Application Management and Patching
March 2025 Third-Party Patches: Notable Vulnerabilities and Updates
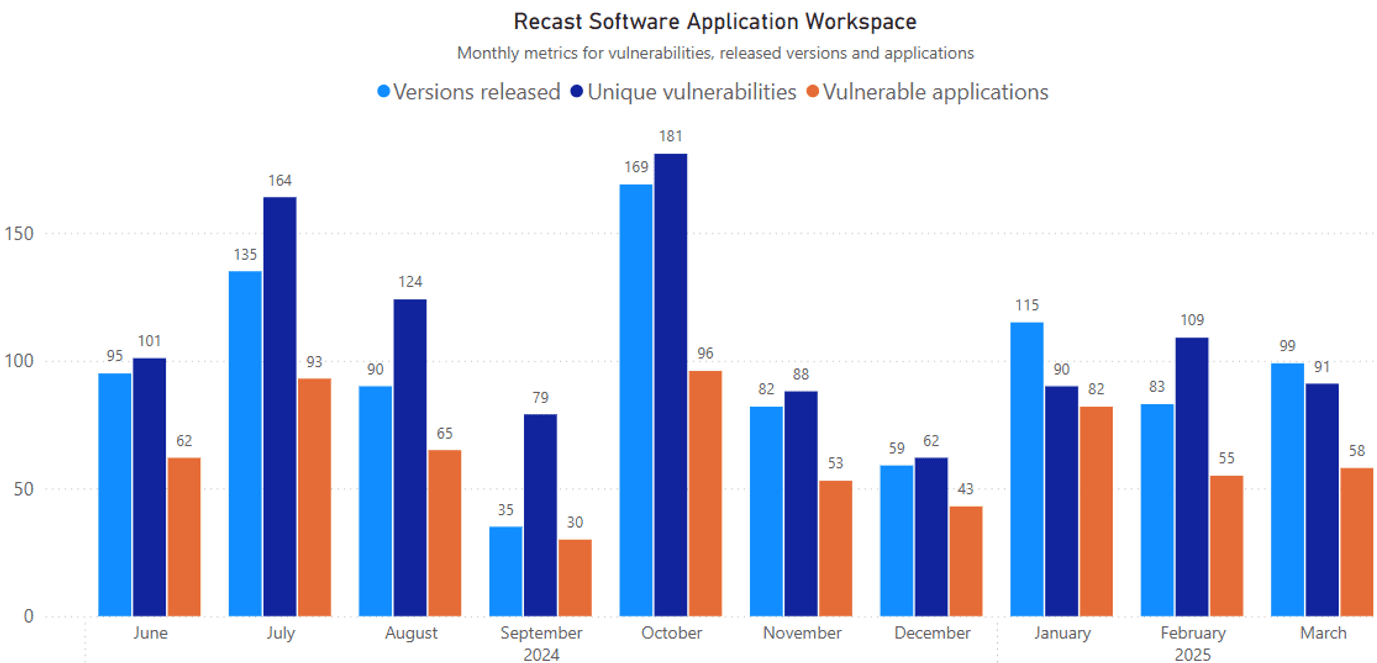
Key numbers have remained stable over the past three months. Metrics show that 58 vulnerable applications were remediated using 99 patches. In total, these updates addressed 91 unique vulnerabilities.
Notable Vulnerabilities in March 2025 Third-Party Patches
In March, several zero-day vulnerabilities were patched, and nine vulnerabilities were classified as critical. VMware Workstation Player 17 was affected by two zero-day vulnerabilities: CVE-2025-22224 and CVE-2025-22226. A malicious actor with local administrative privileges on a virtual machine could exploit CVE-2025-22224 to execute code as the VMX process on the host. Under similar conditions, CVE-2025-22226 can be exploited to leak memory from the VMX process. Other VMWare products were also affected. For more details, refer to the Security Advisory Security Advisory released by Broadcom.
CVE-2025-2783 is a zero-day vulnerability that affects Chromium-based products. An incorrect handle in the Mojo component of Google Chrome on Windows (versions earlier than 134.0.6998.177) allowed a remote attacker to escape the sandbox via a malicious file. This vulnerability also affects Microsoft Edge and Vivaldi browsers. There is no indication that Brave Browser addressed this vulnerability in March. CVE-2025-24201 is another zero-day vulnerability affecting Chromium-based browsers, remediated by Brave Browser, Google Chrome, Microsoft Edge, and Vivaldi in March.
Snagit released a patch addressing the critical OpenSSL vulnerability CVE-2021-3711. Refer to their changelog for additional details.
Mozilla released an update to remediate the CVE-2025-1942 vulnerability affecting Firefox and Thunderbird. Refer to their security advisory for more information. Additionally, Mozilla addressed a second critical vulnerability, CVE-2025-1941, in Firefox. More details are available in their security advisory.
Critical vulnerability CVE-2025-27832 affects Ghostscript. In Artifex Ghostscript versions prior to 10.05.0, a compression buffer overflow was discovered in the NPDL device for the file contrib/japanese/gdevnpdl.c. More details are available in their bug tracker. Additionally, critical vulnerabilities CVE-2025-27831, CVE-2025-27836, and CVE-2025-27837 affect Artifex Ghostscript versions prior to 10.05.0. Refer to the respective bug tracker pages for more information:
- https://bugs.ghostscript.com/show_bug.cgi?id=708132
- https://bugs.ghostscript.com/show_bug.cgi?id=708192
- https://bugs.ghostscript.com/show_bug.cgi?id=708238
Browser Security Updates in March 2025
| Browser | Vulnerabilities | Updates |
| Google Chrome | 16 | 4 |
| Microsoft Edge | 14 | 4 |
| Brave Browser | 16 | 3 |
| Pale Moon | 1 | 1 |
| Mozilla Firefox | 16 | 2 |
| Mozilla Firefox ESR 115 | 6 | 2 |
| Mozilla Firefox ESR 128 | 11 | 2 |
| Waterfox | 2 | 1 |
| Vivaldi | 2 | 2 |
Microsoft Product Updates Included in March 2025 Third-Party Patches
In addition to Edge, Microsoft issued security updates for several other products.
- Microsoft .NET Runtime 8.0
- Microsoft .NET Runtime 9.0
- Microsoft .NET SDK 8.0
- Microsoft .NET SDK 9.0
- Microsoft 365 Apps
- Microsoft ASP.NET Core Runtime 8.0
- Microsoft ASP.NET Core Runtime 9.0
- Microsoft ASP.NET Core Runtime Hosting Bundle 8.0
- Microsoft ASP.NET Core Runtime Hosting Bundle 9.0
- Microsoft Azure CLI
- Microsoft Visual Studio 2019 Enterprise
- Microsoft Visual Studio 2019 Professional
- Microsoft Visual Studio 2022 Enterprise
- Microsoft Visual Studio 2022 Professional
- Microsoft Visual Studio Feedback Client 2017
- Microsoft Visual Studio Team Explorer 2019
- Microsoft Windows Desktop Runtime 8.0
- Microsoft Windows Desktop Runtime 9.0
Detailed List of March 2025 Third-Party Patches
For a complete list of applications, versions, and the number of remediated vulnerabilities, see the table below generated using Application Workspace data.
| ProductName | VersionName | Vulnerabilities remediated |
| Adobe Acrobat DC | 25.001.20432 | 10 |
| Adobe Acrobat DC Pro and Standard 2020 Classic Track | 20.005.30763 | 10 |
| Adobe Acrobat Reader 2020 MUI – Classic Track | 20.005.30763 | 10 |
| Adobe Acrobat Reader DC | 25.001.20432 | 10 |
| Adobe Acrobat Reader DC – Multilingual (MUI) | 25.001.20432 | 10 |
| Adobe Reader DC | 25.001.20432 | 10 |
| Brave Browser | 1.76.74 | 6 |
| Brave Browser | 1.76.80 | 1 |
| Brave Browser | 1.76.73 | 9 |
| Caphyon Advanced Installer | 22.5 | 1 |
| Coder | 2.19.1 | 1 |
| Docker Desktop | 4.39.0 | 1 |
| Docker Desktop | 4.39.0.184744 | 1 |
| Electron | 32.3.3 | 2 |
| Electron | 34.3.4 | 1 |
| Electron | 33.4.6 | 1 |
| Electron | 33.4.3 | 3 |
| Ghostscript | 10.05.0 | 8 |
| Gitleaks | 8.24.2 | 1 |
| Google Chrome for Business | 134.0.6998.118 | 1 |
| Google Chrome for Business | 134.0.6998.178 | 1 |
| Google Chrome for Business | 134.0.6998.89 | 5 |
| Google Chrome for Business | 134.0.6998.36 | 9 |
| Google Chrome for Linux | 134.0.6998.117 | 1 |
| Google Chrome for Linux | 134.0.6998.88 | 4 |
| Google Chrome for Linux | 134.0.6998.35 | 9 |
| Google Chrome for Mac | 134.0.6998.118 | 1 |
| Google Chrome for Mac | 134.0.6998.89 | 5 |
| Google Chrome for Mac | 134.0.6998.45 | 9 |
| Google Go Programming Language 1.23 | 1.23.7 | 1 |
| Google Go Programming Language 1.24 | 1.24.1 | 1 |
| IBM Semeru Runtime Open Edition JDK 23 | 23.0.1.11 | 1 |
| IBM Semeru Runtime Open Edition JRE 23 | 23.0.1.11 | 1 |
| Mendix 10 | 10.21.0.64362 | 1 |
| Microsoft .NET Runtime 8.0 | 8.0.14.34611 | 1 |
| Microsoft .NET Runtime 8.0 | 8.0.14 | 1 |
| Microsoft .NET Runtime 9.0 | 9.0.3 | 1 |
| Microsoft .NET SDK 8.0 | 8.0.407 | 1 |
| Microsoft .NET SDK 8.0 | 8.4.725.11310 | 1 |
| Microsoft .NET SDK 9.0 | 9.0.202 | 1 |
| Microsoft .NET SDK 9.0 | 9.0.201 | 1 |
| Microsoft 365 Apps | 2408 (Build 16.0.17928.20468) | 11 |
| Microsoft 365 Apps | 2501 (Build 16.0.18429.20200) | 11 |
| Microsoft 365 Apps | 2502 (Build 16.0.18526.20168) | 11 |
| Microsoft 365 Apps | 16.95.25030928 | 8 |
| Microsoft ASP.NET Core Runtime 8.0 | 8.0.14.25112 | 1 |
| Microsoft ASP.NET Core Runtime 8.0 | 8.0.14 | 1 |
| Microsoft ASP.NET Core Runtime 9.0 | 9.0.3 | 1 |
| Microsoft ASP.NET Core Runtime Hosting Bundle 8.0 | 8.0.14.25112 | 1 |
| Microsoft ASP.NET Core Runtime Hosting Bundle 9.0 | 9.0.3 | 1 |
| Microsoft Azure CLI | 2.70.0 | 1 |
| Microsoft Edge Beta | 134.0.3124.66 | 4 |
| Microsoft Edge Beta | 134.0.3124.51 | 10 |
| Microsoft Edge Beta | 134.0.3124.62 | 5 |
| Microsoft Edge for Business | 134.0.3124.66 | 4 |
| Microsoft Edge for Business | 134.0.3124.83 | 1 |
| Microsoft Edge for Business | 134.0.3124.93 | 1 |
| Microsoft Edge for Business | 134.0.3124.51 | 8 |
| Microsoft Edge for Business for Linux | 134.0.3124.83 | 1 |
| Microsoft Edge for Business for Linux | 134.0.3124.68 | 4 |
| Microsoft Edge for Business for Linux | 134.0.3124.51 | 10 |
| Microsoft Edge for Business for Mac | 134.0.3124.83 | 1 |
| Microsoft Edge for Business for Mac | 134.0.3124.51 | 7 |
| Microsoft Edge for Business for Mac | 134.0.3124.62 | 5 |
| Microsoft Visual Studio 2019 Enterprise | 16.11.35826.135 | 2 |
| Microsoft Visual Studio 2019 Professional | 16.11.35826.135 | 2 |
| Microsoft Visual Studio 2022 Enterprise | 17.8.35827.206 | 3 |
| Microsoft Visual Studio 2022 Enterprise | 17.10.35827.194 | 3 |
| Microsoft Visual Studio 2022 Enterprise | 17.12.35827.183 | 3 |
| Microsoft Visual Studio 2022 Enterprise | 17.13.35828.75 | 3 |
| Microsoft Visual Studio 2022 Professional | 17.8.35827.206 | 3 |
| Microsoft Visual Studio 2022 Professional | 17.10.35827.194 | 3 |
| Microsoft Visual Studio 2022 Professional | 17.12.35827.183 | 3 |
| Microsoft Visual Studio 2022 Professional | 17.13.35828.75 | 3 |
| Microsoft Visual Studio Feedback Client 2017 | 15.9.35826.203 | 1 |
| Microsoft Visual Studio Team Explorer 2019 | 16.11.35826.135 | 2 |
| Microsoft Windows Desktop Runtime 8.0 | 8.0.14.34613 | 1 |
| Microsoft Windows Desktop Runtime 9.0 | 9.0.3 | 1 |
| Mozilla Firefox | 136.0.4 | 1 |
| Mozilla Firefox | 136.0 | 15 |
| Mozilla Firefox ESR 115 | 115.21.1 | 1 |
| Mozilla Firefox ESR 115 | 115.21.0 | 5 |
| Mozilla Firefox ESR 128 | 128.8.1 | 1 |
| Mozilla Firefox ESR 128 | 128.8.0 | 10 |
| Mozilla Thunderbird | 136.0 | 11 |
| Mozilla Thunderbird | 136.0 | 13 |
| Mozilla Thunderbird ESR 128 | 128.8.0 | 10 |
| Pale Moon | 33.6.1 | 1 |
| Snagit 2022 | 2022.2.9 | 2 |
| Snagit 2025 | 2025.1.0 | 1 |
| TeamCity | 2025.03 | 3 |
| Termius | 9.16.0 | 1 |
| Termius | 9.16.0.0 | 1 |
| The Document Foundation LibreOffice 25 | 25.2.1.2 | 1 |
| Vivaldi | 7.2.3621.71 | 1 |
| Vivaldi | 7.1.3570.60 | 1 |
| VMware Workstation Player 17 | 17.6.3.24583834 | 2 |
| VMware Workstation Pro 17 | 17.6.3.24583834 | 2 |
| Waterfox | 6.5.5 | 2 |
Conclusion
Timely third-party patching remains essential for protecting your IT environment. March 2025’s updates addressed significant vulnerabilities across major browsers and applications, strengthening your organization’s defense and operational stability. Stay tuned for next month’s insights.
For deeper insights into how third-party patch management reduces your attack surface, explore our eBook “Reduce Your Attack Footprint” or follow our App Management and Patching series.





























