Intune
How to Block Apps with Intune
Topics: Intune
Managing app installations is a vital aspect of IT administration for any organization, helping to improve security and ensure compliance with internal policies.
Why Block Apps with Intune?
With recent legislative actions, such as the US House of Representatives and the President moving toward a potential ban of TikTok, compliance with new regulations may become mandatory for many US organizations. This guide will walk you through the steps to block specific apps, such as TikTok, within the Microsoft Store using Microsoft Intune by leveraging the AppLocker functionality in Windows.
Blocking specific apps is important for several reasons:
- Security Considerations: Preventing installations of apps that could pose security risks.
- Enhancing Productivity: Limiting access to apps that might distract employees.
- Compliance and Regulatory Requirements: Ensuring only approved apps are used in regulated environment
Step-by-Step Guide to Blocking Apps with Intune
Section 1: Creating an AppLocker Policy in Windows
- On your test machine, visit the Microsoft Store and install TikTok.
- Go to the Start Menu, type “Local Security Policy,” right-click on it, and run as Administrator.
- Navigate to Application Control Policies > AppLocker > Package App Rules.
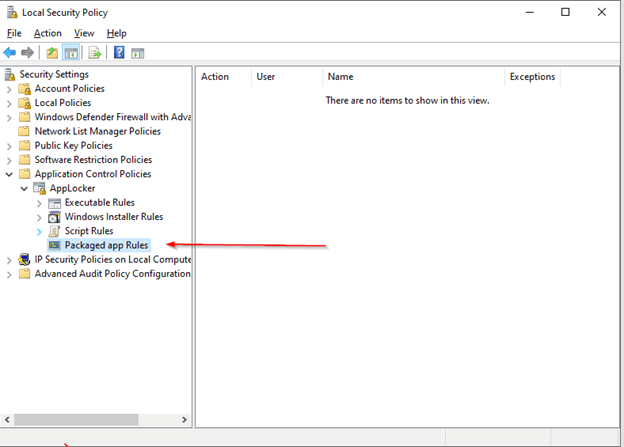
- Right click on Package App Rules.
- Select Create New Rule.
- Click Next in the dialog box.
- Select Deny > then Next.
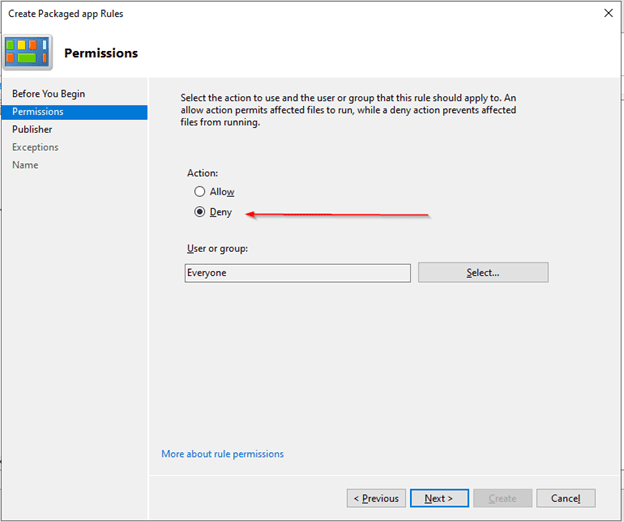
- Keep the default option selected. Click the Select, choose TikTok from the list, and press OK.
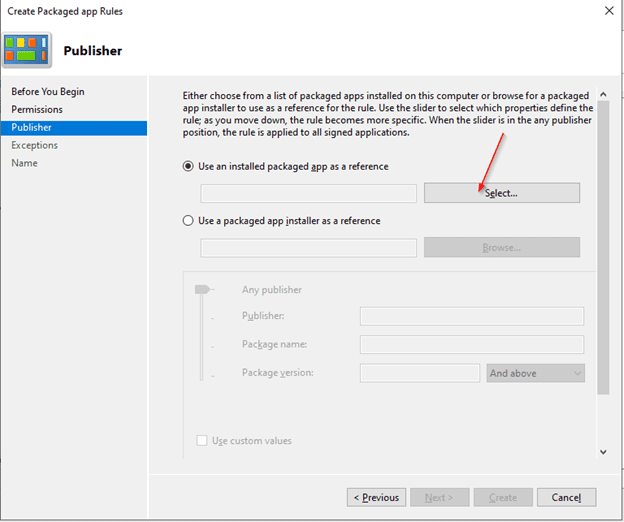
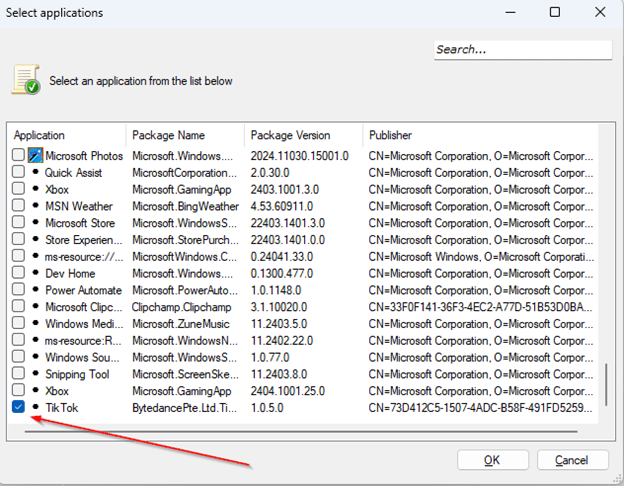
- Once TikTok is selected, adjust the slider from Package Version to Package Name to specify that the policy should block all versions of TikTok.
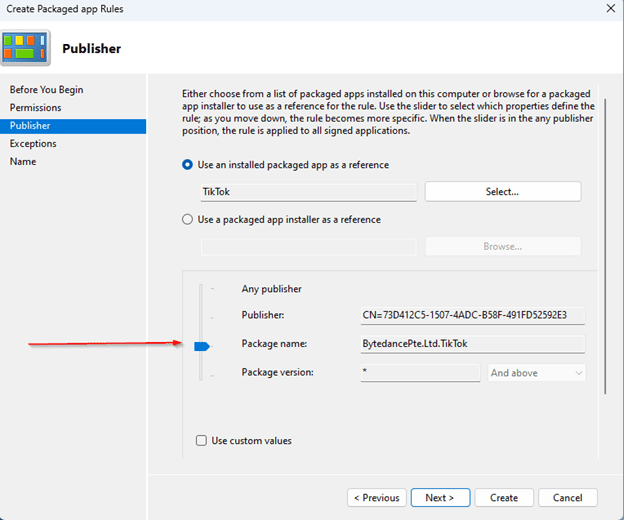
- Click Next several times, name your policy, provide a description, and then click Create to finalize your Block Policy.
- Right click on Package App Rules again and select Create Default Rules to ensure that the policy does not block any unintended applications.
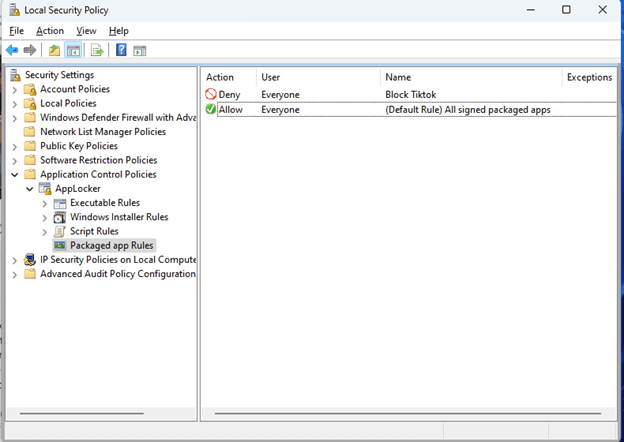
Completing the AppLocker Configuration
- Now that rules are created, Right click on Applocker on the left blade and select Properties.
- Check Configured under Packaged App Rules > select Enforce Rules > then Click OK.
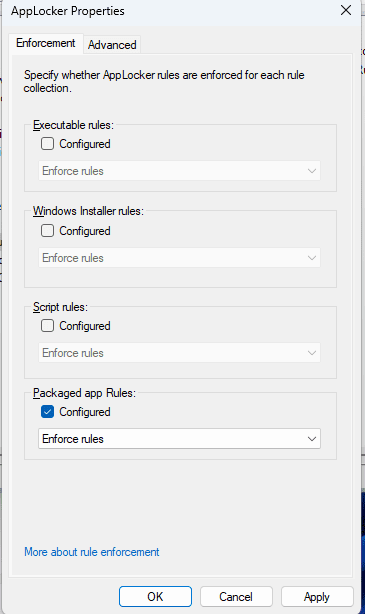
Exporting the AppLocker Policy
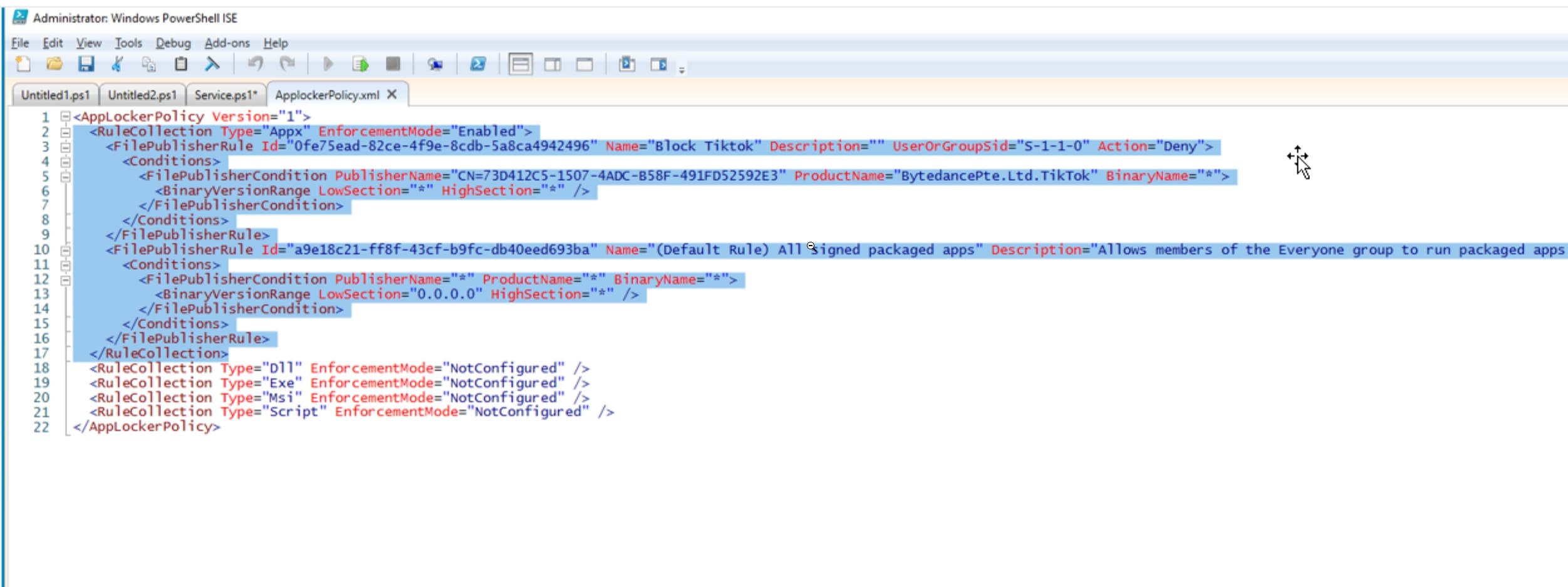
- Right click on AppLocker on the left blade again and select Export Policy. Save the XML file to your desktop. We will need this file later in the Intune section.
- Open the XML file. You will notice that the rule configuration starts with <RuleCollection> and ends with </RuleCollection>. Copy this highlighted text within your XML file to your clipboard.
Section 2: Implementing the Block Policy in Intune
- Login to intune.microsoft.com.
- Navigate to Devices > Configuration Profiles.
- Click on Create Profile > New Policy. Select Windows 10 and later for platform.
- Profile type should be Templates with Custom as the Template name > Click Create.
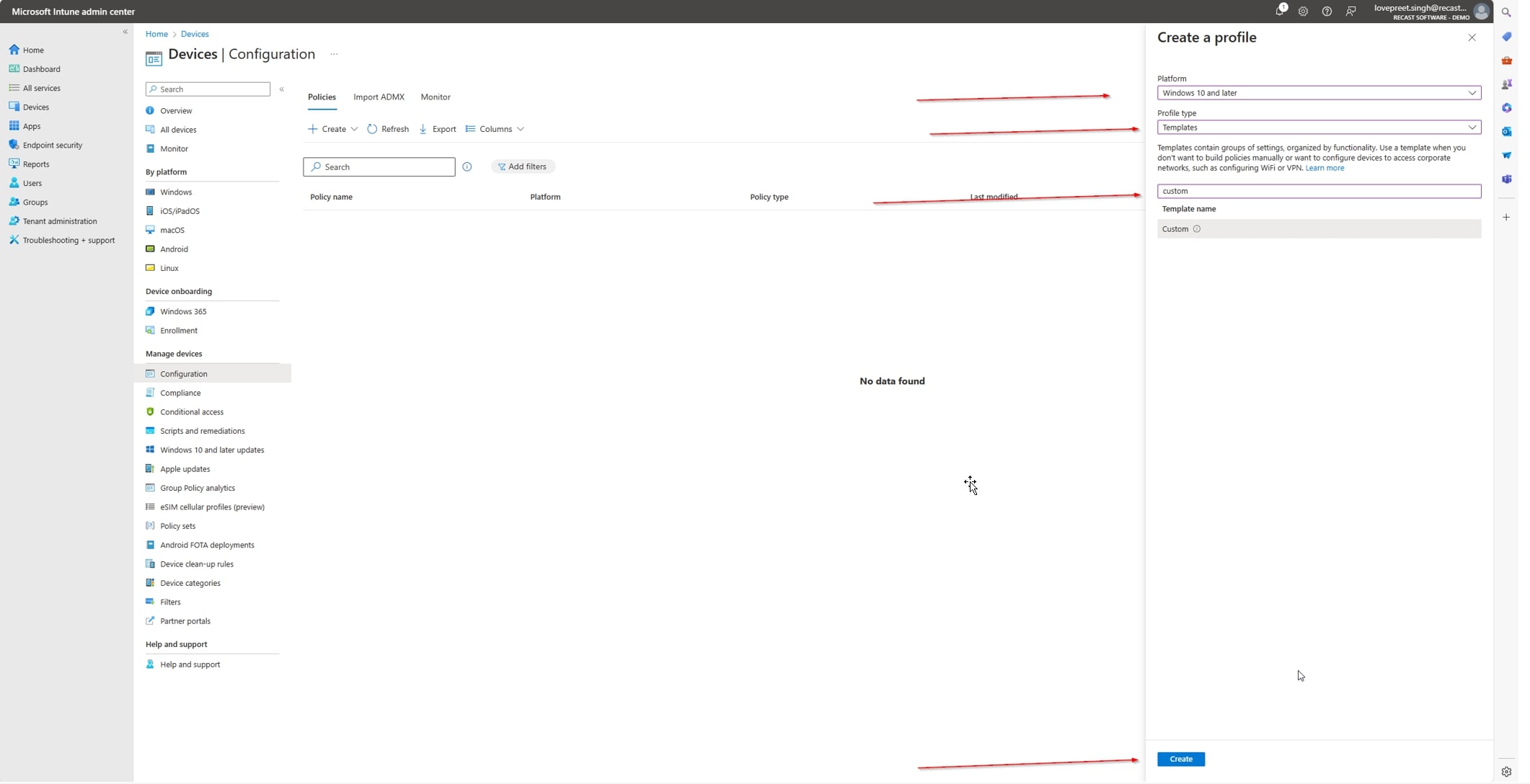
- Give your policy a name and description that reflects its purpose, e.g., “Block Tiktok” > click Next.
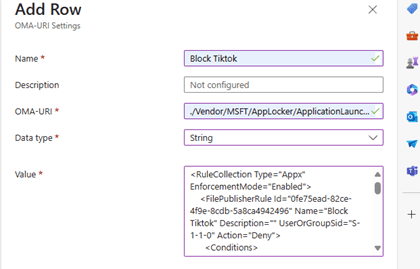
- Under Configuration settings, click on Add next to OMA-URI settings.
- Name the setting, provide a description, select String as the Data Type, and paste the content from the XML file into the Value section.
- For “OMA-URI,” use the following string: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/apps/StoreApps/Policy
For more information on Applocker CSPs, refer to this article: AppLocker CSP – Windows Client Management | Microsoft Learn
- Click Save and continue to assign the Intune group where you want to apply this profile. Follow the prompts to finish creating the profile.
Section 3: Monitor and Manage App Blocking with Intune
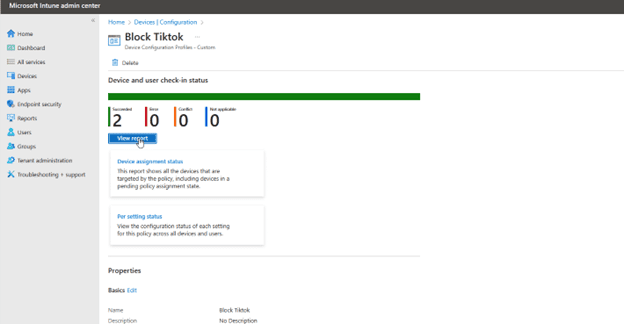
After deploying the policy, monitor its impact through the View reports button. Once the policy is successfully applied on devices, TikTok will be blocked on the Microsoft Store.
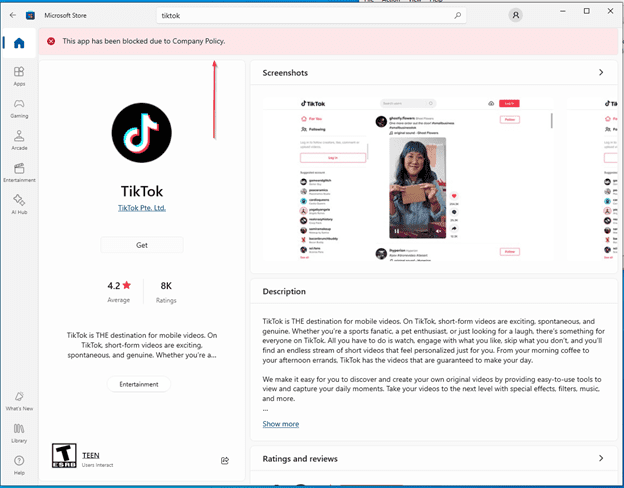
Appendix: Extending App Blocking to Other File Types
Just like blocking Microsoft Store apps, we can also block unapproved exe, msi, and script files using AppLocker and Intune. The process remains largely the same, with only two changes required:
- In Section 1, steps 5 and 10, instead of clicking on Packaged app rules, we will right click on Executable rules (for exe) and Windows Installer Rules (for msi).
- The OMA-URI will also change as mentioned below.
- For exe files: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/apps/EXE/Policy
- For msi: ./Vendor/MSFT/AppLocker/ApplicationLaunchRestrictions/apps/MSI/Policy
Conclusion: Enhancing Security and Compliance with Intune
By utilizing Microsoft Intune and AppLocker, organizations can effectively block unauthorized apps, enhancing security and ensuring compliance. This guide demonstrates a straightforward method to manage applications and maintain control over your IT environment. As you adapt and refine your endpoint management strategies, Intune’s capabilities support a secure, productive, and compliant workplace. Continuous monitoring and updating of these policies are essential to address the evolving challenges that inevitably arise.