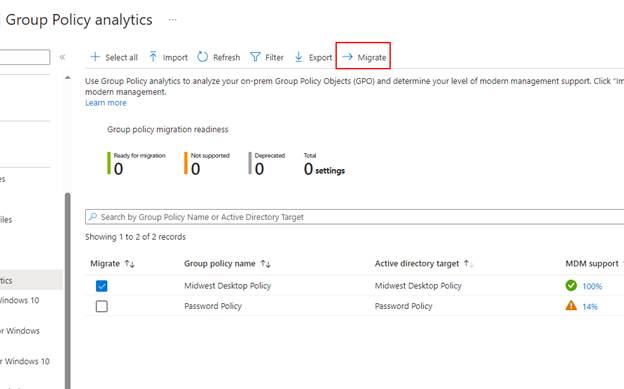
Once you have clicked on Migrate, you will be prompted to the following screen where you can choose all the settings you want to migrate to Intune. I went ahead and selected All.
Note: It’s best to test with a pilot group before migrating and enabling these settings in your environment.
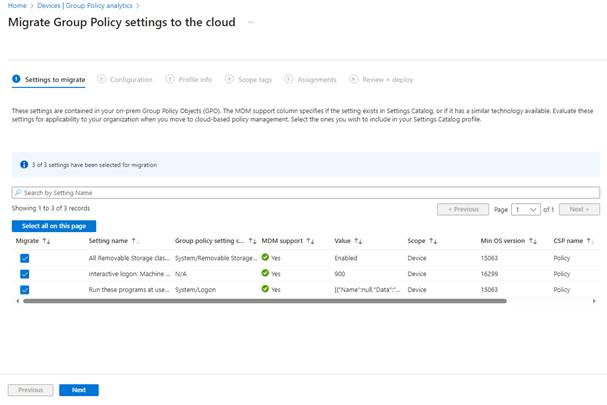
Next, on the configuration page we will see where GPO Analytics has created setting catalog policies using our imported GPOs.
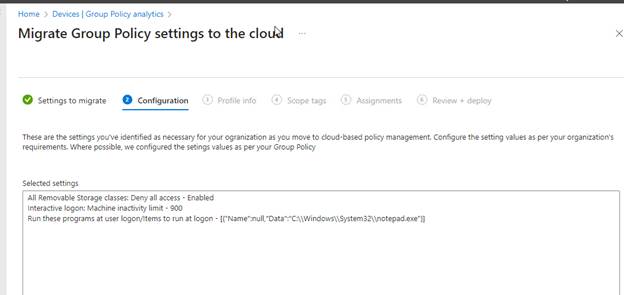
The following configuration will land on the Profile info page, where we can give this migration a name and description to help for future reference. Click Next to move forward.
We did not have any scope tags, so I chose Next and landed on Assignments. Here I will choose who will get these settings. I chose Add all users, but remember it’s best to test this out before deploying to everyone in your environment. Click Next to review your migration.
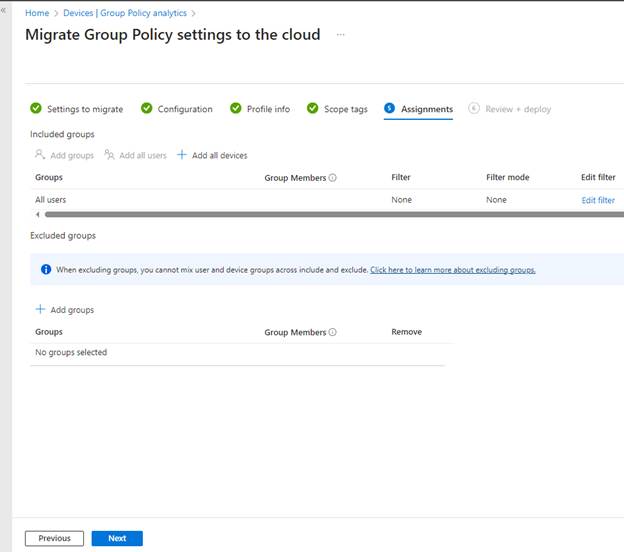
Review and verify that everything looks correct and deploy when ready.
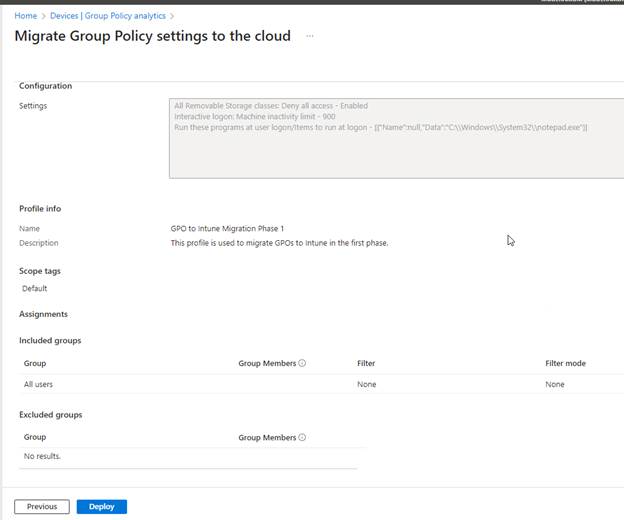
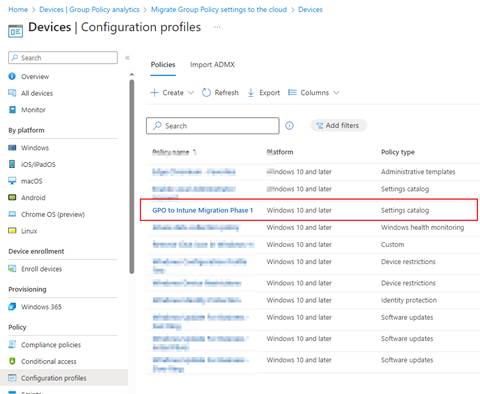
After deploying, we can now see that our GPO migration is shown in the Configuration Profile under the profile name we gave it earlier. The settings have also migrated successfully.
Conclusion: Group Policy Objects Transferred
Migrating Group Policy Objects to Microsoft Intune using Group Policy Analytics is a significant step forward in modernizing your IT infrastructure. This process streamlines management while also enhancing security and compliance. By following the steps outlined in this guide, you can efficiently transition your GPOs to a cloud-based environment.
As always, it’s important to thoroughly plan and test your migration to avoid potential pitfalls.
Additional Intune Posts
- How to create a Win32 application and deploy with Intune
- How to Set Up Free Microsoft 365 Developer Program
- Collecting Custom Inventory with Intune: A Step-by-Step Guide
- Configure BitLocker on Windows Devices with Intune
- How to Upgrade Windows 10 Devices to Windows 11 with Intune
- Step-by-Step Guide: Enabling Windows LAPS in Entra ID
- How to Configure Bitlocker with Intune
- How to Set Up Windows LAPS with Microsoft Intune