ConfigMgr
Windows Authorization Access Group
Topics: ConfigMgr
I originally wrote this blog post when System Center 2012 R2 Configuration Manager’s (SCCM) Role-Based Administration (RBA) feature was relatively new. Since then, RBA is now widely used, so I thought that the time was right to re-visit this post. Here I’ll demonstrate how to add a SQL Server Reporting Services (SSRS) execution or computer account to the Windows Authorization Access Group. Doing this will allow SCCM’s RBA feature to work correctly with ConfigMgr / SCCM security users and roles.
In order for ConfigMgr to use the RBA feature within SSRS, the SSRS execution or computer account needs to determine who is running the report. Then it determines what SCCM rights the user has before displaying the report results.
In some cases, however, after upgrading to SCCM Current Branch, when you run a SSRS report you may receive the following error message:
The DefaultValue expression for the report parameter ‘UserTokenSIDs’ contains an error: The specified directory service attribute or value does not exist.
The solution to this problem is to add the execution or computer account to the Windows Authorization Access Group (Active Directory (AD) security group). The online documentation for Windows Authorization Access Group says:
Members of this group have access to the computed token GroupsGlobalAndUniversal attribute on User objects. Some applications have features that read the token-groups-global-and-universal (TGGAU) attribute on user account objects or on computer account objects in Active Directory Domain Services. Some Win32 functions make it easier to read the TGGAU attribute. Applications that read this attribute or that call an API (referred to as a function) that reads this attribute do not succeed if the calling security context does not have access to the attribute. This group appears as a SID until the domain controller is made the primary domain controller and it holds the operations master role (also known as flexible single master operations or FSMO).
In ConfigMgr terms this means that the SSRS execution account will be allowed to query for the, “…token GroupsGlobalAndUniversal attribute, this token is used to determine who is running the reports and therefore using RBA it can check to see what ConfigMgr objects (Collections, Software Update groups, etc.) the user executing the SSRS is allowed to access.”
Below are the steps and my screenshots from the original blog post. Even though I was using SCCM 2012 R2 at the time, the steps are still the same with Current Branch.
How to Add an Execution or Computer Account to the Windows Authorization Access Group
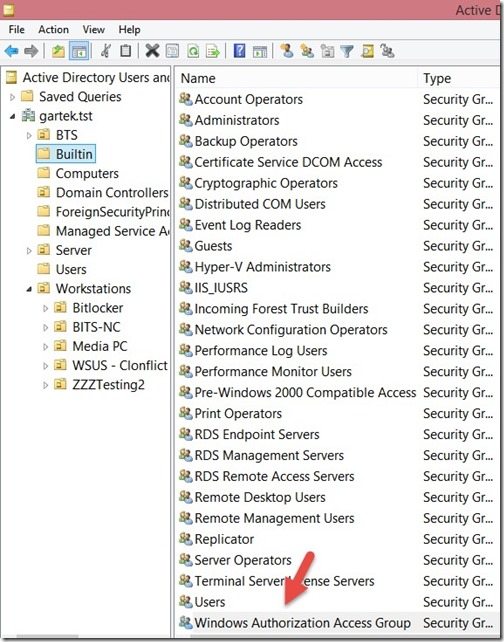
Open Active Directory Users and Computers (ADUC), and browse to the Builtin container. Double-click on the Windows Authorization Access Group.
Click on the Members tab.
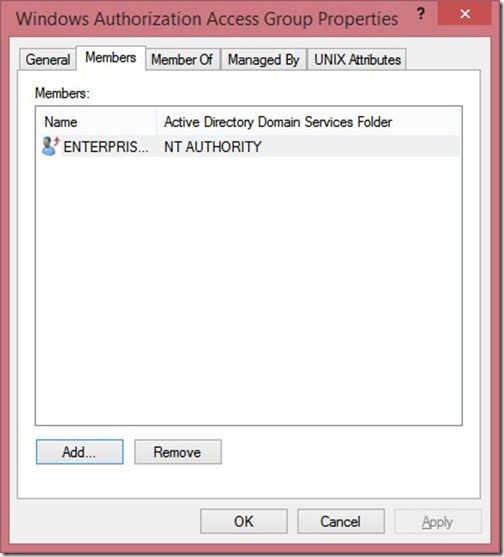
Click Add…
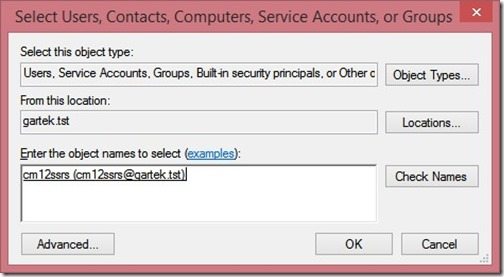
Add the execution or computer account and click OK twice to return back to the ADUC.
From this point forward the ConfigMgr SSRS account will be able to read the access token from AD and the reports will work correctly.
If you have any questions, please feel free to contact me @GarthMJ.
Do you have an idea for a blog post about a System Center Configuration Manager query or reporting topic? Let me know. Your idea might become the focus of my next blog post!
Additional ConfigMgr Resources
Learn more about how to better use ConfigMgr.
Overview
Inventory
Reporting
- How Can I Install Report Builder?
- How to Install a SCCM Reporting Services Point
- Dynamic Images to SSRS Report for SCCM
- Editing SCCM Reports with Report Builder
- Fixing the SCCM Reporting Services Point
Scripting
Security/Permissions
Software
External Integration



































