Application Management and Patching
Bridging the Gap in Vulnerability Management
A recent discussion with a colleague sparked an important flashback. This past conversation had reshaped our collective understanding of third-party vulnerabilities and the intricacies of their disclosure timelines. The discussion had started thanks to an internal initiative to leverage the National Vulnerability Database (NVD) for monitoring new versions and vulnerabilities to then add to Application Manager, our third-party patching platform. However, it swiftly became apparent that direct information from vendor sites and official changelogs significantly outpaced NVD’s Data Feed, sometimes by weeks. Importantly, this observation is not a critique of the NVD, which plays a crucial role in the collection, analysis, and scoring of vulnerabilities, despite inherent delays in publication due to various constraints. However, the conversation did lead to some important conclusions and framework shifts.
Tenable’s insightful analysis from 2023, “Mind the Gap: A Closer Look at the Vulnerabilities Disclosed in 2022,” highlighted an average 45-day delay for the NVD to score and publish details about critical vulnerabilities, starting from when a vendor first publicly acknowledges them. Another source, the Ponemon Institute, found it takes organizations an average of 16 days to patch a critical vulnerability, while Verizon’s 2023 Data Breach Investigations Report indicated a median patch time of 49 days. While the timeframes vary, these reports collectively underscore the prolonged window of risk organizations face.
Then, in addition, Mandiant’s 2023 analysis, “Analysis of Time-to-Exploit Trends: 2021-2022,” revealed that the first month post-patch disclosure is the most critical, with 29 out of 93 n-day vulnerabilities being exploited within this timeframe. This data sets the stage for understanding the urgency in reducing vulnerability exposure time.
Visualizing the Vulnerability Risk
To illuminate the remediation timelines that organizations might experience, below we compare standard procedures against those enhanced by Recast Software’s solutions. Utilizing Tenable, Ponemon Institute, and Verizon’s findings, we landed on an average patch deployment timeframe of 32.5 days. With Application Manager by Recast, however, new vulnerabilities and their updated application versions are typically identified and released within 24-48 hours. Our January 2024 data for Application Manager showed an impressive average release time of just 0.42 days for packaging the latest versions, demonstrating our commitment to rapid response.
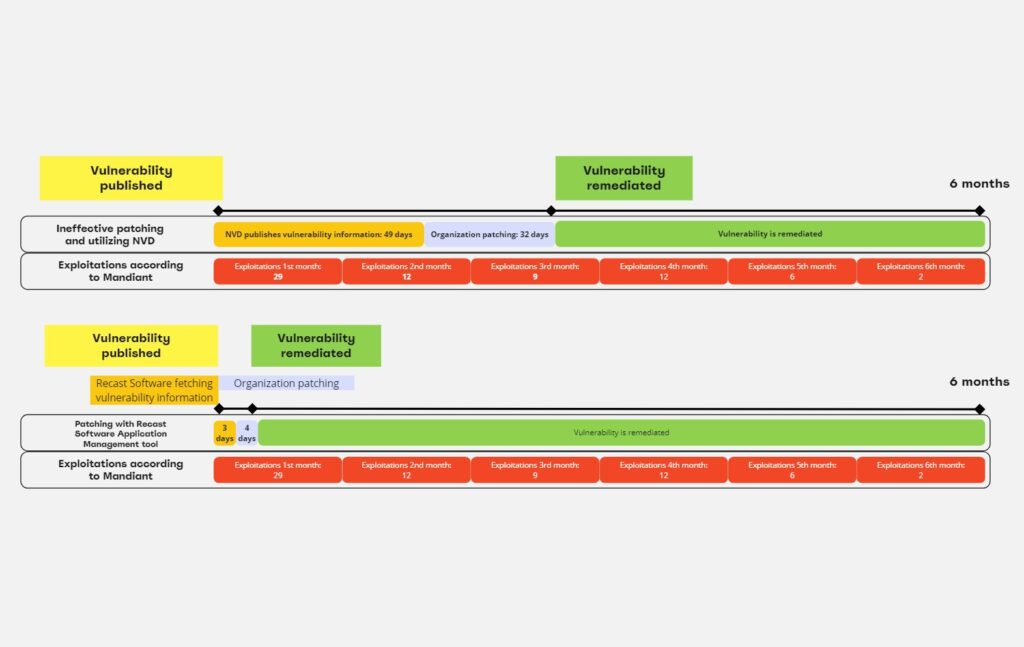
The above visualizations contrast these timelines, showing the efficiency gained with Application Manager. 94.8% of our Application Manager for Intune customers benefit from immediate patch deployment, highlighting our system’s capability to significantly reduce the window of vulnerability exposure. For the remaining 5.2% of customers, we saw an average delay of 7.4 days (which we’ve adjusted to 4 days above).
Close the Gap in Vulnerability Management
This comparative study highlights the importance of timely vulnerability management. Delays in receiving notifications from databases like NVD or in preparing and deploying patches can severely impact your ability to mitigate risks effectively. Through our innovative solutions, we offer a pathway to lead the race against exploitation, helping to ensure that your organization’s defenses are always a step ahead.































