ConfigMgr
Building a ConfigMgr Lab from Scratch: Step 3 – Certificate Authority
Topics: ConfigMgr
Building a ConfigMgr Lab from Scratch: Step 3
Adding a Certificate Authority
This post is completely optional for your environment.
You can do everything you want in your lab without this feature, but guess what, if you’re going to do anything that needs HTTPS, having your own Certificate Authority (CA) makes this so much slicker.
Creating a CA is straight forward. You pick the role and click next a few times. I’m adding it to my DC, as it’s an easy place to put it.
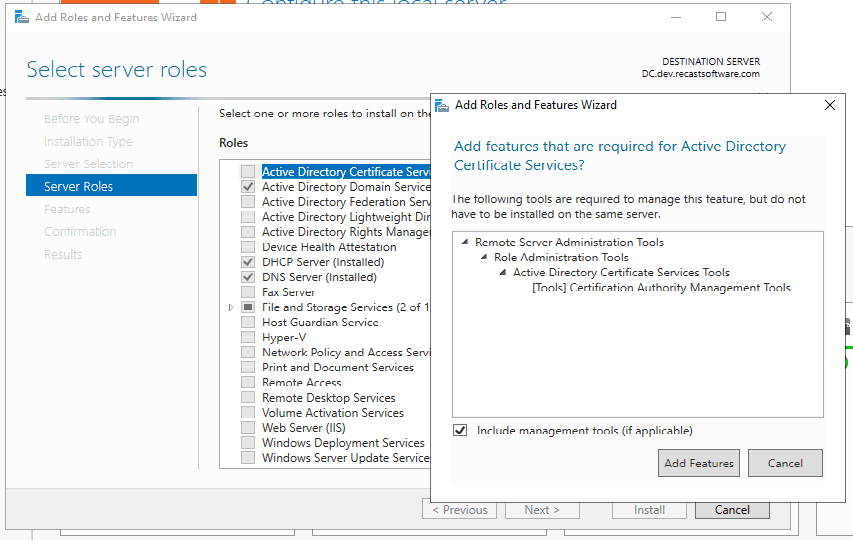
You’ll check the box “Active Directory Certificate Services, which will then pop up this dialog, click “Add Features.”
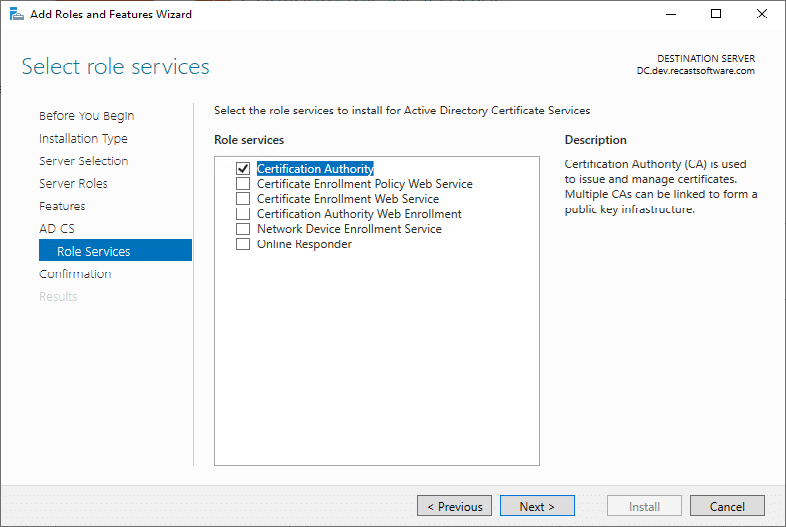
This is default.
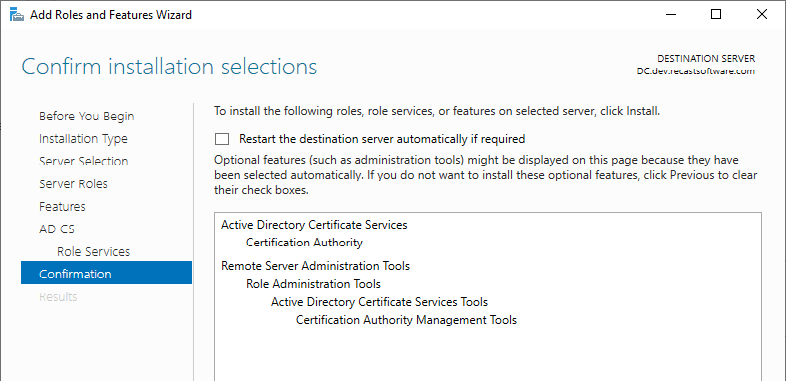
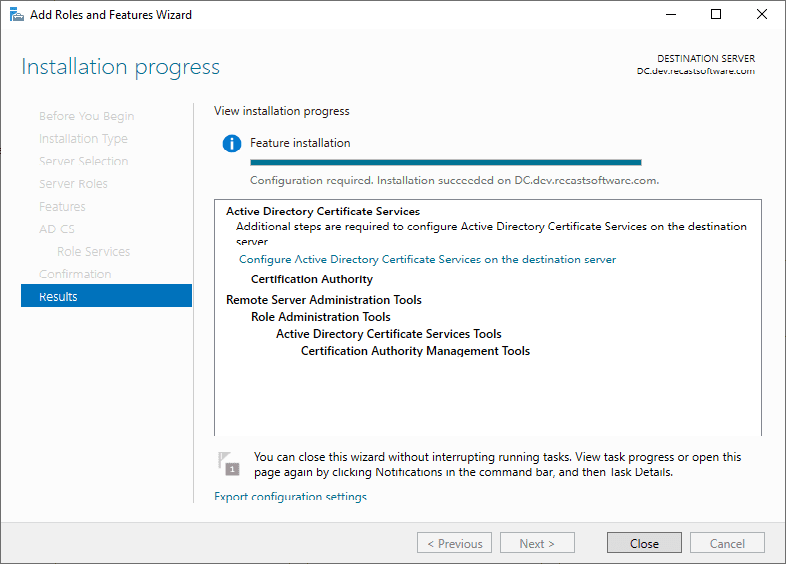
At this point, click “Configure AD CS on the destination server.
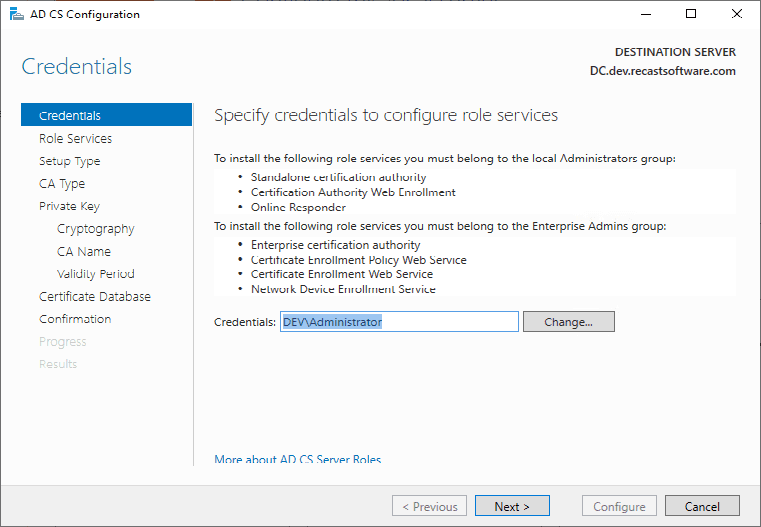
Defaults.
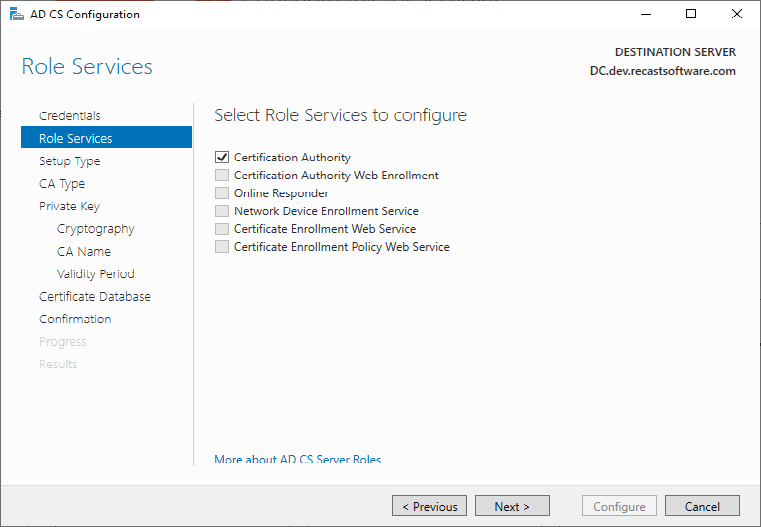
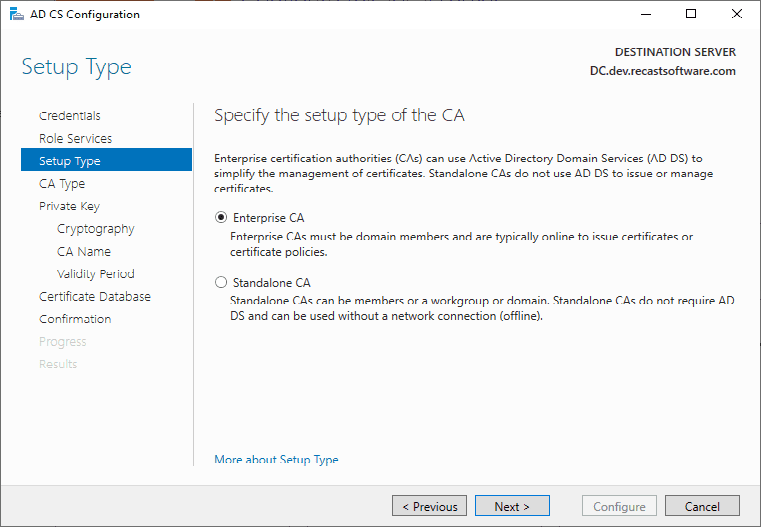
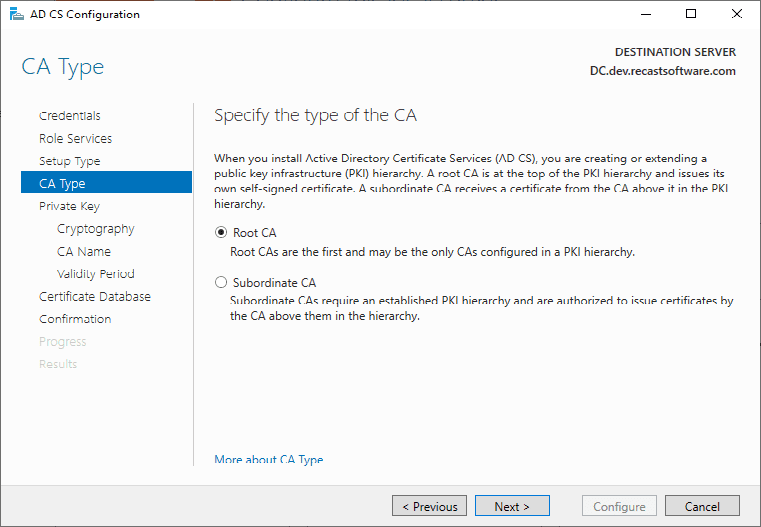
I left the defaults here.
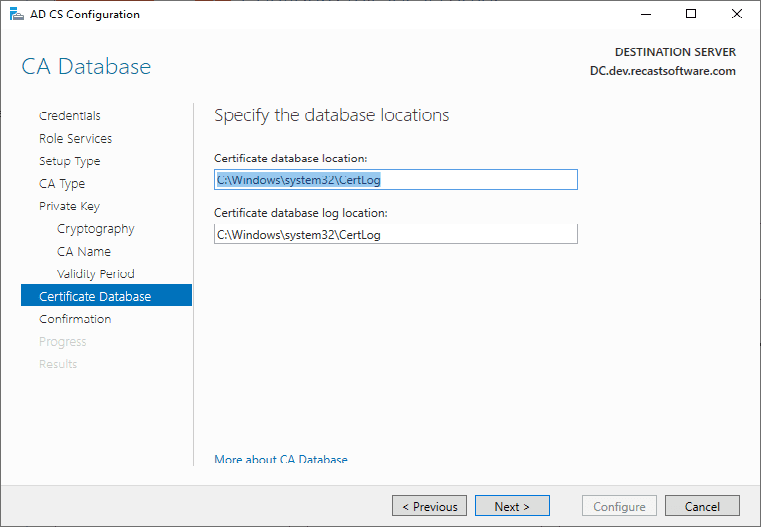
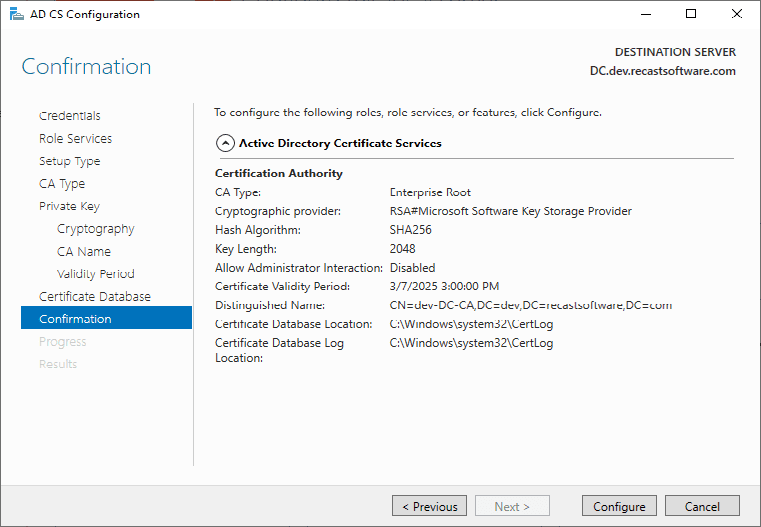
Ok, so now we have setup our CA & had it configured. Now let’s create a Cert Template. In this example, I’ll be creating a certificate template to be used with our Recast Management Server Web Server, which will basically be the same for any web server.
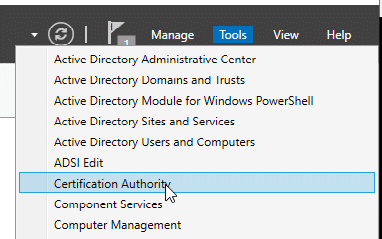
Launch Certification Authority from the Tools Menu.
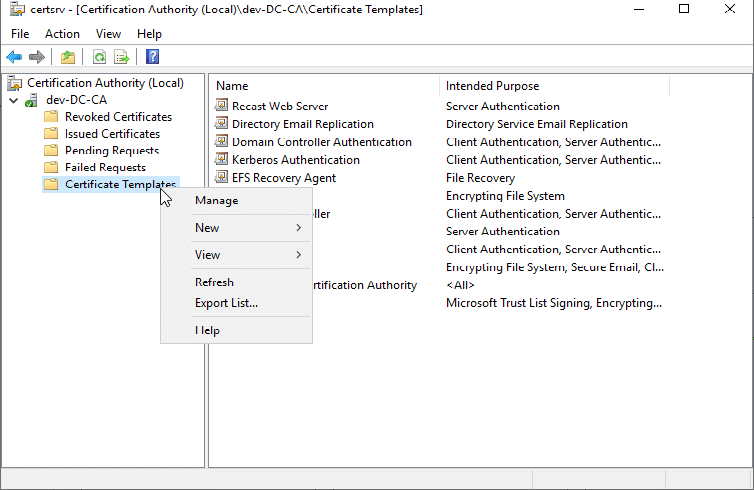
Right Click on Certificate Templates and choose Manage.
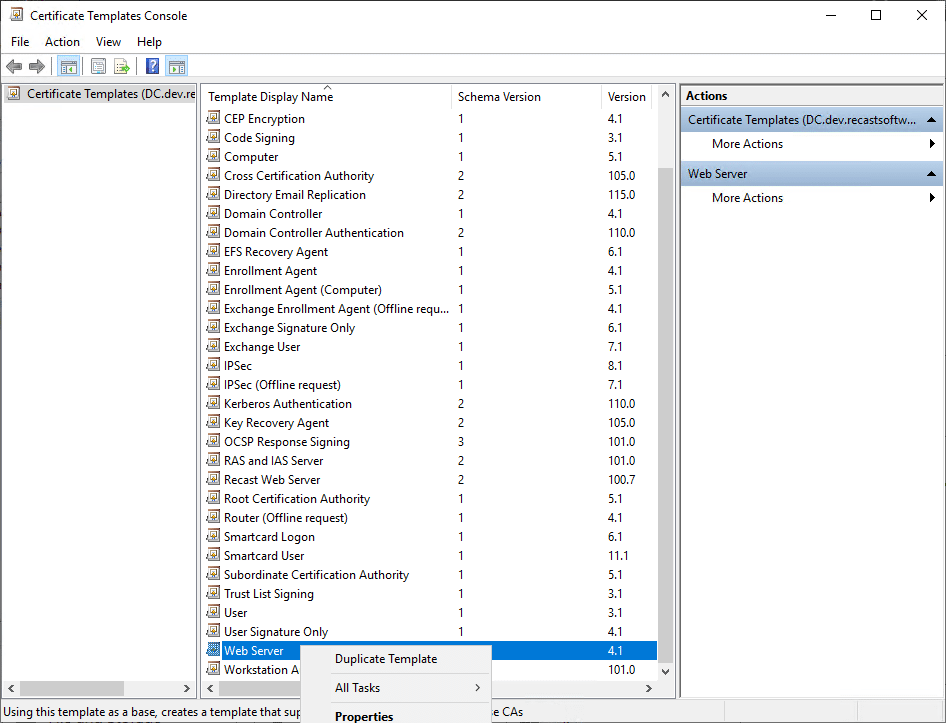
We’re going to make a duplicate of the Web Server Template to use.
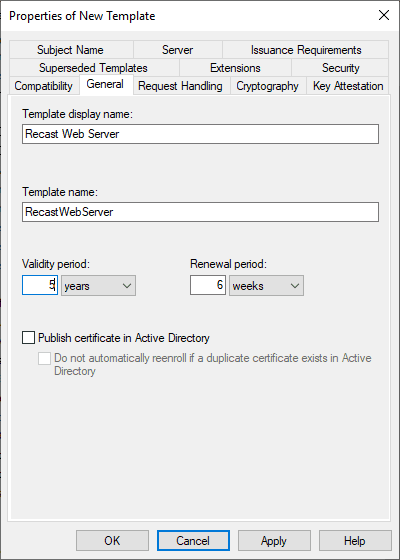
I’m going to name it Recast Web Server.
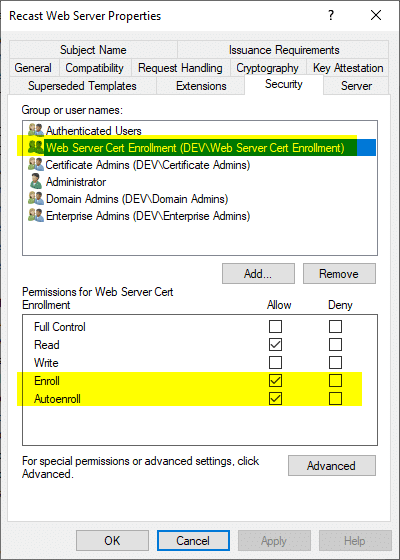
Under Security I added an AD Group “Web Server Cert Enrollment” and checked the boxes “Enroll & Autoenroll.”
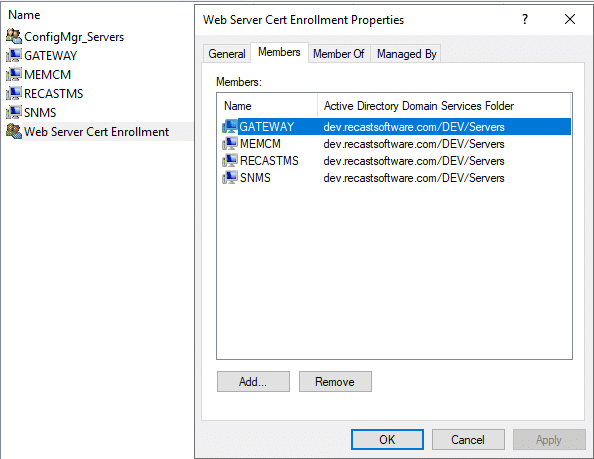
In AD, this is the group, and the members. I’ve added several servers that might need the cert and one that I know does for sure. Eventually all of these servers will automatically get the certificated because they are set to auto enroll.
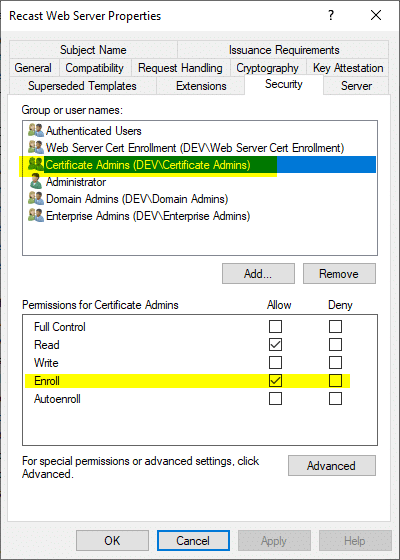
I also added Certificate Admins and checked the box for Enroll.
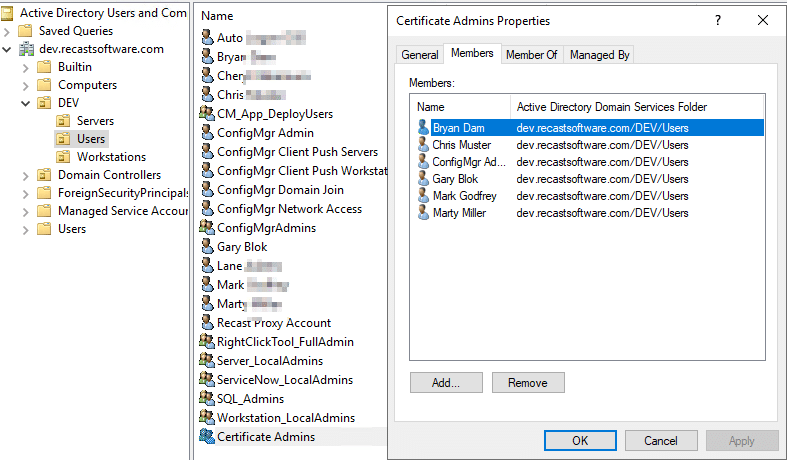
The Certificate Admins Group, anyone in this group has the ability to enroll this new certificate.
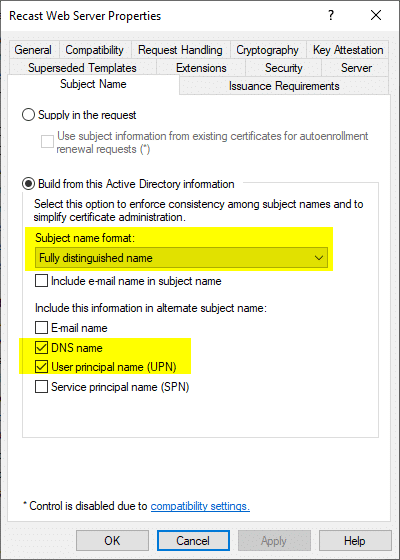
Now that this is done, you’ll have to Add these certs to “Certificate Templates” – Otherwise you might get this error:
“The requested certificate template is not supported by this CA. A valid certification authority (CA) configured to issue certificates based on this template cannot be located, or the CA does not support this operation, or the CA is not trusted.”
This drove me crazy for a bit, then realized I forgot a step. Any Templates you’ve duplicated and created that you want this CA to be able to give out, you’ll need to add here: [More Info]
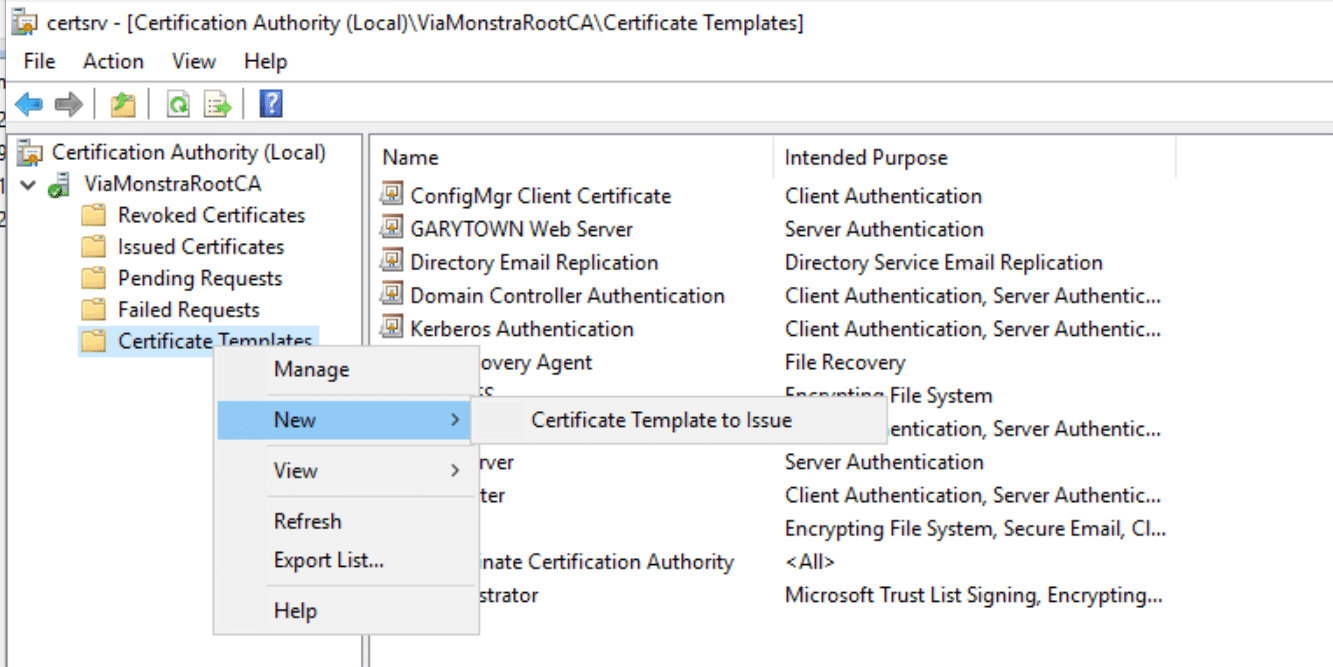
Sorry, the names changed. I noticed this after the original post and am appending this from my personal lab.
Now, on the server, you can enroll and add the certificate.
In this example I’ll be having the certificate enrolled on the Recast Management Server which hosts our Recast Enterprise Server Web Service.
Currently it’s using it’s self-issued certificate which causes clients to get a warning when you try to connect.
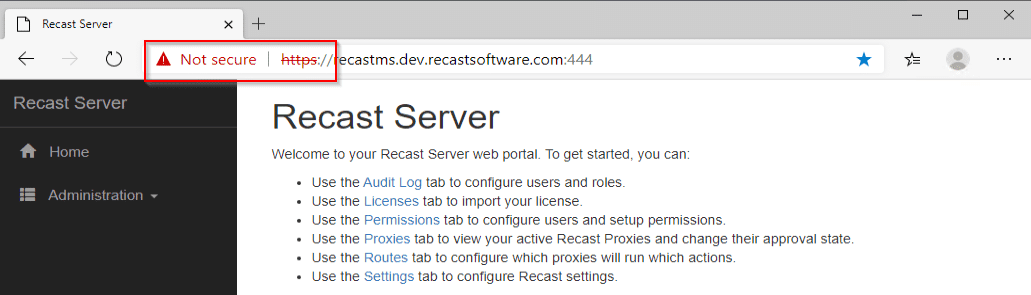
You can see here that while it’s HTTPS, it gives a “Not Secure” Warning.
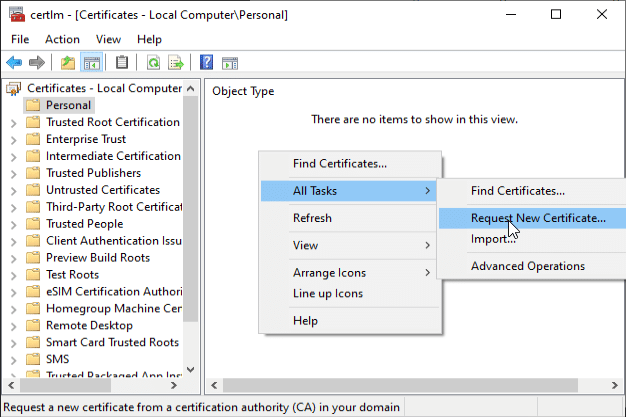
Go to “Manage Computer Certificates”. On Personal, right click and choose “All Tasks”, then “Request New Certificate.”
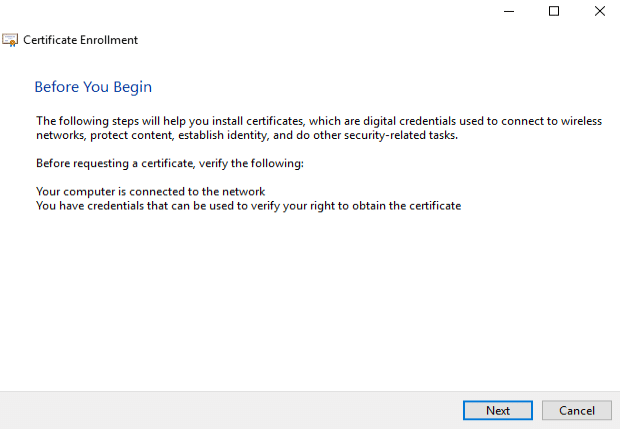
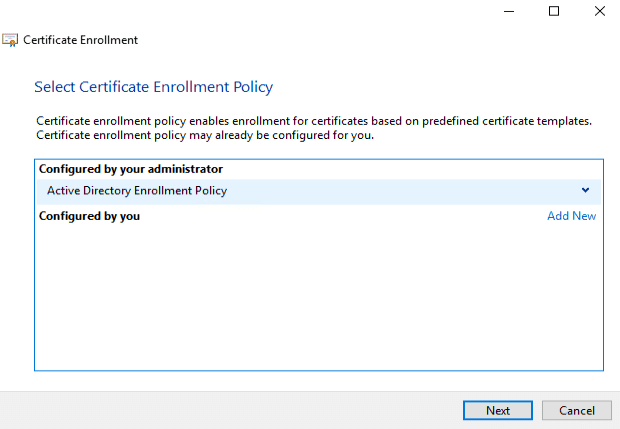
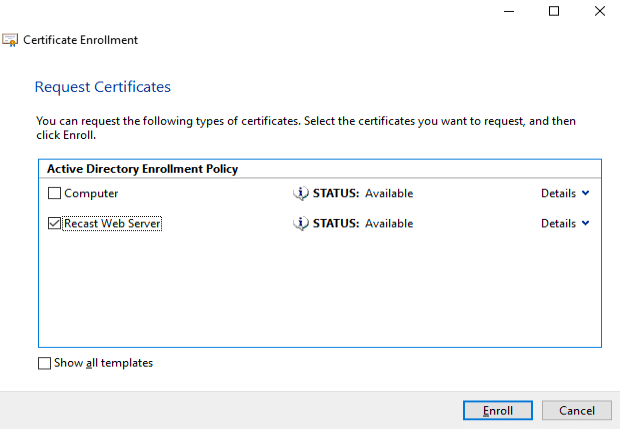
At this point you should see the “Recast Web Server” cert available.
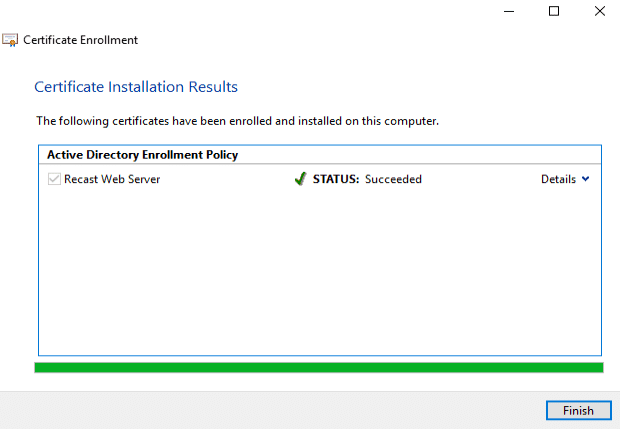
It enrolled successfully.
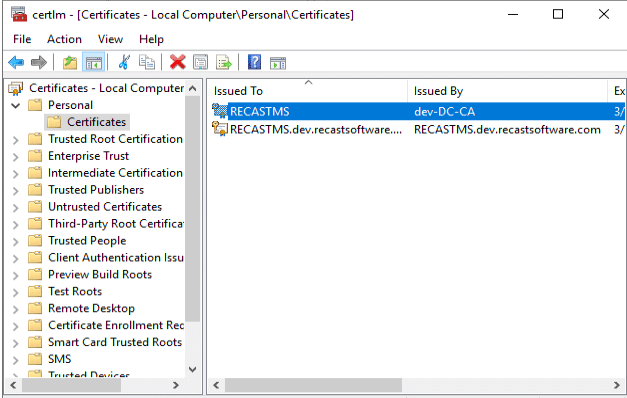
Now in the Certificates, you’ll see the cert that was issued by our CA.
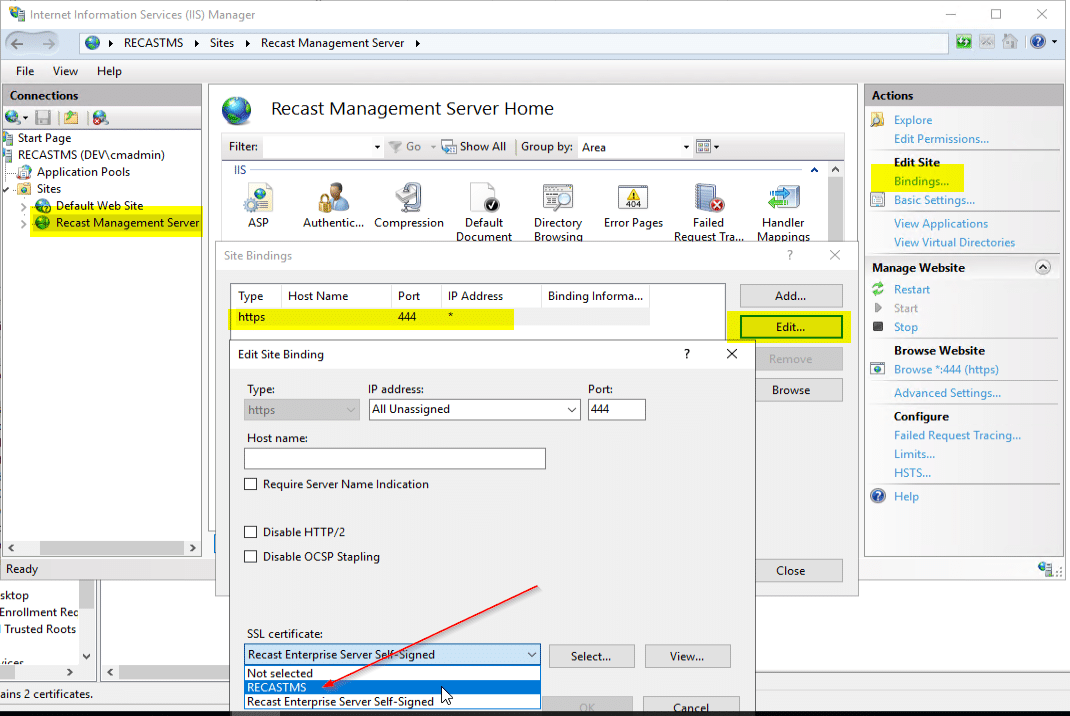
Now that we have the Cert available, let’s tell our Recast Server’s Site to use our new cert. Open up IIS, choose the Recast Management Server, click Bindings, then click “Edit” and choose the cert that was issued.
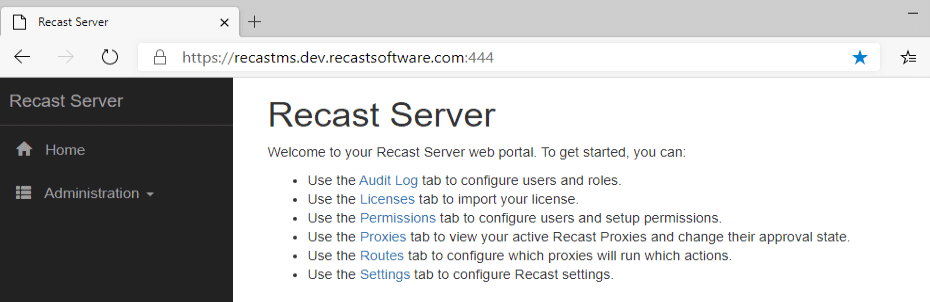
So now we have a CA setup and used it to improve the experience on our Recast Management Server. Long term plan is to use it to enable HTTPS only on our CM Server. We’ll get to that in a future post.
Building a ConfigMgr Lab from Scratch Series
Series Introduction – Building a CM Lab from Scratch
- Setting up your Domain Controller
- Creating a Router for your Lab using Windows Server
- Certificate Authority – On Domain Controller [Optional] – You are Here
- ConfigMgr Server Pre-Reqs (Windows Features)
- Configuration Settings (AD & GPOs)
- Source Server (File Share)
- ConfigMgr SQL Install
- ConfigMgr Install
- ConfigMgr Basic Settings
- ConfigMgr Collections & App Deployment
- ConfigMgr OSD
- ConfigMgr Reporting Services
- Cloud Management Gateway (CMG) – Certs PreReq
- Cloud Management Gateway (CMG) – Azure Subscription
- Azure Services Connection
- Setting up CMG in the Console
- Cloud Management Gateway (CMG) – Post CMG Config
- Cloud Management Gateway – Client CMG Endpoints






















