Application Management and Patching
February 2025 Third-Party Patches: Notable Vulnerabilities and Updates
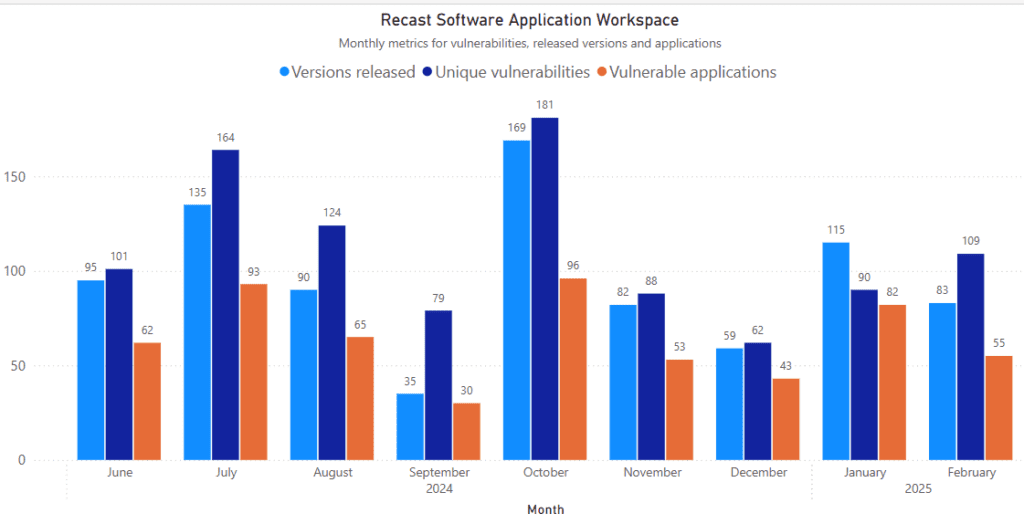
February’s data shows fewer vulnerable applications and fewer new software versions released. However, the total number of patched vulnerabilities increased, meaning each release patched more vulnerabilities on average than in January. This month, prioritize updates for browsers, especially those classified as high-risk vulnerabilities.
Notable Vulnerabilities in February 2025 Third-Party Patches
In February 2025 there were no patched vulnerabilities with 9.0 or higher CVSS rating. This means that none of the vulnerabilities were classified as critical. None of the vulnerabilities were classified as a zero day either.
Chromium-Based Vulnerabilities
- CVE-2025-0999 has a CVSS rating of 8.8 and it affects multiple Chromium based products such as Chrome, Edge, Electron, Edge and Burb Suite. More information can be found on the Google Chrome release notes. There are more Chromium related vulnerabilities. More information can be found on Google’s corresponding release notes pages.
- CVE-2025-0612, CVE-2025-0611: Initially patched for most browsers in January; Electron 32 update released this month. More information can be found on their release notes as well as this set of notes.
- CVE-2025-0437, CVE-2025-0762: Chromium vulnerabilities originally released in January, but patched for Microsoft Edge in February. More information can be found on Microsoft MSRC’s advisory. The second vulnerability was also patched by Brave Browser.
- Additional Chromium vulnerabilities patched this month:
Brave Browser Vulnerabilities
Brave has finally patched CVE-2025-0995 that allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. More information about the vulnerability can be found on Google Chrome’s release notes.
Mozilla Vulnerabilities
Firefox and Thunderbird had a memory safety vulnerability CVE-2025-1017 affecting them. More information can be found on the Mozilla’s security advisory. CVE-2025-1020 was another vulnerability patched by Mozilla. See this advisory for more information. Third affecting vulnerability is CVE-2024-11704.
TurboVNC Vulnerabilities
TurboVNC is a derivative of VNC (Virtual Network Computing) that is tuned to provide peak performance for 3D and video workloads. It was patched for CVE-2024-9632. Release notes can be found on GitHub. If you are interested in more vulnerability details, you can check out the original advisory in GitHub too.
Browser Security Updates in February 2025
| Browser | Vulnerabilities | Updates |
| Google Chrome | 10 | 3 |
| Microsoft Edge | 52 | 5 |
| Brave Browser | 8 | 3 |
| Pale Moon | 1 | 1 |
| Mozilla Firefox | 12 | 2 |
| Mozilla Firefox ESR 115 | 4 | 2 |
| Mozilla Firefox ESR 128 | 9 | 3 |
| Waterfox | 7 | 1 |
Microsoft Product Updates Included in February 2025 Third-Party Patches
In addition to Edge, Microsoft issued security updates for several widely-used tools, including Microsoft 365 Apps, Visual Studio (2017-2022), Visual Studio Code, and related developer tools, addressing vulnerabilities primarily related to stability and security.
- Microsoft 365 Apps
- Microsoft Visual Studio Code
- Microsoft Visual Studio 2019 Enterprise
- Microsoft Visual Studio 2022 Community
- Microsoft Visual Studio Team Explorer 2019
- Microsoft Visual Studio Team Explorer 2022
- Microsoft Visual Studio Feedback Client 2017
- Microsoft Visual Studio Team Explorer 2017
- Microsoft Visual Studio 2019 Community
- Microsoft Visual Studio 2017 Enterprise
- Microsoft Visual Studio 2017 Community
- Microsoft Visual Studio 2017 Professional
- Microsoft Visual Studio 2019 Professional
- Microsoft Visual Studio 2022 Enterprise
- Microsoft Visual Studio 2022 Professional
Detailed List of February 2025 Third-Party Patches
For a complete list of applications, versions, and the number of remediated vulnerabilities, see the table below generated using Application Workspace data.
| ProductName | VersionName | Vulnerabilities remediated |
| Brave Browser | 1.74.51 | 1 |
| Brave Browser | 1.75.180 | 3 |
| Brave Browser | 1.75.178 | 4 |
| Burp Suite Community Edition | 2025.2.1 | 3 |
| Burp Suite Community Edition | 2025.2 | 3 |
| Burp Suite Professional Edition | 2025.2.1 | 3 |
| Burp Suite Professional Edition | 2025.2 | 3 |
| Chef Workstation | 25.2.1075 | 3 |
| Chef Workstation for Windows | 25.2.1075 | 3 |
| Datadog Agent | 7.63.0 | 1 |
| Electron | 32.3.2 | 3 |
| Electron | 33.4.2 | 3 |
| Electron | 32.3.2 | 0 |
| EnterpriseDB Corporation PostgreSQL 13 | 13.19.1 | 1 |
| EnterpriseDB Corporation PostgreSQL 14 | 14.16.1 | 1 |
| EnterpriseDB Corporation PostgreSQL 15 | 15.11.1 | 1 |
| EnterpriseDB Corporation PostgreSQL 16 | 16.7.1 | 1 |
| EnterpriseDB Corporation PostgreSQL 17 | 17.3 | 1 |
| EnterpriseDB Corporation PostgreSQL 17 | 17.3.1 | 1 |
| Github CLI | 2.67.0 | 1 |
| Google Chrome for Business | 133.0.6943.99 | 4 |
| Google Chrome for Business | 133.0.6943.127 | 3 |
| Google Chrome for Business | 133.0.6943.54 | 3 |
| Google Go Programming Language 1.22 | 1.22.12 | 1 |
| Google Go Programming Language 1.23 | 1.23.6 | 1 |
| JetBrains ReSharper 2024.1 | 2024.1.7 | 1 |
| MariaDB Server 10.11 | 10.11.11 | 1 |
| MariaDB Server 10.5 | 10.5.28.0 | 1 |
| MariaDB Server 10.6 | 10.6.21 | 1 |
| MariaDB Server 11.4 | 11.4.5 | 1 |
| Microsoft 365 Apps | 2408 (Build 16.0.17928.20440) | 20 |
| Microsoft 365 Apps | 2412 (Build 16.0.18324.20240) | 20 |
| Microsoft 365 Apps | 2501 (Build 16.0.18429.20158) | 20 |
| Microsoft 365 Apps | 16.94.25020927 | 7 |
| Microsoft Edge Beta | 133.0.3065.51 | 10 |
| Microsoft Edge Beta | 133.0.3065.51 | 15 |
| Microsoft Edge for Business | 133.0.3065.51 | 15 |
| Microsoft Edge for Business | 133.0.3065.59 | 15 |
| Microsoft Edge for Business | 133.0.3065.69 | 5 |
| Microsoft Edge for Business | 133.0.3065.82 | 3 |
| Microsoft Edge for Business | 133.0.3065.59 | 14 |
| Microsoft Visual Studio 2017 Community | 15.9.35727.129 | 1 |
| Microsoft Visual Studio 2017 Enterprise | 15.9.35727.129 | 1 |
| Microsoft Visual Studio 2017 Professional | 15.9.35727.129 | 1 |
| Microsoft Visual Studio 2019 Community | 16.11.35731.53 | 2 |
| Microsoft Visual Studio 2019 Enterprise | 16.11.35731.53 | 2 |
| Microsoft Visual Studio 2019 Professional | 16.11.35731.53 | 2 |
| Microsoft Visual Studio 2022 Community | 17.13.35806.99 | 1 |
| Microsoft Visual Studio 2022 Enterprise | 17.12.35728.132 | 1 |
| Microsoft Visual Studio 2022 Enterprise | 17.10.35728.63 | 1 |
| Microsoft Visual Studio 2022 Enterprise | 17.13.35806.99 | 1 |
| Microsoft Visual Studio 2022 Enterprise | 17.8.35728.64 | 1 |
| Microsoft Visual Studio 2022 Professional | 17.8.35728.64 | 1 |
| Microsoft Visual Studio 2022 Professional | 17.10.35728.63 | 1 |
| Microsoft Visual Studio 2022 Professional | 17.13.35806.99 | 1 |
| Microsoft Visual Studio 2022 Professional | 17.12.35728.132 | 1 |
| Microsoft Visual Studio Code | 1.97.1 | 1 |
| Microsoft Visual Studio Feedback Client 2017 | 15.9.35727.129 | 1 |
| Microsoft Visual Studio Team Explorer 2017 | 15.9.35727.129 | 1 |
| Microsoft Visual Studio Team Explorer 2019 | 16.11.35731.53 | 2 |
| Microsoft Visual Studio Team Explorer 2022 | 17.13.35806.99 | 1 |
| Mozilla Firefox | 135.0.1 | 1 |
| Mozilla Firefox | 135.0 | 11 |
| Mozilla Firefox ESR 115 | 115.20.0 | 4 |
| Mozilla Firefox ESR 115 | 115.20.0 | 0 |
| Mozilla Firefox ESR 128 | 128.7.0 | 9 |
| Mozilla Firefox ESR 128 | 128.7.0 | 0 |
| Mozilla Thunderbird ESR 128 | 128.7.0 | 12 |
| OpenSSL | 3.1.8 | 2 |
| OpenSSL | 3.0.16 | 2 |
| OpenSSL | 3.2.4 | 3 |
| OpenSSL | 3.3.3 | 3 |
| OpenSSL | 3.4.1 | 2 |
| OpenSSL Light | 3.1.8 | 2 |
| OpenSSL Light | 3.4.1 | 2 |
| OpenSSL Light | 3.0.16 | 2 |
| OpenSSL Light | 3.2.4 | 3 |
| OpenSSL Light | 3.3.3 | 3 |
| Pale Moon | 33.6.0 | 1 |
| Rider 2024 | 2024.1.7 | 1 |
| Snagit 2024 | 2024.3.2 | 4 |
| Snagit 2025 | 2025.0.0 | 4 |
| Studio 3T | 2025.3.0 | 6 |
| Studio 3T | 2025.2.0 | 1 |
| TeamCity | 2024.12.2 | 2 |
| The Document Foundation LibreOffice 24 | 24.8.5.2 | 1 |
| TurboVNC | 3.1.4 | 12 |
| Waterfox | 6.5.4 | 7 |
Conclusion
Timely third-party patching remains essential for protecting your IT environment. February 2025’s updates addressed significant vulnerabilities across major browsers and applications, strengthening your organization’s defense and operational stability. Stay tuned for next month’s insights.
For deeper insights into how effective third-party patch management reduces your attack surface, explore our eBook Reduce Your Attack Footprint or follow our App Management and Patching series.





























