Security and Compliance
Mandatory MFA for All Sign-Ins: Act Now
Topics: Security and Compliance
If you’ve logged into Azure or one of its admin portals recently, chances are you’ve come across a notification about multi-factor authentication (MFA). But what’s the deal? Why is Microsoft enforcing this now, and what does it mean for you?
Microsoft is making multi-factor authentication (MFA) mandatory for all sign-ins. Yes, you read that correctly: every account is affected, including admin and even break-glass (emergency access) accounts. Why is this crucial? This move is all about boosting security, protecting accounts from cyber threats, and ensuring compliance with industry regulations. According to Microsoft research, MFA can prevent over 99.2% of account compromise attacks, making it an essential step in securing your digital assets.
The MFA Rollout Plan
Microsoft began rolling out MFA in October last year, dividing the process into two phases. It’s time to act now!
Phase 1: October 2024
MFA will become a requirement for signing into the Azure portal, Microsoft Entra admin center, and Intune admin center. The rollout will happen gradually for all tenants worldwide.
Phase 2: Early 2025
In the next phase, Microsoft will extend MFA enforcement to Azure CLI, Azure PowerShell, the Azure mobile app, and Infrastructure as Code (IaC) tools.
For more information about Microsoft’s planning, visit this article.
What Does This Really Mean?
Phase 2 is officially here, and that means that there is no time to waste. Make sure your teams are aware of these changes so they can adapt smoothly once enforcement kicks in.
I know mandatory MFA might seem like extra work for your organization. But in reality, it’s a small price to pay for significantly stronger security. Cyber threats evolve every day, and Microsoft is taking proactive steps to keep users safe and ahead of the curve.
Now, the focus shifts to Azure, Azure PowerShell, and Infrastructure as Code (IaC) tools. Many scripts that automate tasks in PowerShell, Azure Automation, and IaC tools rely on special service accounts or user identities. However, these are no longer recommended for automation. Instead, they should be transitioned to managed identities and service principals (also known as Workload Identities).
The good news is that managed identities and service principals are not affected by MFA enforcement in either phase. Making this shift now will help your organization stay compliant without disruption. Change can be challenging, but staying ahead of security threats is always worth it.
Is your team ready for Phase 2? Let’s make the transition smooth and secure!
The Impact of Mandatory MFA on User and Admin Accounts
By now, your organization has likely implemented MFA for both user and admin accounts. Why is this so crucial? Well, admin accounts usually have elevated privileges and access to sensitive information, making them prime targets for cyberattacks. Enforcing MFA on these accounts adds an essential extra layer of protection against unauthorized access.
But security isn’t just about implementation; it’s also about monitoring. Measuring is key, so let’s check your organization’s MFA status. With the simple steps below, you can quickly generate a report and even download it if needed.
Steps to Check MFA Enrollment:
- Log in to the Azure Portal using an account with Global Administrator rights.
- Navigate to the Microsoft Entra ID service.
- Go to Manage >> Security.
- Then, go to Manage >> Authentication Methods.
- Finally, head over to Monitoring and click on User Registration Details.
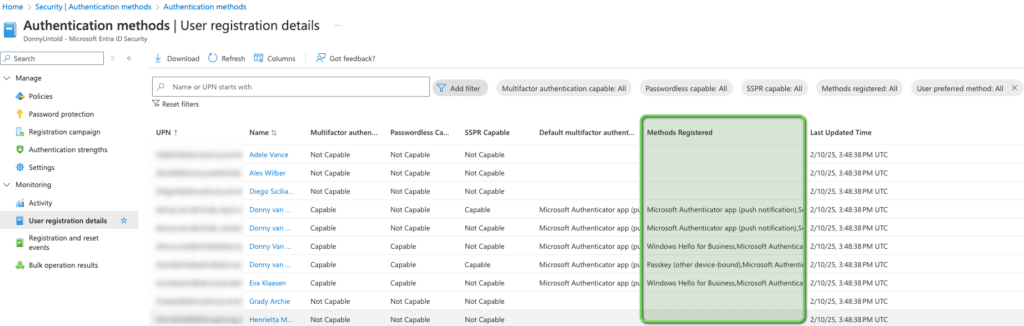
That’s it! You’ll now see a report detailing which users are registered with which authentication method for MFA. If you find accounts that don’t have MFA enabled, take immediate action! Any unprotected admin account is a potential risk to your environment.
Break Glass (Emergency Access) Accounts
When it comes to securing my special accounts, I personally prefer using a FIDO2 security key. I use a YubiKey 5C NFC with USB-C because it works best with my MacBook. If you’re considering a similar approach for your organization, here are some strong reasons why this method makes sense:
- Secure and Passwordless: Passkeys eliminate the need for passwords entirely, offering a seamless and highly secure authentication experience. No more worrying about password leaks or brute-force attacks!
- Resistant to Phishing & Credential Theft: Break glass (emergency access) accounts are prime targets for attackers. FIDO2 passkeys are tied to a specific device and require biometric authentication or a PIN, making them virtually impossible to steal remotely.
- No Dependency on Mobile MFA Methods: One of the biggest advantages of using a FIDO2 key is that it removes the dependency on mobile phones for MFA. This is particularly useful for break glass accounts, which shouldn’t be tied to a personal device. A security key like a YubiKey operates independently and can be stored securely.
- Compliance & Security Best Practices: Passkeys align perfectly with Zero Trust principles and meet security standards like NIST and NIS2, ensuring compliance with modern regulations. If security compliance is a priority for your organization, this is a big plus.
- Seamless Integration with Microsoft Entra ID: Microsoft fully supports FIDO2 authentication, making it easy to log in securely to Entra ID without relying on riskier MFA methods like SMS or mobile authentication apps.
Note: If a user has not yet set up any authentication methods for MFA, the FIDO2 option will not appear, as Microsoft has not yet designated it as a “Sign-in Method.” I have configured the system so that only SMS, the Authenticator App, and FIDO2 are allowed for a specific Entra group. Even if a user belongs to this group, one of the following methods must be set up first: the Microsoft Authenticator app, a hardware token, or telephone verification.
The FIDO2 option will only appear after one of the default sign-in methods (Phone or Authenticator) has been set up, as Microsoft currently allows only these methods by default. If the user does not want to set up another method, a workaround is to assign a Temporary Access Pass (TAP), which Microsoft counts as a sign-in method. Once the user logs in to mysignins.microsoft.com, they will be prompted to use the TAP, after which they can add a FIDO2 key. Ultimately, the TAP will expire according to your TAP policy, or it can be deleted manually after the FIDO2 key has been set.
Steps to Set FIDO2 key with TAP
- First, make sure that passkeys (FIDO2) are enabled within your organization
- Ensure that the Temporary Access Pass policy is enabled within Microsoft Entra ID
- Create a Temporary Access Pass for your break-glass or emergency access account.
- Log in to mysignins.microsoft.com/security-info and set up the FIDO2 key (in our case, a YubiKey) using the Temporary Access Pass.
Final Thoughts
The bottom line is that MFA isn’t optional—it’s essential. Microsoft’s phased rollout means now is the time to secure your sign-ins, shift to managed identities, and protect break-glass or emergency access accounts. Cyber threats aren’t slowing down, so neither should you. Stay ahead and stay protected!






























