- What are the total supported systems?
Privilege Manager supports Windows servers and workstations, work group computers, domain joined computers, hybrid joined computers and, Azure AD joined computers.
- Does Privilege Manager keep a log on what the admin rights have been used for?
For data protection reasons, this information is not recorded. Privilege Manager’s operating logic is based on the idea that when a user knows their use of admin rights is being controlled, one way or another, the threshold for misuse is high enough. However, the administrator can check the log for when the admin rights have been activated for use.
- Can you configure a temporary admin right for a domain ID?
Yes
- Can you limit the temporary access rights to the user’s own device?
Yes
- Does Privilege Manager work without internet connection?
You can use an activation key offline, without connection to the organization’s internal network. However, a user cannot create an activation key offline, and needs to request it from the help desk, if they need it when they are offline. To run any new rules for the devices, the devices need to be connected to the organization’s internal network. You can also configure Privilege Manager to work only with internet connection.
- Can you use Privilege Manager to manage devices linked to Azure AD?
Yes, you can, but when doing so, you can only manage them device-specific and not in groups.
- What does Privilege Manager require from the users’ workstations?
Microsoft-supported versions of the Windows operating system + NET Framework 4.x.
- What kind of infrastructure does Privilege Manager require?
Privilege Manager works in Microsoft environment on Windows devices. For devices in their own Active Directory, you can use the AD’s structures to align your Privilege Manager rules. For other devices, we can create custom device-specific rules. Platform-wise, Privilege Manager requires a Microsoft Server and a Microsoft SQL Server software – and the free Express version is sufficient.
- Do I need to have ConfigMgr to subscribe to or use Privilege Manager?
No, ConfigMgr is not required.
- Can we get a trial of Privilege Manager?
At this time, we currently do not offer a trial, but you can contact us here for a demo.

RIGHT CLICK TOOLS ADD-ON: PRIVILEGE MANAGER
The Privileged Access Management Solution You Need
Our Privileged Access Management (PAM) solution enables tighter security policies for all devices and streamlined workflows. Right Click Tools Privileged Access offers simple, secure, and centralized access rights management.
Right Click Tools Privileged Access Features

Privileged Access Makes Zero Trust Workable without Compromising the Enterprise
Experts estimate that 90 percent of all Windows vulnerabilities could be made impossible to exploit by getting rid of unnecessary admin rights. With our PAM solution, you can allow end-user self-service without compromising security.
Zero trust security is the most comprehensive way to protect your enterprise. But it can often leave less-privileged users without the access they need and burden your IT team with additional work. Now there’s a way to provide users with secure, temporary admin rights to perform just the specific tasks you wish to allow.
Take the leap towards a zero trust security environment. With our Privileged Access Management tools, you can easily grant temporary admin rights and improve security for your entire enterprise. Plus, you can get reports on how many local admins are on each endpoint machine.
Privileged Access, a PAM Solution, Offers Many Benefits:
Increased Security– by removing any excess permissions, Privileged Access keeps users from getting themselves into trouble by installing unapproved software or clicking something they shouldn’t. Avoiding these pitfalls saves you time, money, and headaches. Even more reasons why your enterprise needs Privileged Access Management tools to create a zero-trust environment.
Improved User Productivity– by not having to wait for a simple task to be authorized by a Service Desk, users no longer need to wait and can continue to work on the task at hand. That’s just one more way our PAM services ultimately improve user productivity.
Decreased Service Desk Tickets– Privileged Access Management services reduce the need for service desk. Most users will no longer need to submit a service desk ticket when they’re safely given the access they need – just for the tasks they’re allowed.
Faster Equipment Deployment-with predefined user profiles, they can be applied to machines across the enterprise. Our PAM solution reduces the burden of creating them one by one and applying each profile individually.
System Requirements
See the Top Reasons to Add On Privileged Access
Privileged Access Features Overview
User Privileges
Take control of user privileges – all in one place. Privileged Access lets you grant and view end-user privileges across your entire environment. Now you can streamline permission requests while keeping your security intact.
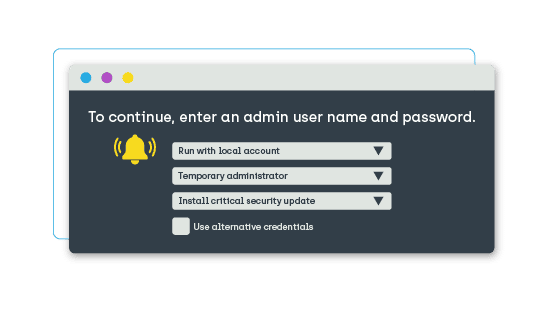
Self-Service
Securely allowing users to perform tasks that usually require a help desk ticket not only frees up your help desk from tedious tasks, it also improves the end user experience across your enterprise. Privilege manager can give users the self-service independence they deserve.
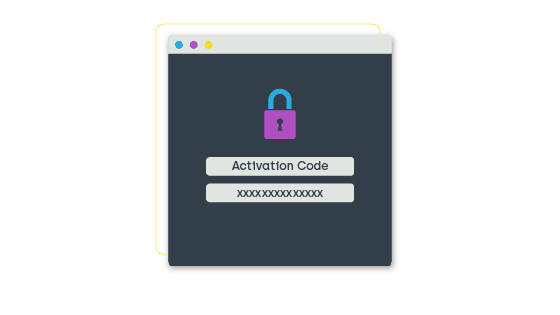
Access Code
If a user needs to install a piece of software, for example, the help desk can grant them a single-use activation code through Privilege Manager. This allows the user to download and complete the installation quickly and at their convenience. It also provides direct reporting to the IT team on when and why the software was installed.
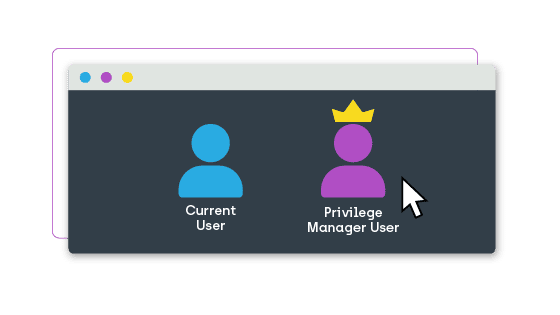
Alternate User IDs
Privileged Access can also provide users with a user ID different than their own that has a set of predetermined access privileges. This allows for the completion of a selected set of tasks with no disruption to their existing privileges, saving the help desk time and getting the end user back into action faster.
Current User IDs (online only)
If the user ID is part of a specific domain, access can be provided through their current user ID. To complete tasks through this method, the user device must be online.
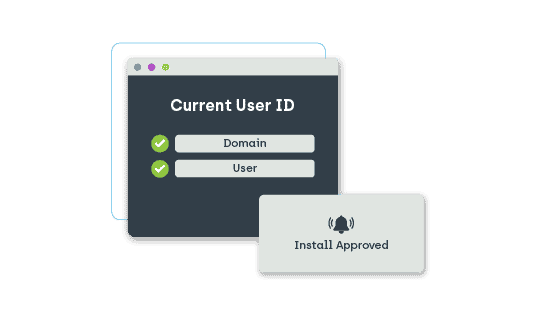
ID Management
Creating and deploying consistent user IDs and groups at scale is a slow and error-prone process. This could leave glaring holes in your enterprise security. Privilege Manager streamlines your ID management, giving you complete control. Leave nothing to chance while improving your overall IT security and efficiency.
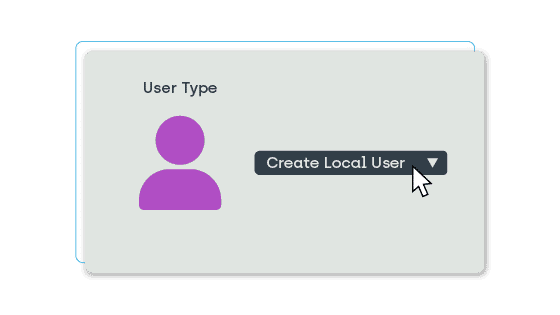
User ID Creation
Privileged Access gives you incredible flexibility in the creation of local user IDs and groups. Whether you are using the structure of your existing Active Directory or predefined rules and permissions, using a specific device type or configuring domain-specific IDs and group rules on the domain level, Privilege Manager has it covered for all these instances and more.
Password Management
Privilege Manager is focused on empowering your help desk to accomplish more while being safe and secure. Your team can use a Privilege Manager created local admin account and password to install software, troubleshoot or whatever is needed to help resolve the ticket.

Group Management
Creating, managing, and scheduling user groups across environments is tedious. Privileged Access makes it all possible, quickly and easily, all while increasing your overall security.
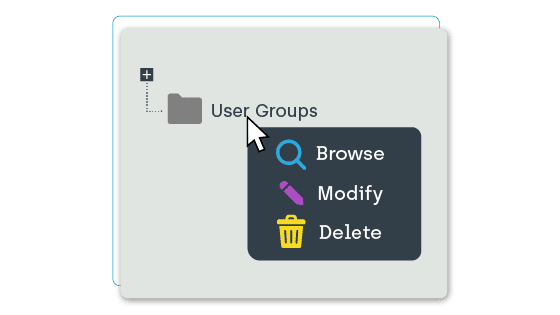
Managing Group Members
Adding or removing members to and from a group based on rules has never been easier. Privilege Manager enables techs to manage group membership at will. They can also provide temporary, specific privileges that allow users to complete certain tasks, while not giving the user unlimited rights.
Creating Groups
Group creation can be done in a snap by using predefined rules. These rules ensure each member has the correct permissions for what they need and when they need it. Privilege Manager provides enhanced flexibility in almost any environment.
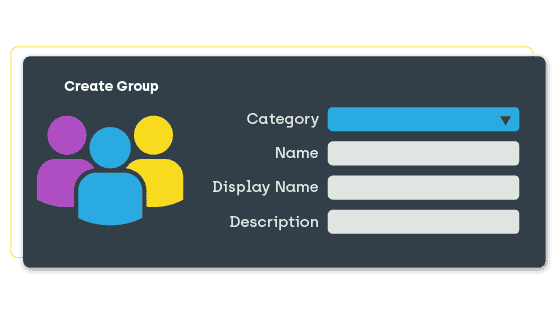
Scheduling Group Membership
With Privileged Access, group membership can be automatically scheduled. Allowing users to join a group membership to accomplish the task they need within a pre-determined time frame. Then, that particular user can be automatically removed from that group, maintaining the integrity of the environment’s security.
Reporting
With Privileged Access’s reporting capabilities, you will have full visibility into exactly which employees and devices have certain types of permissions. Reports also provide data on users who have requested passwords. Beyond our preset reports, custom reporting allows you to create reports that slice and dice the data as you see fit.
Group Rules Reporting
Easily look in a single list or search to see which group management rules have been created in Privileged Access. Also see which group rules have been applied to specific groups.
User Rules Reports
Know which user rules have been created in Privileged Access. See all user rules in a single list, search user rules for specific devices, or see user rules applied to a specific organization group.

Computer Reports
Quickly see which devices have the Privileged Access client installed. This will also show the local groups and local users on the specific computer even if Privilege Manager is not actively managing the groups or users.
Temporary User IDs
Increase security by seeing which users can use temporary user IDs. Also discover how often the Temporary User ID has been used and quickly see what the reason for the request was for.
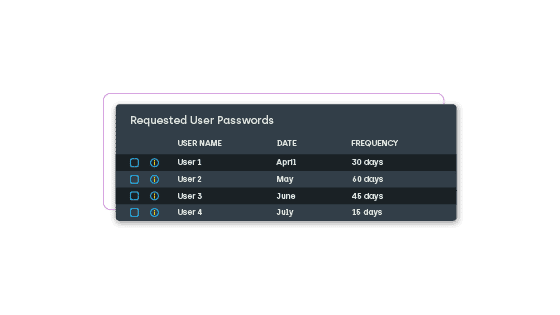
Password Reporting
Add another layer of protection by gaining insight into which users have requested passwords for specific devices. Reports detail the dates, times, and frequency of password requests.
Ready to learn more?
Contact us today to get a quote for any of our endpoint management, application management, and privilege management software solutions!
PRIVILEGE MANAGER