Today, we are going to learn about protecting company data on unmanaged iOS and iPadOS devices and how to set this up using Microsoft Intune. Note, I will refer only to iOS going forward, but this post applies to both iOS and iPadOS. We will be setting up guardrails for our data to ensure that company information remains secure while still providing personal access to organizational data for productivity.
Mobile Application Management (MAM) will be used for unmanaged devices, referred to as personal or BYOD (Bring Your Own Device) devices. These are devices over which your IT staff has no control over their settings.
Find my partner post Mobile Application Management for Android Devices with Intune here.
Understanding MAM and Intune’s Role
What Is MAM (Mobile Application Management)?
To provide a bit more context, let’s explore what MAM and App Protection Policies entail. MAM, also known as Mobile Application Management, refers to a suite of management features that empower administrators to publish, configure, and secure mobile applications.
The Importance of App Protection Policies in Intune
App Protection Policies within Intune are essentially a collection of rules designed to secure company data within an application by managing how data is accessed and shared. With these policies, administrators can enforce requirements such as a PIN to access the app and prevent the copying of organizational data to personal applications, among other security measures.
The Benefits of Implementing MAM with Intune
Enhanced Data Security – Provides a layer of security for organization data on unmanaged devices by setting policies to control how company data is accessed and shared within apps.
Increase Flexibility – Give your users access to company data such as Outlook, Excel etc. without having to enroll their devices under management.
Preparing for MAM Setup: What You Need
- Company Portal app or MS Authenticator App (broker app)
- Microsoft Intune License
- Entra ID P1 License
Step-by-Step Guide to Setting Up MAM for iOS Devices
Creating Your Conditional Access Policy
To begin protecting your data, start by creating a Conditional Access Policy in Microsoft Intune. Navigate to Microsoft Intune > Endpoint security > Conditional access > + Create new policy
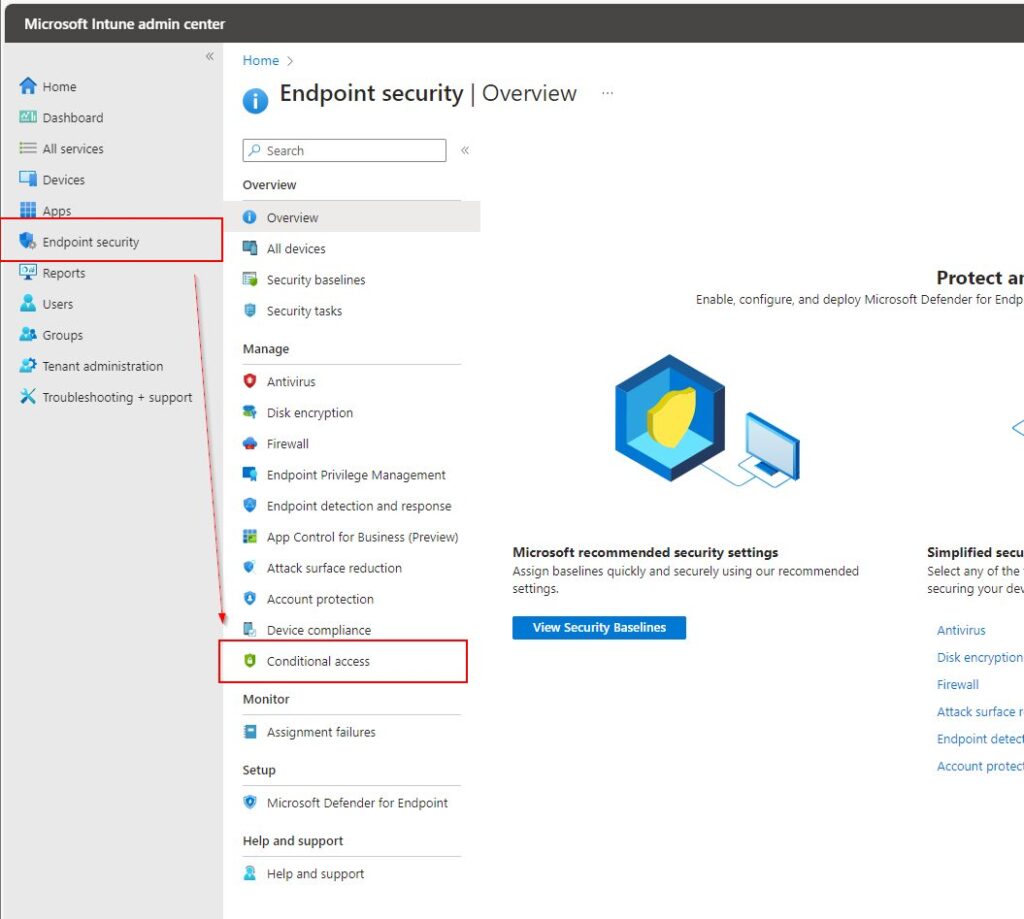
Create your Conditional Access Policy. Assign a descriptive name to the policy, such as “MAM for iOS.”
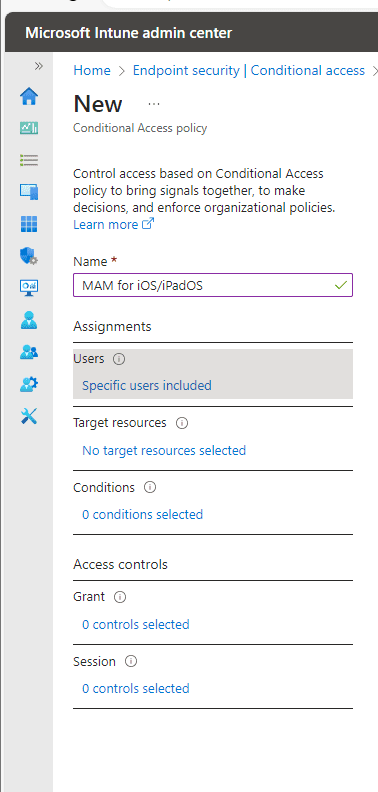
Assigning Your Policy to Groups
Select the group the best fits your needs. In my case, I will choose “App Protection Pilot Group” which has a single user account that I will use to demo later.
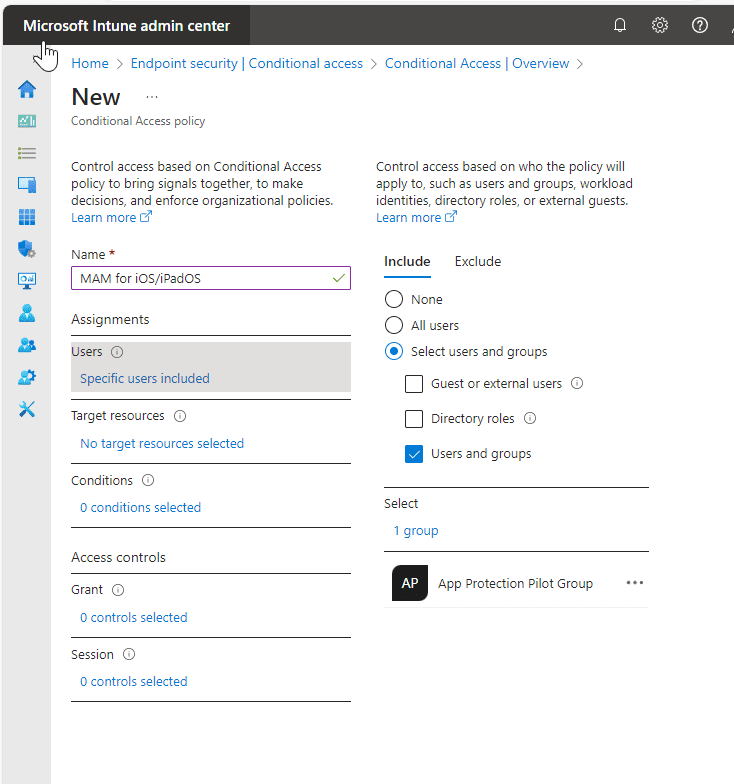
Selecting Targeted Resources and Conditions
Choose the resources to protect, such as “Cloud Apps” or specifically “Office 365.” You can also select All cloud apps to broaden your scope, but for simplicity’s sake I will select Office 365.
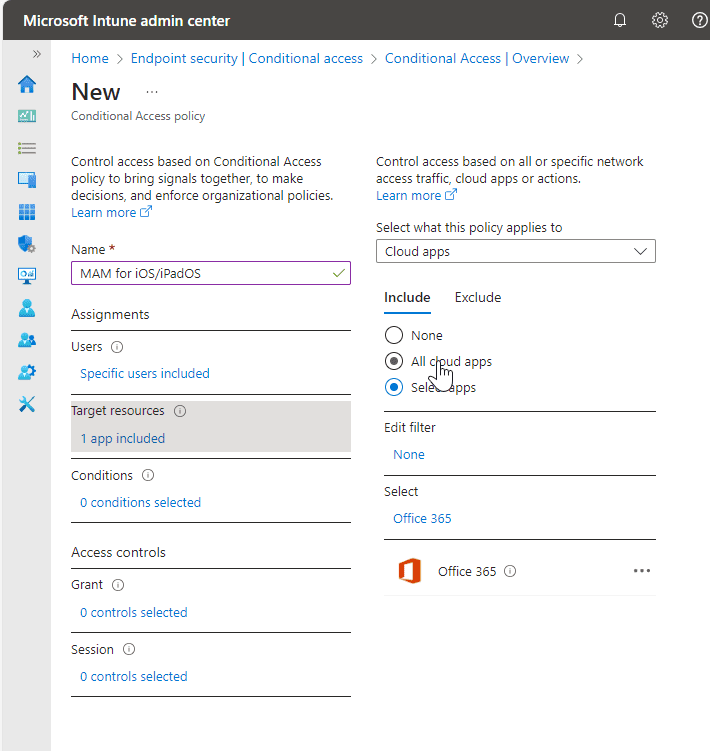
Conditions
Set the conditions targeting the Device Platform, as this will tell us the platform the user is signing in from.
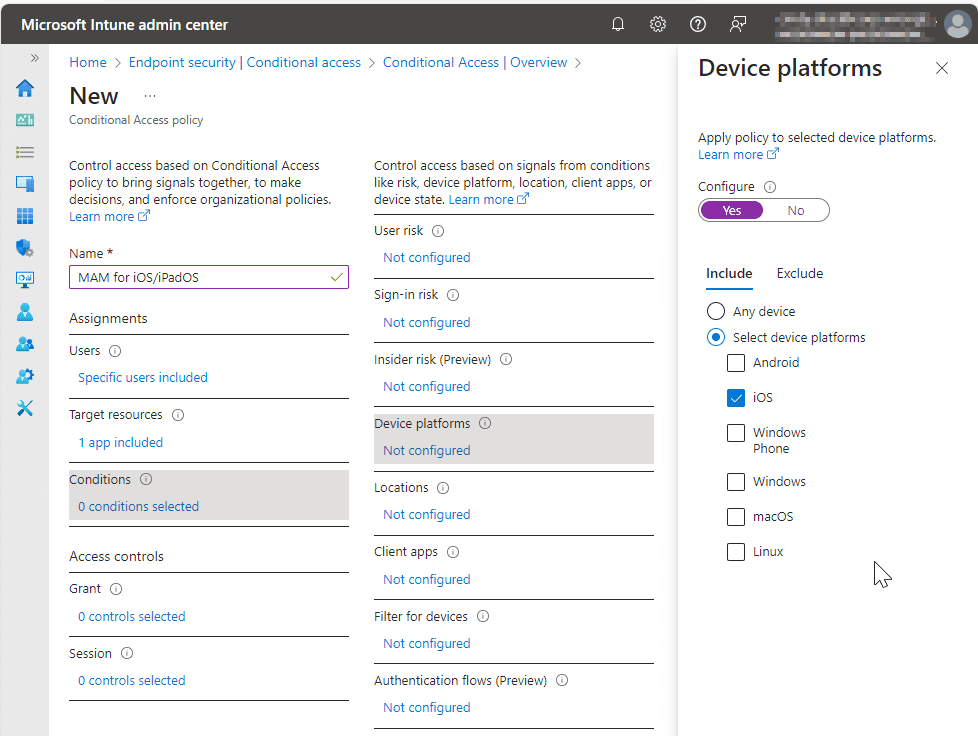
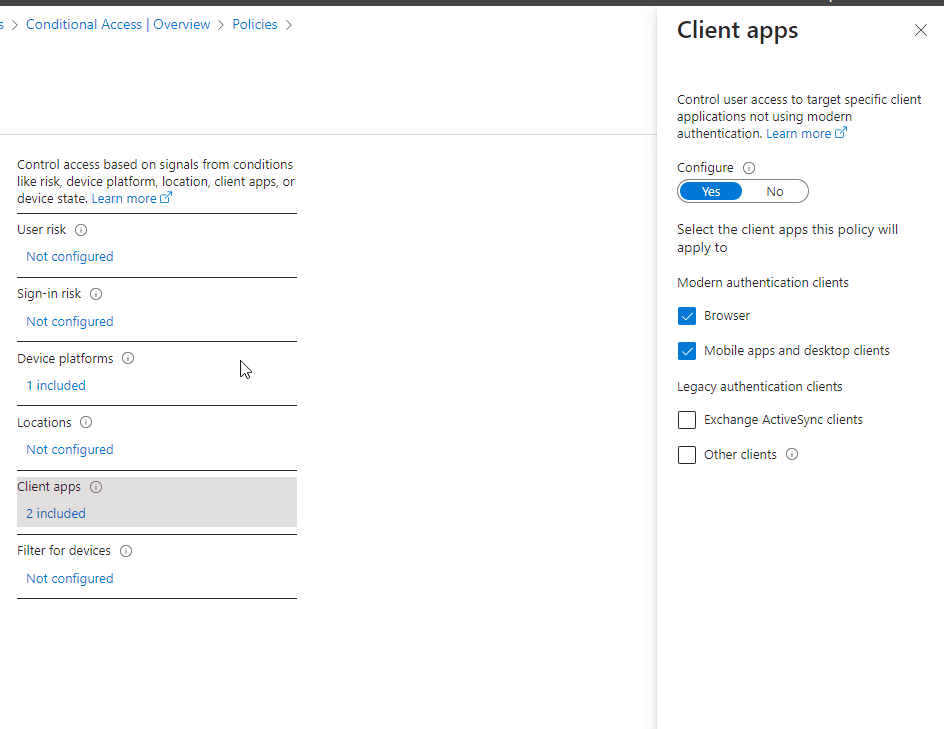
Under Client apps, select both Browser and Mobile apps and desktop clients.
Defining Access Controls
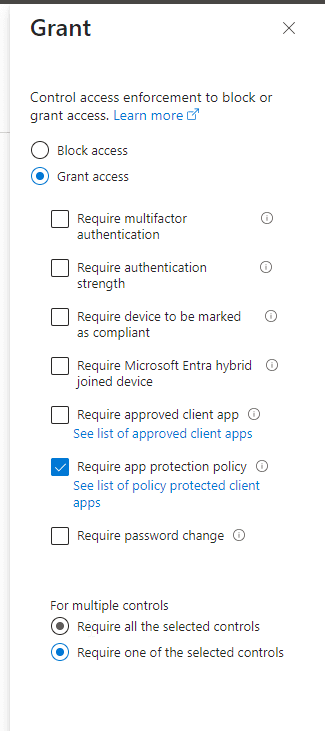
Next, go down to Access Controls and specify the requirements to get access. I have chosen Grant access by Requiring app protection policies to be in place.
Crafting Your App Protection Policy
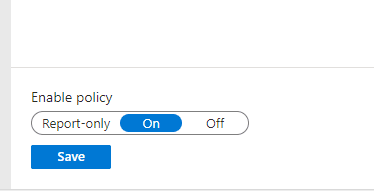
Activate the policy by setting the toggle to On, then click Save.
Go to the Intune Admin Center > click on Apps > App protection policies > + Create policy > iOS
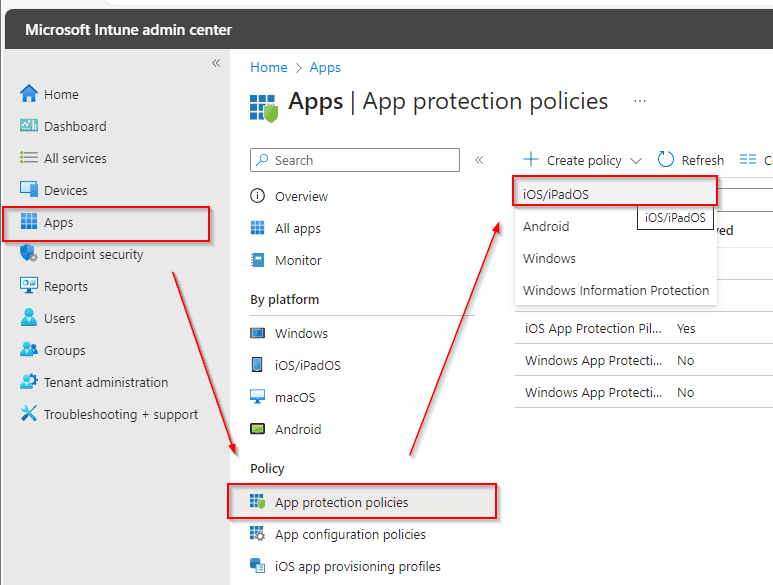
Navigating to Policy Configuration
On the ‘Create Policy’ page, give your policy a name and a description to clarify its purpose, then click ‘Next’.
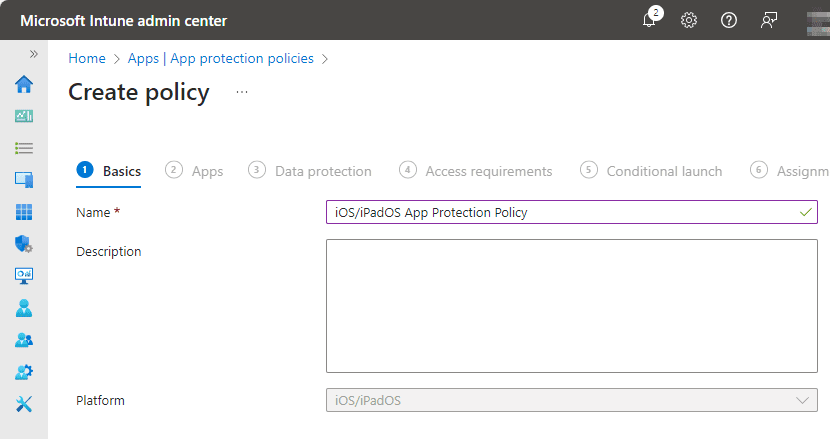
Specifying Apps and Data Transfer Restrictions
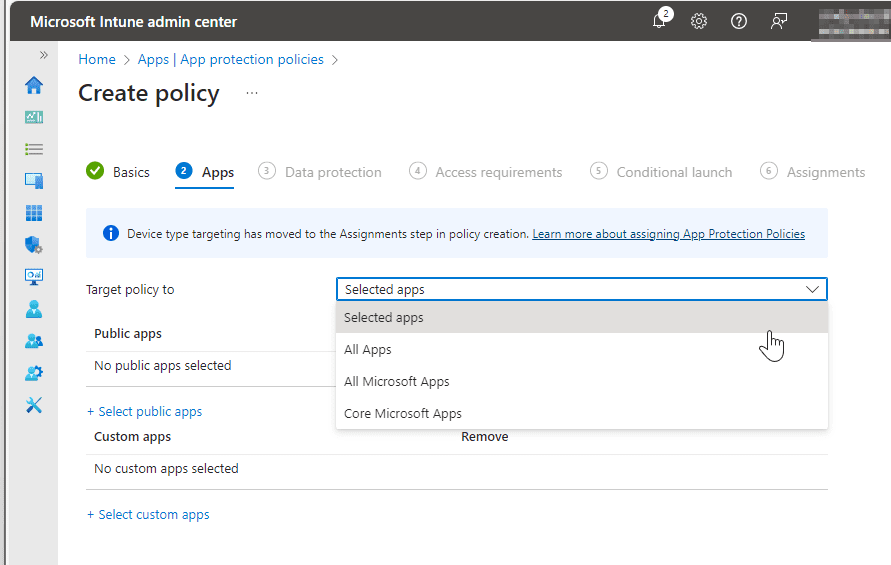
In the following section, we will select what applications we want to target with the App Protection Policies.
Public Apps
- All Apps – This would target policy to all Microsoft and partner apps that have Intune SDK setup
- All Microsoft Apps – This target all Microsoft apps that have Intune SDK setup
- Core Microsoft Apps – This includes these apps: MS Edge, Excel, Office, OneDrive, OneNote, Outlook, PowerPoint, SharePoint, Teams, To Do and Word.
If you don’t select an option from the dropdown menu, you can choose to target single apps by using Selected Apps and click + Select public apps to choose your app.
If you also don’t select any of the predefined groups as mentioned above, you can also select + Custom apps to target a custom app from its Bundle ID.
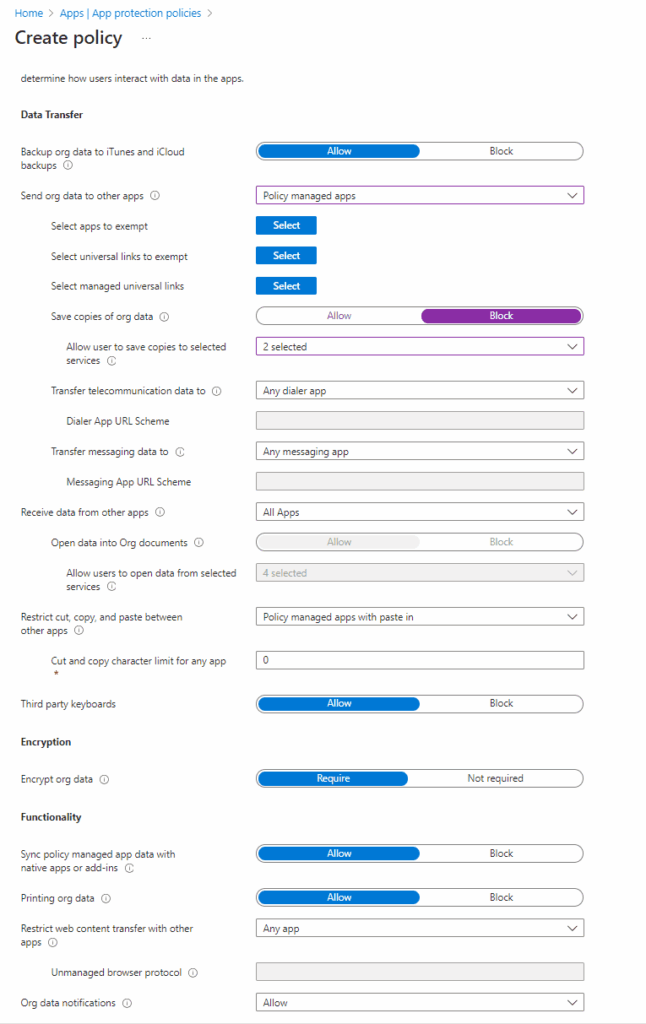
Data Transfer Restrictions
Next, we will create policies to control actions like cutting, copying, paste, as well as other restrictions.
Below, I’ve outlined my policy choices. Here I will highlight a few and why I made these choices.
- Backup org data to iTunes and iCloud Backup: Set to block to prevent data leaks. I want to avoid storing sensitive work or school data in iCloud backup services.
- Save copies of org data: Set to Block to disallow saving sensitive data on unmanaged resources. I do not want to allow users to save potential sensitive data on unmanaged resources, but I will allow users to save org data on managed services like SharePoint and OneDrive.
- Restrict cut, copy, and paste between other apps: Allow only for managed apps, with paste-in enabled. This helps mitigate the risk of users copying sensitive information on unsupported platforms.
Setting Encryption and Functionality Parameters
Require encryption of org data on all devices accessing org data on this app.
Here I went ahead and Blocked the Sync policy managed app data apps or add ins so that we are consistent with keeping org data contained and not intermixed. I also Blocked Printing org data to keep org data from leaving unmanaged platforms.
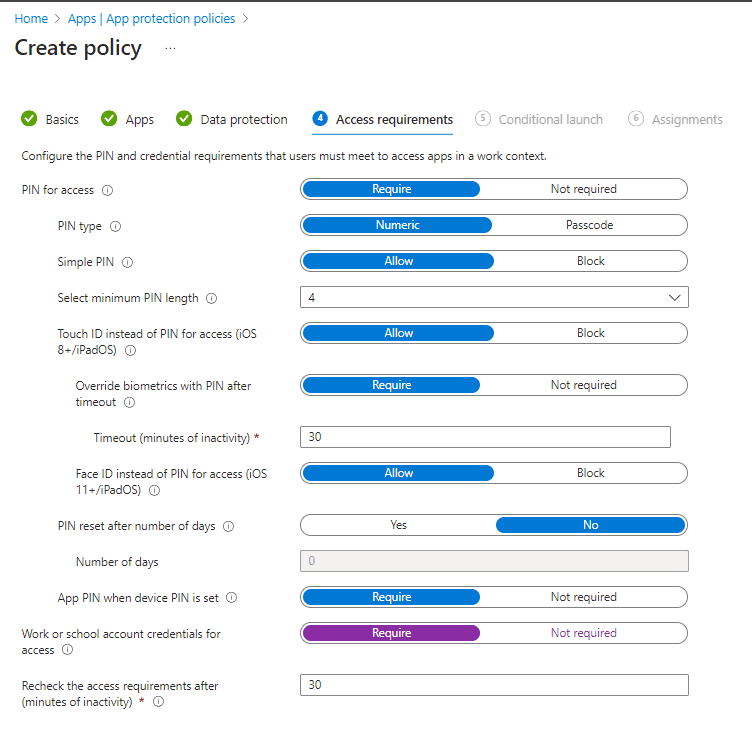
Establishing Access Requirements and Conditional Launch Settings
In this section, we establish rules governing user access to apps. I did keep the defaults, which require a PIN to access the apps. The PIN is set at the device level so if a user does not have a PIN enabled, they will not be able to access apps. I am also requiring an app pin to access a resource such as Outlook for an extra layer of protection, along with requiring users to use work or school credentials for access. Once set, click ‘next’.
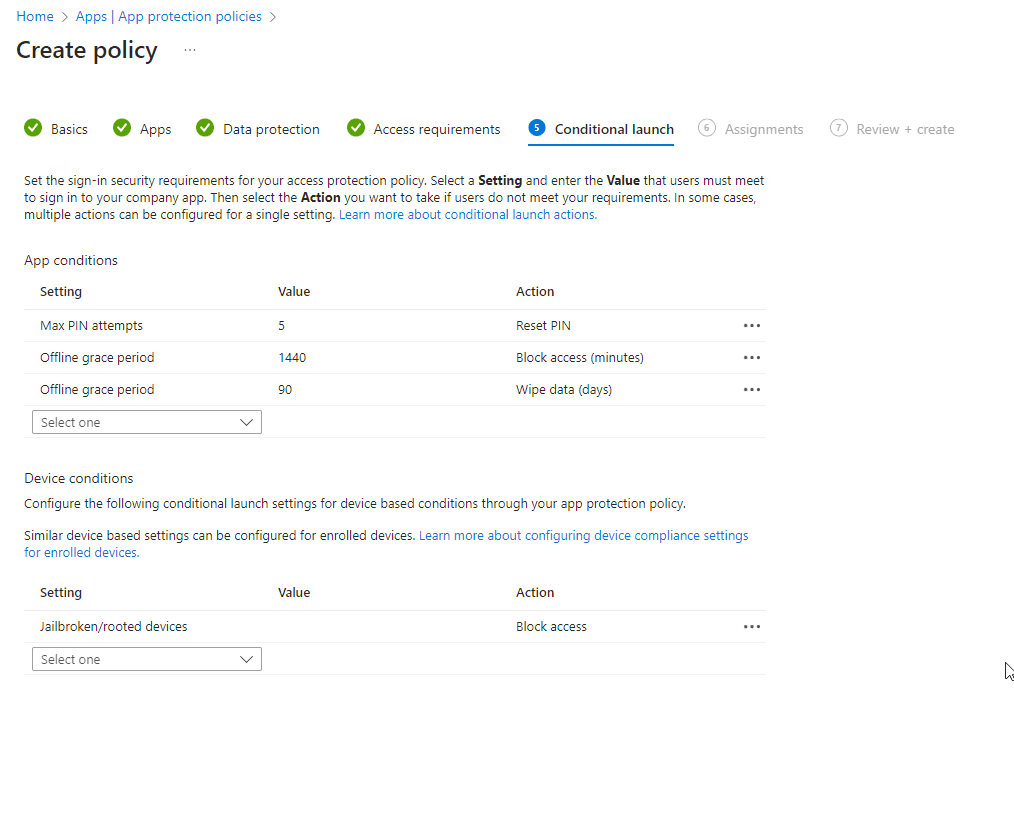
Conditional Launch
Here we set requirements for our App and Device conditions. We can also set actions. For example, if a device is detected as “Jailbroken” or “Rooted” it will Block access to the org’s application. I did not make any changes, keeping to the defaults. Click Next.
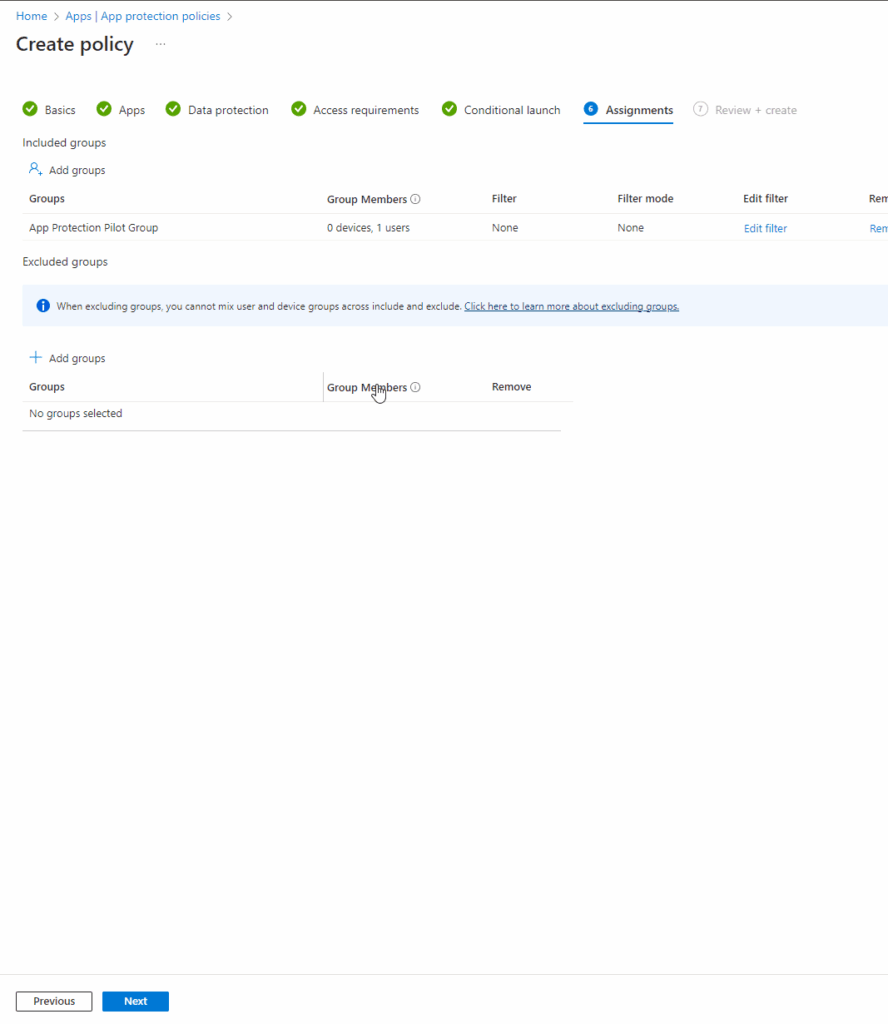
Go ahead and select your Assignments. I chose the App Protection Pilot Group to keep things consistent.
Review and then create your App Protection Policy once you have verified this meets your needs.
Testing and Implementing Your MAM Strategy
Go to unmanaged iOS device > go to Microsoft Word.
You’ll need to register our iOS device so that we can get policies applied to the application.
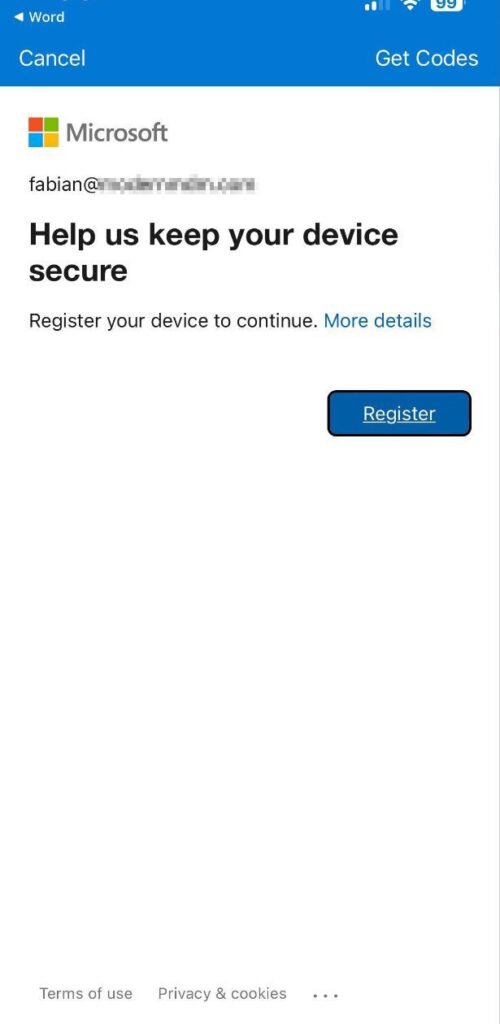
The device is getting policies applied from your App Protection Policy and will close.
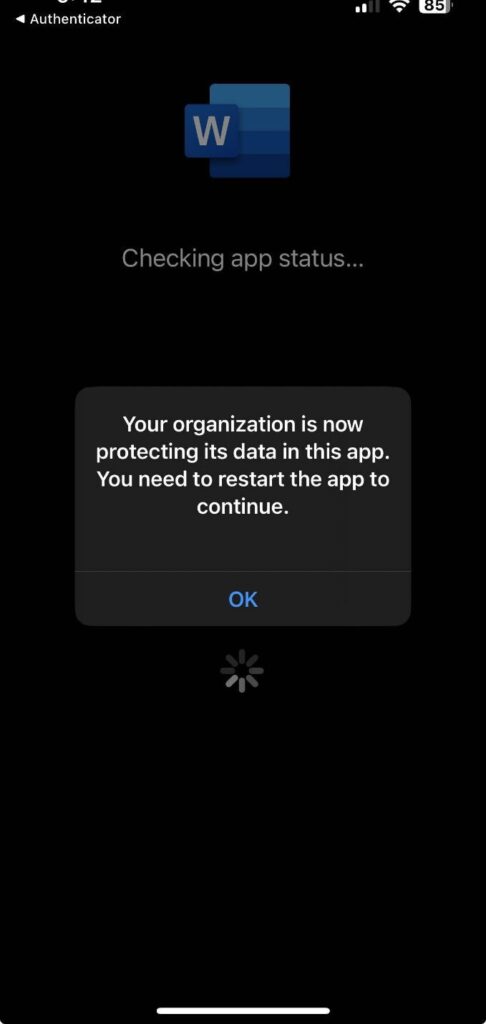
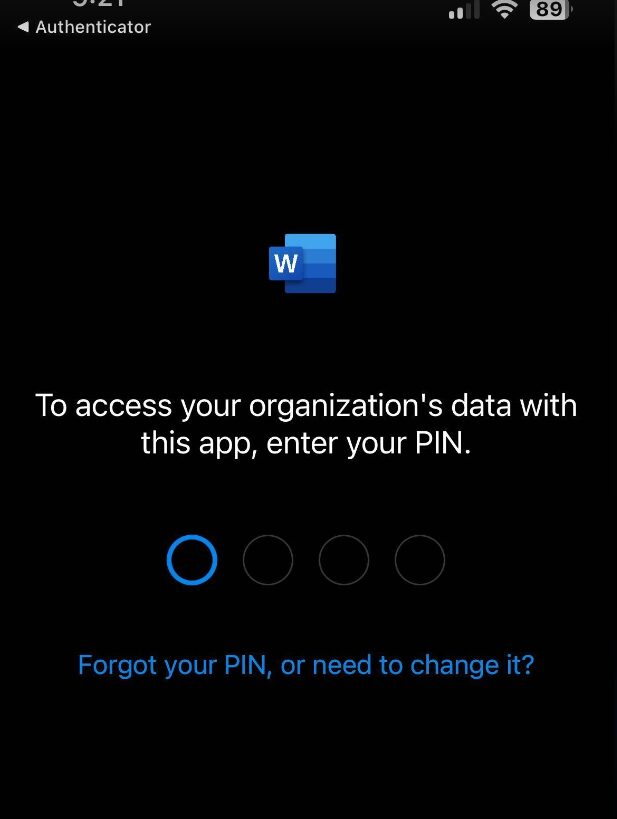
In our policy we require an App PIN to access the application. Go ahead and set your PIN to move forward.
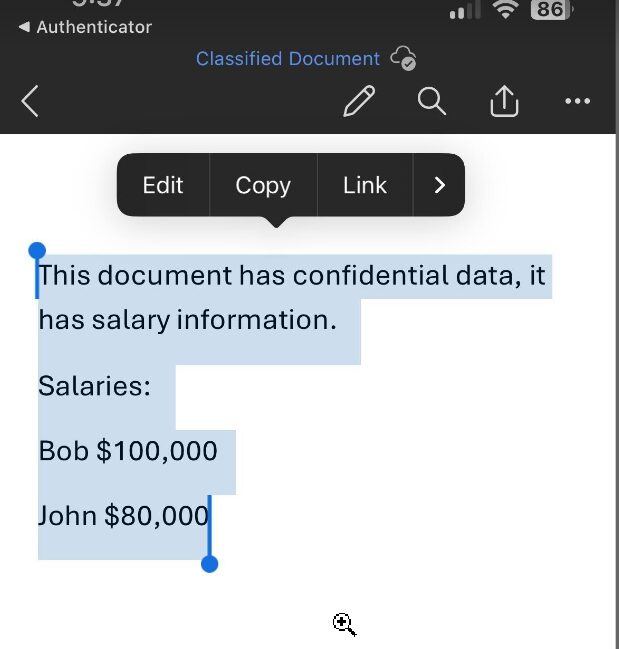
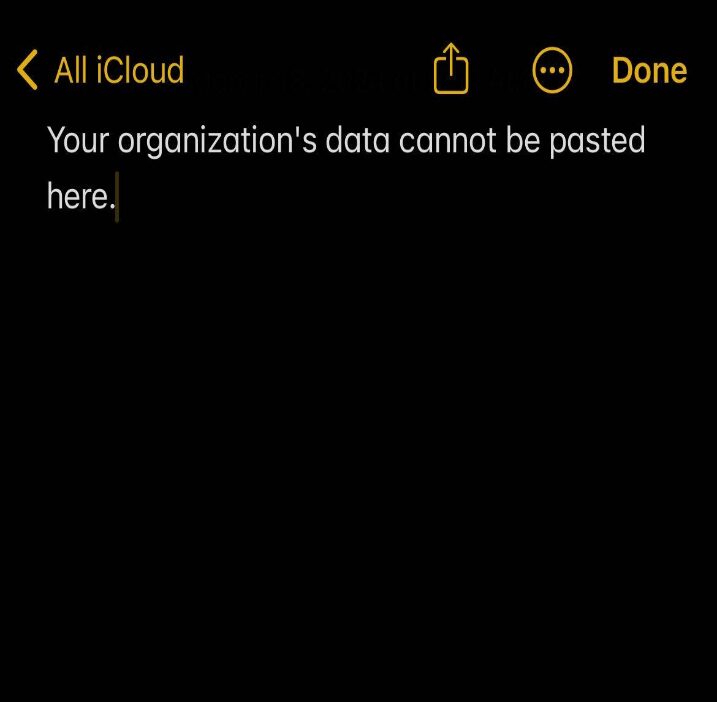
Now that I have access to Microsoft Word on my unmanaged device, I’m going to copy data on a company document and try to paste it into an unmanaged notepad on my iOS device. As you see, we are not able to paste company data on to a personal device.
Complete: Set Up of MAM for iOS Devices with Intune
Following these steps will secure your organization’s data on unmanaged iOS devices, leveraging the power of MAM and App Protection Policies in Intune.


