Application Management and Patching
December 2024 Third-Party Patches: Notable Vulnerabilities and Updates
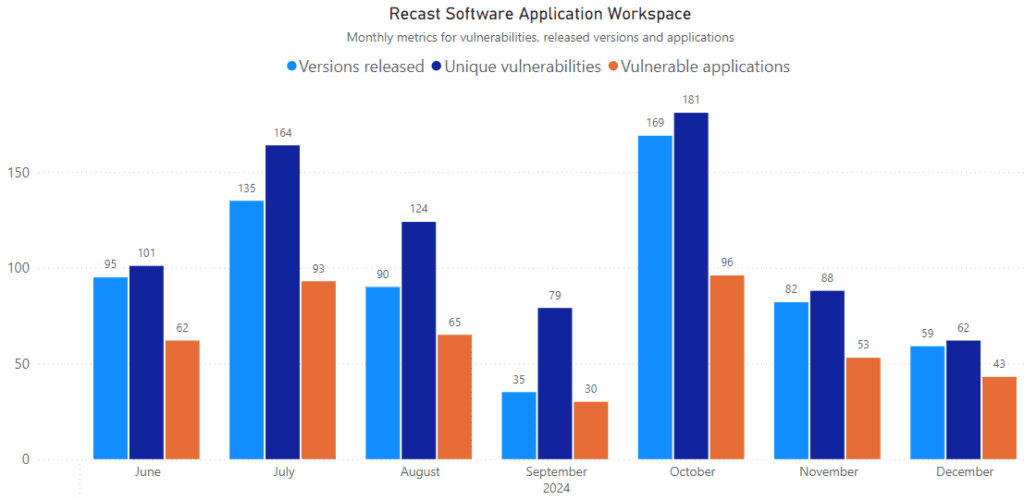
The holiday season is over, and it’s time to dig back into the patching data. Based on our internal metrics, December saw slightly fewer vulnerability activities than November. There were 43 vulnerable applications that received updates, with 59 versions released—some applications received multiple patches. In total, 62 vulnerabilities were remediated, and there were no zero-day vulnerabilities in December 2024.
Notable Vulnerabilities in December 2024 Third-Party Patches
Nine of these vulnerabilities were classified as critical. First is Microsoft .NET SDK 9.0, which was impacted by CVE-2024-43498. This remote code execution vulnerability was discussed in our November blog, but it was only just patched for the .NET SDK 9.0. More information is available at the Microsoft Security Response Center (MSRC).
Chef Infra Client and Chef Workstation contained CVE-2024-27281 and CVE-2020-8130. Because these solutions rely on Ruby, vulnerabilities in Ruby can also affect Chef. More information is available on Ruby-Lang.org.
Apache Tomcat received patches across its major versions 9, 10, and 11 for CVE-2024-50379 and CVE-2024-56337—both critical race condition vulnerabilities. More details can be found in the Apache security bulletins:
- [SECURITY] CVE-2024-56337 Apache Tomcat – RCE via write-enabled default servlet – CVE-2024-50379 mitigation was incomplete-Apache Mail Archives
- [SECURITY] CVE-2024-50379 Apache Tomcat – RCE via write-enabled default servlet-Apache Mail Archives
The Pale Moon browser, derived from Mozilla, patched two critical vulnerabilities (CVE-2024-11704 and CVE-2024-11693) that Mozilla itself patched in November. More information is available here.
CVE-2024-37051 affected JetBrains products, where GitHub access tokens could be exposed to third-party sites in their IDEs. The ARM64 version of Rider 2023 was patched in December. More information is on JetBrains’ website.
CVE-2024-45337 impacted the Datadog Agent. More information can be found on GitHub.
Browser Security Updates in December 2024
| Browser | Vulnerabilities | Updates |
| Google Chrome | 7 | 3 |
| Microsoft Edge | 8 | 3 |
| Brave Browser | 1 | 1 |
| Pale Moon | 2 | 1 |
Microsoft Product Updates Included in December 2024 Third-Party Patches
In addition to Edge, Microsoft released updates for the following products:
- Microsoft .NET SDK 9.0
- Microsoft 365 Apps
- Microsoft Remote Desktop
- Microsoft Windows PE add-on for ADK for Windows 11
- Microsoft Windows Assessment and Deployment Kit (ADK) for Windows 11
Detailed List of December 2024 Third-Party Patches
For a complete list of applications, versions, and the number of remediated vulnerabilities, see the table below generated using Application Workspace data.
| Product | Version | Vulnerabilities Remediated |
| Adobe Acrobat DC | 24.005.20320 | 6 |
| Adobe Acrobat DC Pro and Standard 2020 Classic Track | 20.005.30748 | 6 |
| Adobe Acrobat Reader 2020 MUI – Classic Track | 20.005.30748 | 6 |
| Adobe Acrobat Reader DC | 24.005.20320 | 6 |
| Adobe Acrobat Reader DC | 24.005.20320! | 6 |
| Adobe Acrobat Reader DC – Multilingual (MUI) | 24.005.20320 | 6 |
| Adobe Reader DC | 24.005.20320 | 6 |
| Apache Tomcat 10 | 10.1.34 | 3 |
| Apache Tomcat 11 | 11.0.2 | 3 |
| Apache Tomcat 9 | 9.0.98 | 3 |
| Brave Browser | 1.73.97 | 1 |
| Chef Infra Client | 18.6.2 | 3 |
| Chef Infra Client for Windows 10 | 18.6.2 | 3 |
| Chef Infra Client for Windows 11 | 18.6.2 | 3 |
| Chef Infra Client for Windows Server 2016 | 18.6.2 | 3 |
| Chef Infra Client for Windows Server 2019 | 18.6.2 | 3 |
| Chef Infra Client for Windows Server 2022 | 18.6.2 | 3 |
| Chef Workstation | 24.12.1073 | 9 |
| Chef Workstation for Windows | 24.12.1073 | 9 |
| Datadog Agent | 7.60.1 | 1 |
| Devolutions Remote Desktop Manager | 2024.3.20.0 | 1 |
| Foxit PDF Editor 12 | 12.1.9.15762 | 4 |
| Foxit PDF Editor 2024 | 2024.4.0.27683 | 5 |
| Foxit PDF Editor Pro 12 | 12.1.9.15762 | 4 |
| Foxit PDF Reader | 2024.4.0.27683 | 5 |
| Google Chrome for Business | 131.0.6778.205 | 4 |
| Google Chrome for Business | 131.0.6778.140 | 2 |
| Google Chrome for Business | 131.0.6778.109 | 1 |
| Google Chrome for Education | 131.0.6778.205 | 4 |
| Google Chrome for Education | 131.0.6778.140 | 2 |
| Google Chrome for Education | 131.0.6778.109 | 1 |
| Mendix 8 | 8.18.33.53709 | 2 |
| Mendix 9 | 9.24.31.53726 | 1 |
| Microsoft .NET SDK 9.0 | 9.0.101 | 2 |
| Microsoft 365 Apps | 2402 (Build 16.0.17328.20670) | 4 |
| Microsoft 365 Apps | 2410 (Build 16.0.18129.20200) | 4 |
| Microsoft 365 Apps | 2411 (Build 16.0.18227.20162) | 4 |
| Microsoft 365 Apps | 16.92.24120731 | 2 |
| Microsoft Edge for Business | 131.0.2903.112 | 4 |
| Microsoft Edge for Business | 131.0.2903.99 | 2 |
| Microsoft Edge for Business | 131.0.2903.86 | 2 |
| Microsoft Remote Desktop | 1.2.5716.0 | 1 |
| Microsoft Windows Assessment and Deployment Kit (ADK) for Windows 11 | 10.1.26100.2454 | 1 |
| Microsoft Windows PE add-on for ADK for Windows 11 | 10.1.26100.2454 | 1 |
| Mozilla Thunderbird | 115.18.0 | 2 |
| Mozilla Thunderbird ESR 128 | 128.5.2 | 1 |
| Pale Moon | 33.5.0 | 2 |
| Python 3.12 | 3.12.8150.0 | 1 |
| Python 3.12 | 3.12.8 | 1 |
| Python 3.13 | 3.13.1 | 1 |
| Rider 2023 | 2023.3.6 | 1 |
| Tabby | 1.0.216 | 1 |
| TeamCity | 2024.12 | 9 |
Conclusion
Timely third-party patching remains crucial for maintaining the security and performance of your IT environment. The December 2024 updates addressed several critical vulnerabilities across a range of applications. By prioritizing these patches, you help protect your systems from potential exploits and ensure ongoing operational stability.
To further understand the impact of third-party patching on your security, explore the eBook Reduce Your Attack Footprint and follow our App Management and Patching thread.





























