Intune
Managing Application Installations on AVD Multi-Session Devices with Intune
Topics: Intune
Microsoft Intune simplifies application installations on AVD multi-session devices by allowing you to set requirement-based rules for installations. These rules can be based on OS and hardware factors (e.g., disk space, RAM, processor). For more advanced checks—such as validating files, registry settings, or using custom scripts—you can extend these rules with additional conditions.
Default Requirement Rules
Intune’s default requirement rules can be set based on the following criteria:
- Operating System Version
- Hardware Specifications
However, if you need to enforce custom conditions, such as checking for specific files or registry entries, you can do so by adding additional rules.
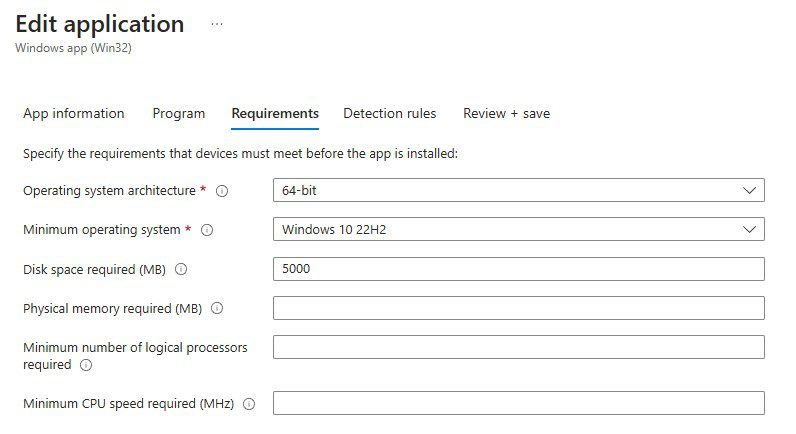
Custom Requirement Rules
Intune requirement rules operate with an AND logic, meaning that all conditions—such as file existence, registry settings, and script outputs—must be met for the application to install.
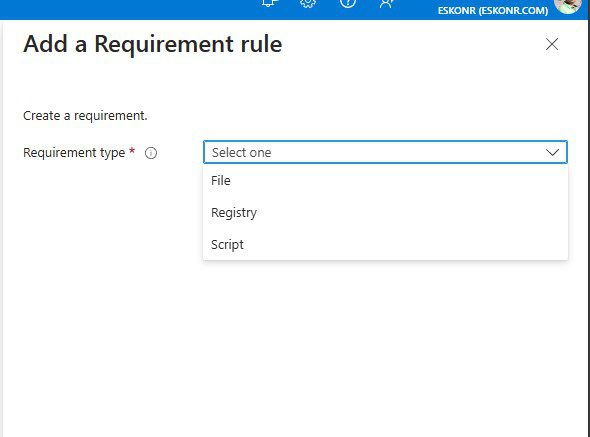
If you need to use an OR operator to allow for more flexible conditions (e.g., if any one of multiple checks is true), you will need to create a custom script.
Scenario: Handling AVD Multi-Session Devices
In this scenario, we manage Azure Virtual Desktop (AVD) multi-session devices with Intune. These devices usually have applications set up through MSI app attach or pre-installed in the base image. For more details about AVD multi-session and Intune support, visit Microsoft’s documentation here.
To prevent unintended installations on AVD multi-session devices—especially when targeting user groups in Intune—we need to ensure applications are only installed on non-multi-session devices.
Intune’s default requirement rules don’t allow you to select the operating system edition, a feature available in Microsoft Configuration Manager (ConfigMgr). This is where custom requirement rules become necessary.
Implementing a Custom Requirement Rule
To achieve this, we can use a PowerShell script to check if the OS is a multi-session version. If the OS is multi-session, the script will prevent the application from installing.
Below is a PowerShell script you can use to check if the OS is multi-session.
<#
.SYNOPSIS
This script checks if the operating system is a multi-session OS before proceeding with application installation using Intune.
.DESCRIPTION
The script queries the Win32_OperatingSystem class to determine if the OS is a multi-session version. If the OS caption includes the term "Multi-Session",
it indicates that the OS supports multiple user sessions, and the script exits with code 1. If the OS is not a multi-session version, the script exits with code 0.
File Name: RequirementRule-IsMultiSessionOS.ps1
#>
# Query the Win32_OperatingSystem class
$os = Get-WmiObject -Class Win32_OperatingSystem
# Check for multi-session OS
if ($os.Caption -match "Multi-Session") {
Write-Host "Multi-session OS"
exit 1
} else {
Write-Host "Not a multi-session OS"
exit 0
} How to Use This Script in Intune
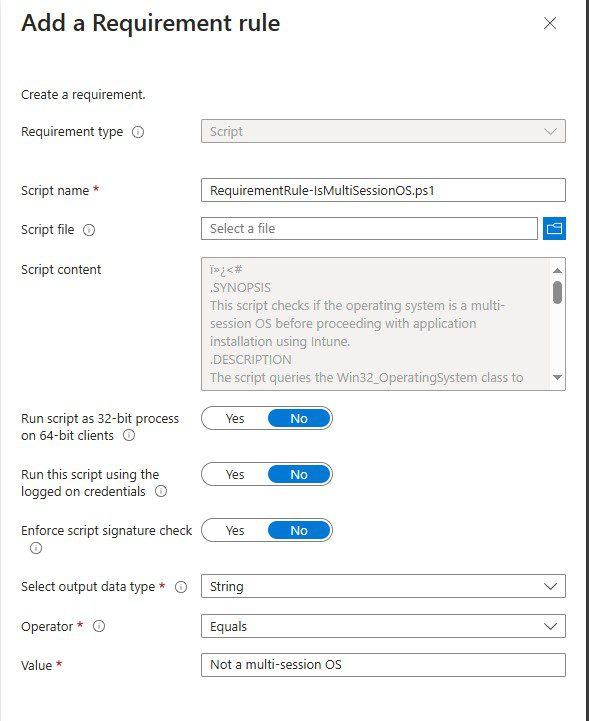
- Upload the Script: In your Win32 app configuration within Intune, add an additional requirement rule.
- Configure the Rule: Select the PowerShell file, set the data type to “String,” and input “Not a multi-session OS” as the value.
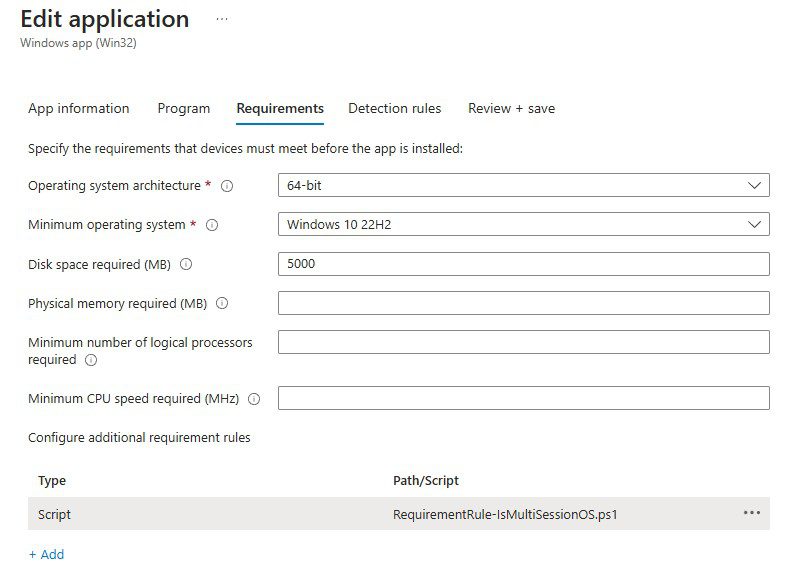
Ensuring Seamless Application Installations on AVD Multi-Session Instances
By integrating this PowerShell script into your Intune deployment, you can ensure applications are only installed on non-multi-session devices, effectively preventing unwanted installations on AVD environments.
References
https://learn.microsoft.com/en-us/mem/intune/fundamentals/azure-virtual-desktop-multi-session